Wireless sensor network source position safety route design method based on irregular ring
A wireless sensor and irregular technology, applied in specific environment-based services, wireless communications, data exchange networks, etc., can solve the problems of multiple energy, large energy consumption, low efficiency of protecting source nodes, etc., and achieve the effect of effective privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
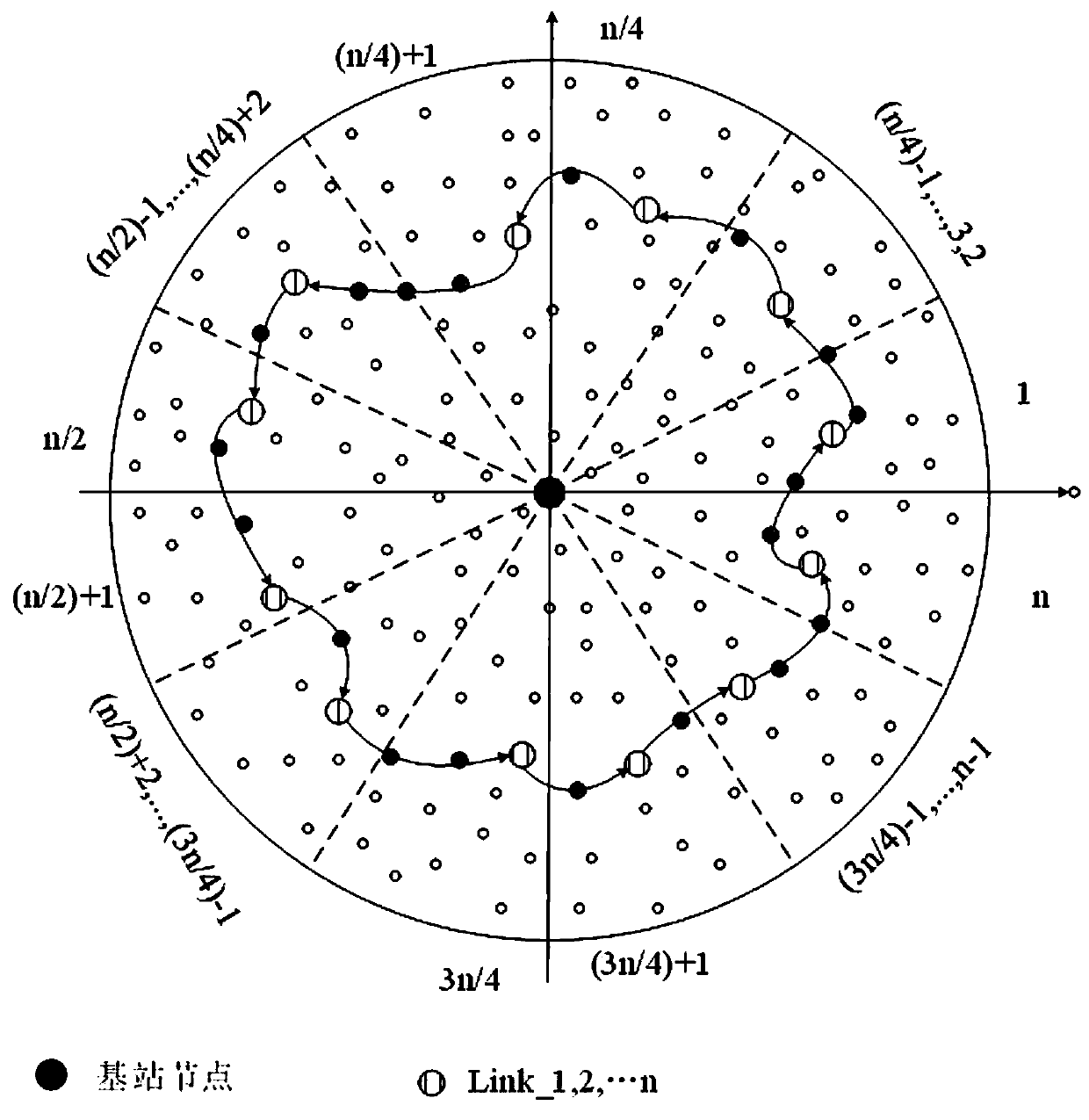
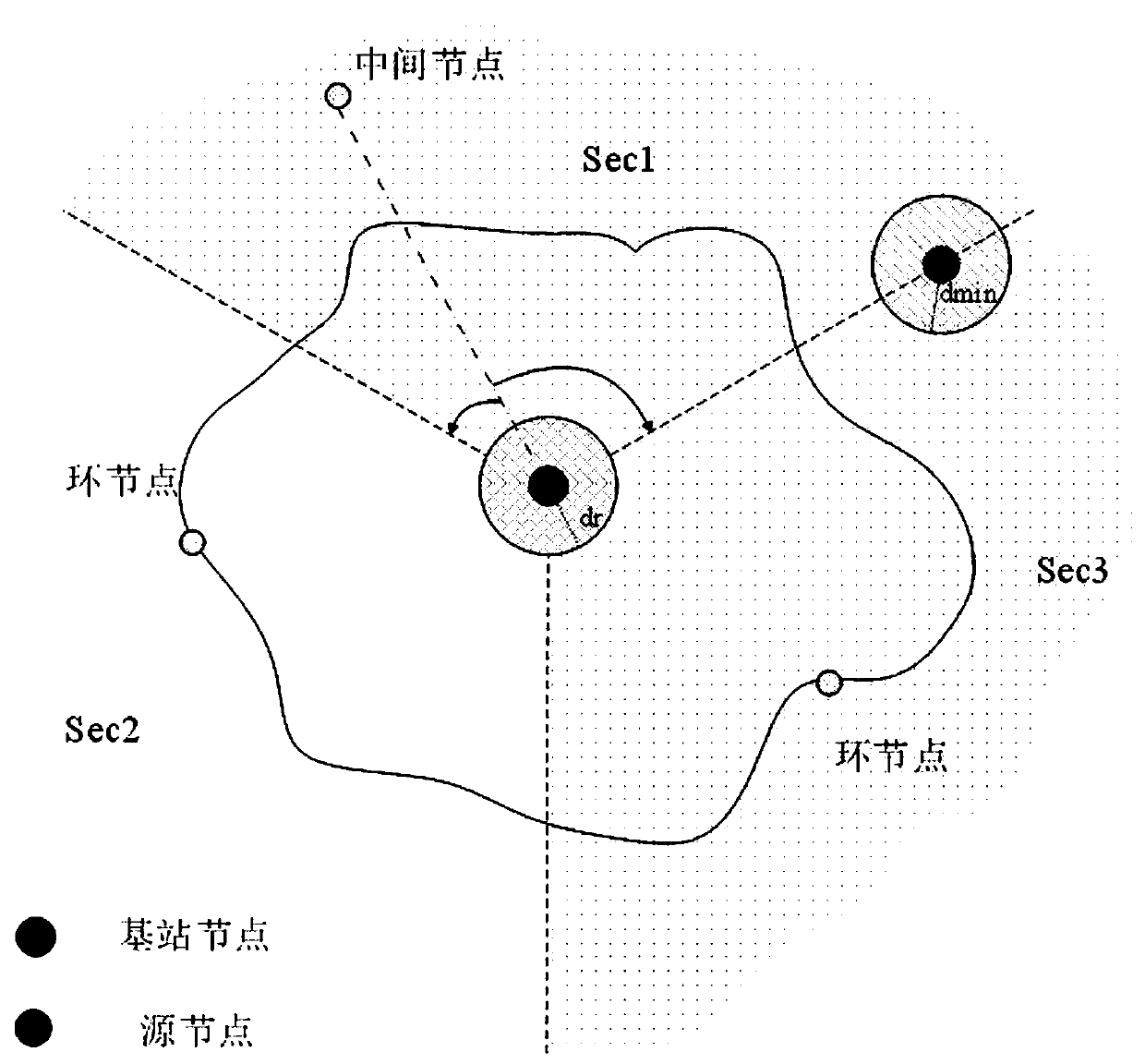
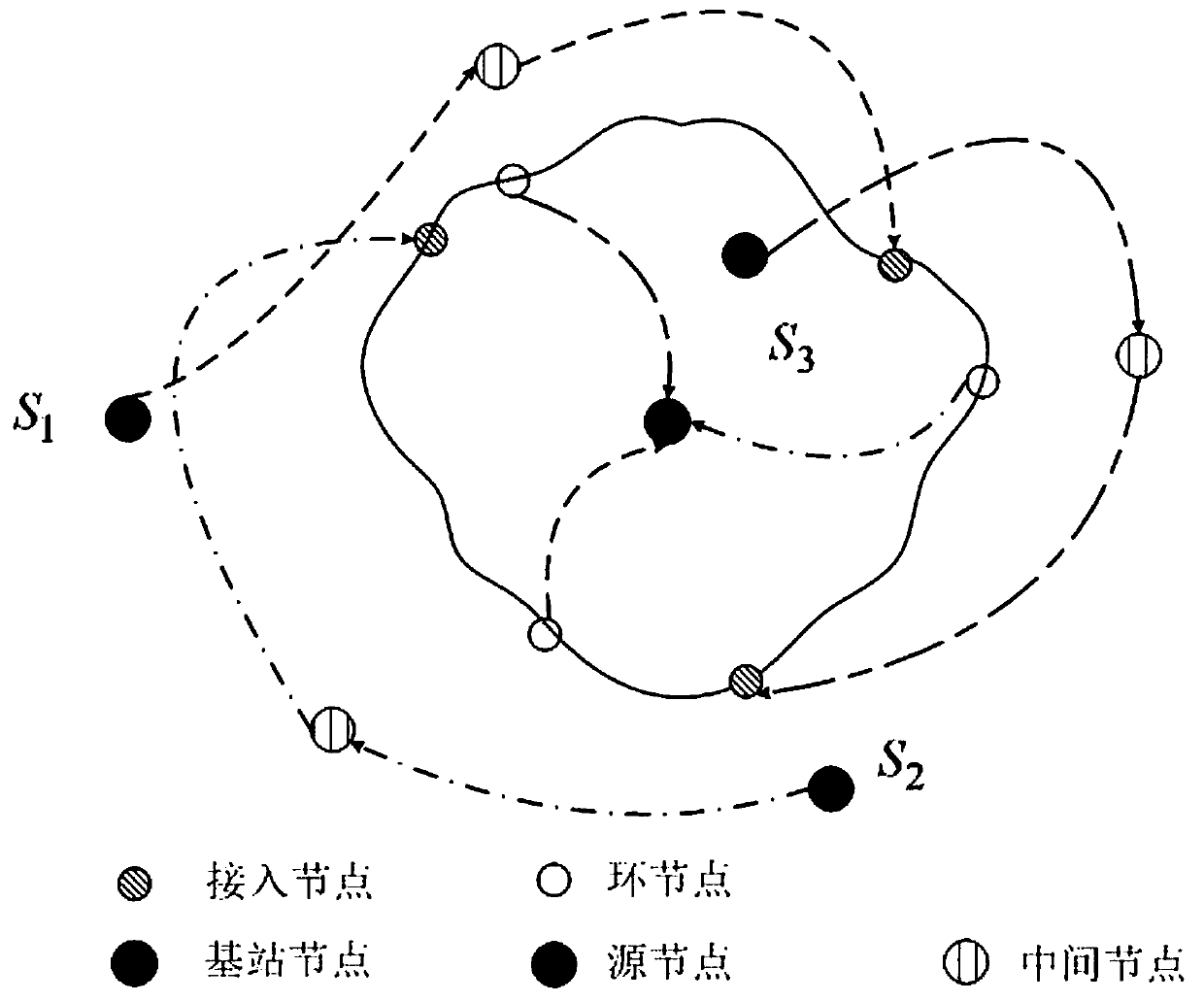
[0057] A method for designing secure routing of a source location in a wireless sensor network based on an irregular ring, comprising the following steps:
[0058] 1) Define the network model: the wireless sensor network model is composed of a base station node, namely the BS node, and N sensor nodes. When the sensor node perceives the monitoring object, it collects data and sends it to the base station BS node. The sensor node is called the source node SN, assuming When the source node in the network cannot monitor the monitored object for a period of time, the source node stops sending data packets, and the network model satisfies the following conditions:
[0059] 1-1) The sensor nodes in the network are evenly distributed, and the sensor nodes are isomorphic, that is, the sensor nodes have the same configuration, and the computing power, storage and energy consumption resources of each sensor node are the same;
[0060] 1-2) The base station node is the only final destinat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com