Method and device for determining memory exception, equipment and storage medium
A memory and exception technology, applied in response to error generation, non-redundancy-based fault handling, instrumentation, etc., can solve problems such as undetermined memory exceptions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
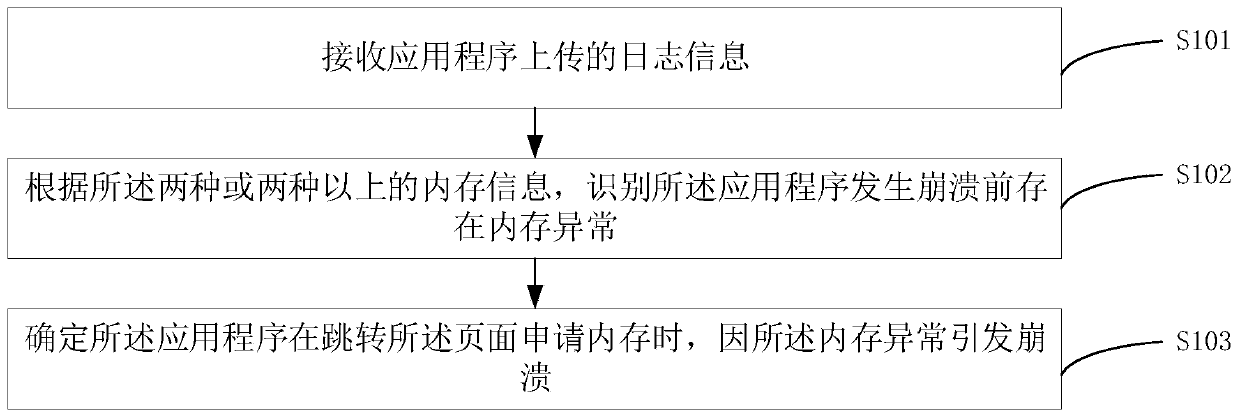
[0089] figure 1 It is a flow chart of a method for determining memory abnormality provided by Embodiment 1 of the present invention. This embodiment is suitable for receiving log information uploaded by an application program, and identifying memory exceptions before the application program crashes according to the log information. The method can be executed by a device for determining memory abnormality, and the device can be implemented by software and / or hardware. It can be configured in computer equipment, such as servers, workstations, personal computers, etc., and the method specifically includes the following steps:
[0090] S101. Receive log information uploaded by an application program.
[0091] In computers, log information is a file that records events that occur during the operation of an operating system or other software, or messages between different users of communicating software. Log information records events that occur during the execution of the system...
Embodiment 2
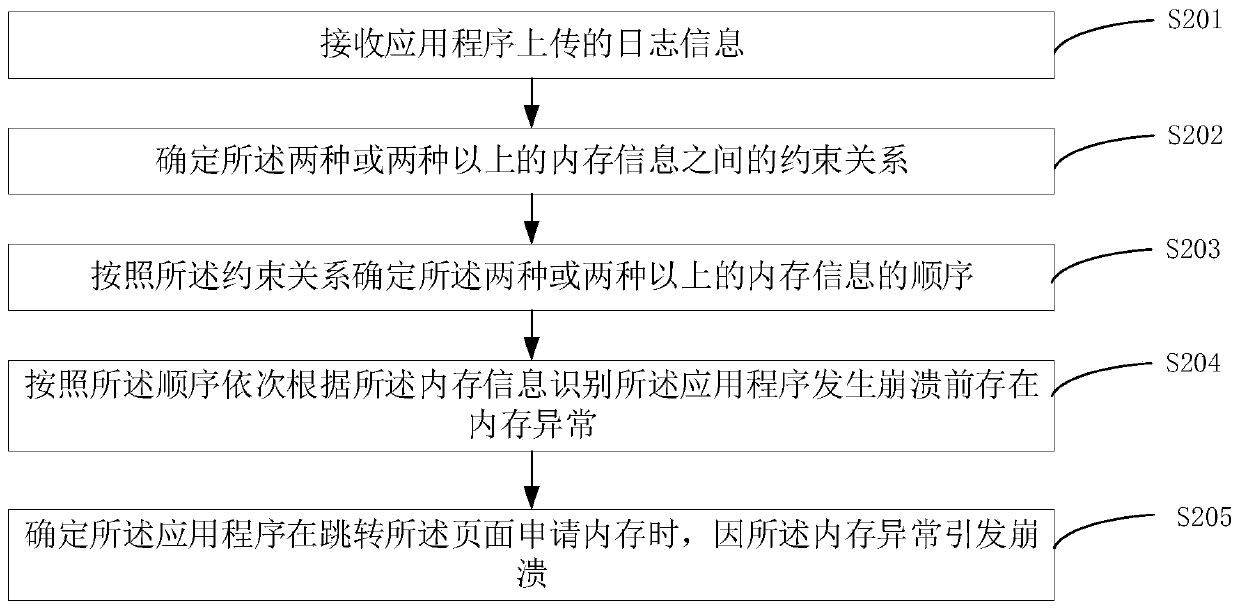
[0113] figure 2 It is a flowchart of a method for determining memory abnormality provided by Embodiment 2 of the present invention. This embodiment is refined on the basis of the first embodiment, and describes the specific steps of identifying memory exceptions before the application program crashes according to two or more types of memory information. The method specifically includes the following steps:
[0114] S201. Receive log information uploaded by an application program.
