Data traceless deletion method and system based on NTFS file system
A file system and file technology, applied in the field of data security, can solve problems such as the inability to delete disk data quickly and without trace, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0038] The present embodiment provides the data traceless deletion method based on NTFS file system;
[0039] The method of data deletion without trace based on NTFS file system, including:
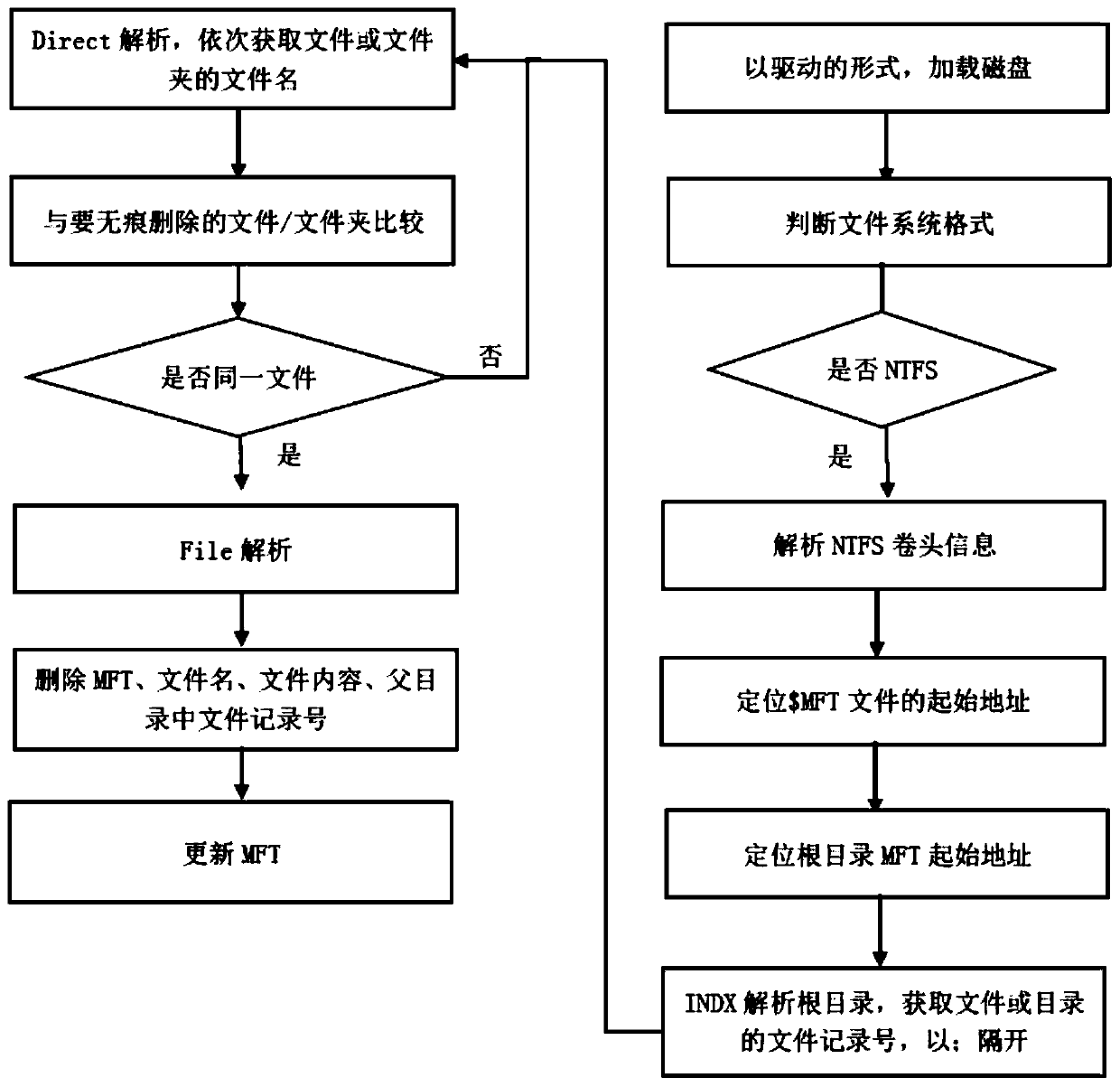
[0040] S101: read the NTFS volume header information; analyze the NTFS volume header information; locate the starting address of the $MFT file; locate the starting address of the MFT table of the root directory ($Root);
[0041] S102: According to the MFT table of the root directory, obtain the starting address of the file content of the root directory; analyze the root directory according to the starting address of the file content of the root directory, and obtain the file record numbers of folders and files under the root directory;
[0042] S103: According to the file record numbers of folders and files in the root directory, calculate the number of file record numbers, loop through the file names corresponding to the file record numbers in turn, and determine the file name correspond...
Embodiment 2
[0099] The present embodiment provides a data traceless deletion system based on the NTFS file system;
[0100] Data traceless deletion system based on NTFS file system, including:
[0101] The reading module is configured to: read NTFS volume header information; analyze the NTFS volume header information; locate the initial address of the $MFT file; locate the initial address of the MFT table of the root directory ($Root);
[0102] The parsing module is configured to: obtain the starting address of the root directory file content according to the MFT table of the root directory; analyze the root directory according to the starting address of the root directory file content, and obtain the folders and files in the root directory document record number;
[0103] The trace removal module is configured to: calculate the number of file record numbers according to the file record numbers of the folders and files in the root directory, loop through the file names corresponding to t...
Embodiment 3
[0108] This embodiment also provides an electronic device, including: one or more processors, one or more memories, and one or more computer programs; wherein, the processor is connected to the memory, and the one or more computer programs are programmed Stored in the memory, when the electronic device is running, the processor executes one or more computer programs stored in the memory, so that the electronic device executes the method described in Embodiment 1 above.
[0109] It should be understood that in this embodiment, the processor can be a central processing unit CPU, and the processor can also be other general-purpose processors, digital signal processors DSP, application specific integrated circuits ASIC, off-the-shelf programmable gate array FPGA or other programmable logic devices , discrete gate or transistor logic devices, discrete hardware components, etc. A general-purpose processor may be a microprocessor, or the processor may be any conventional processor, o...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap