A computer data encryption system and method
A data encryption, computer technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
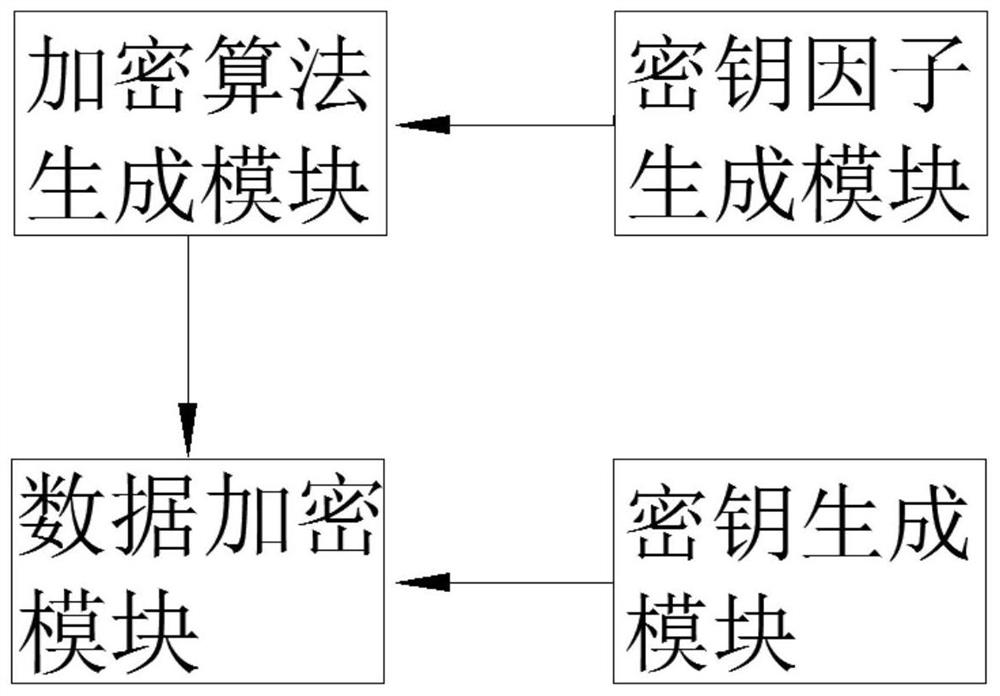
[0036] like figure 1 As shown, the present invention also provides a computer data encryption system, which includes: a key factor generation module, an encryption algorithm generation module, a key generation module and a data encryption module.
[0037] A key factor generating module, configured to generate a corresponding first key factor and a second key factor, and a third key factor for generating a prime number according to a computer login account number and password;
[0038] Encryption algorithm generating module, for determining the elliptic curve Ep(X according to the first key factor, the second key factor and the third key factor n ,Y n ), where X n is the first key factor, Y n is the second key factor, p is the third key factor;
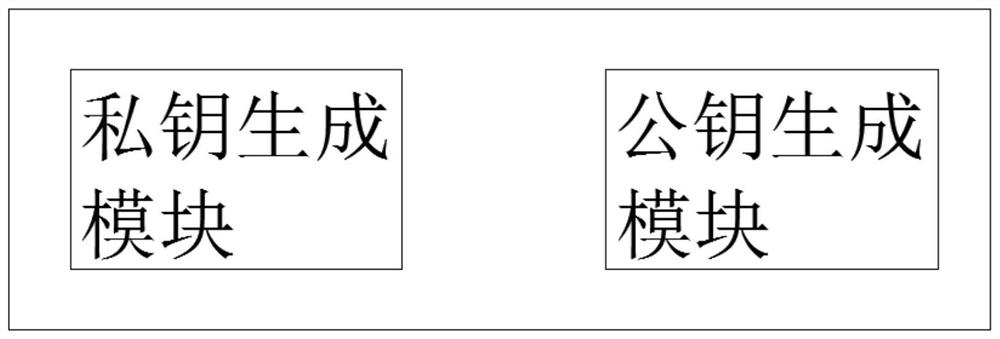
[0039] Key generation module, used to generate a private key Z n , take the elliptic curve Ep(X n ,Yn ) as the base point G, according to the private key Z n And base point G generates public key Q=Z n G;
[0040] Data encrypt...
Embodiment 2
[0057] Such as figure 1 As shown, the present invention also provides a computer data encryption system, which includes: a key factor generation module, an encryption algorithm generation module, a key generation module and a data encryption module.
[0058] A key factor generating module, configured to generate a corresponding first key factor and a second key factor, and a third key factor for generating a prime number according to a computer login account number and password;
[0059] Encryption algorithm generating module, for determining the elliptic curve Ep(X according to the first key factor, the second key factor and the third key factor n ,Y n ), where X n is the first key factor, Y n is the second key factor, p is the third key factor;
[0060] Key generation module, used to generate a private key Z n , take the elliptic curve Ep(X n ,Y n ) as the base point G, according to the private key Z n And base point G generates public key Q=Z n G;
[0061] Data en...
Embodiment 3
[0075] like figure 1 As shown, the present invention also provides a computer data encryption system, which includes: a key factor generation module, an encryption algorithm generation module, a key generation module and a data encryption module.
[0076] A key factor generating module, configured to generate a corresponding first key factor and a second key factor, and a third key factor for generating a prime number according to a computer login account number and password;
[0077] Encryption algorithm generating module, for determining the elliptic curve Ep(X according to the first key factor, the second key factor and the third key factor n ,Y n ), where X n is the first key factor, Y n is the second key factor, p is the third key factor;
[0078] Key generation module, used to generate a private key Z n , take the elliptic curve Ep(X n ,Y n ) as the base point G, according to the private key Z n And base point G generates public key Q=Z n G;
[0079] Data encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com