[0115] Generally, the log information includes the page when the application program crashes, and two or more types of memory information before the application program crashes.
[0116] S202. Determine a constraint relationship between the two or more types of memory information.
[0117] In general, each memory message is used to identify a memory exception. Memory information includes: heap memory information, resident memory information and virtual memory information. Memory exceptions inclu...
Embodiment 3
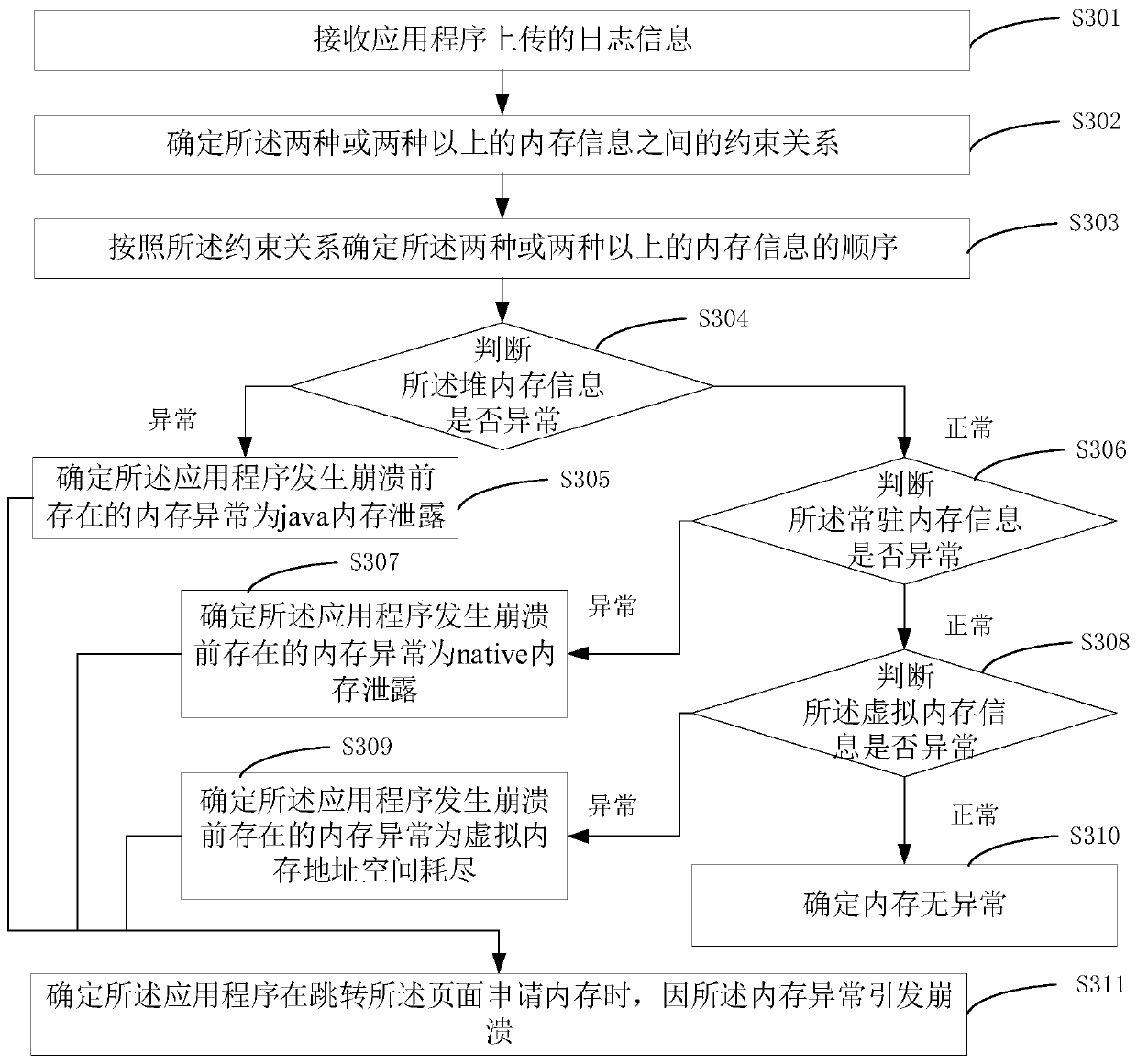
[0133] image 3 It is a flow chart of a method for determining memory abnormality provided by Embodiment 3 of the present invention. This embodiment is refined on the basis of Embodiment 1 and Embodiment 2, and describes the order of determining the two or more types of memory information according to the constraint relationship, and the specific steps for judging memory abnormality according to the order . The method specifically includes the following steps:
[0134] S301. Receive log information uploaded by an application program.
[0135] The log information includes a page when the application program crashes, and two or more types of memory information before the application program crashes.
[0136] S302. Determine a constraint relationship between the two or more types of memory information.
[0137] The memory information includes: heap memory information, resident memory information and virtual memory information, the heap memory information is used to identify j...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap