Commercial data protection method and system based on supply chain management
A supply chain management and data protection technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problem of account information being threatened, and achieve the effect of safety and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
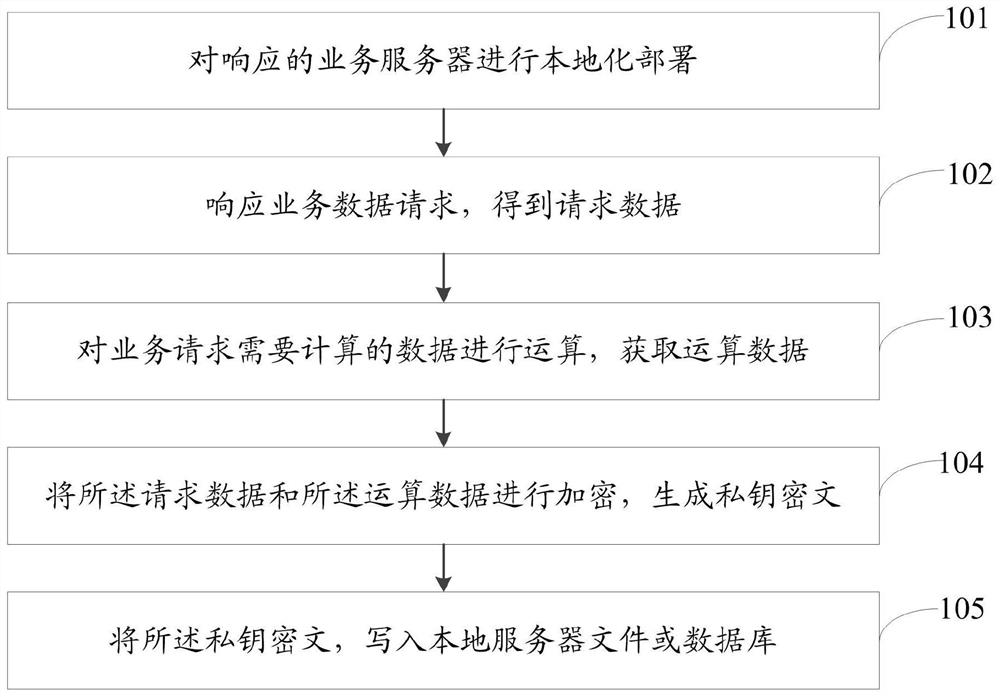
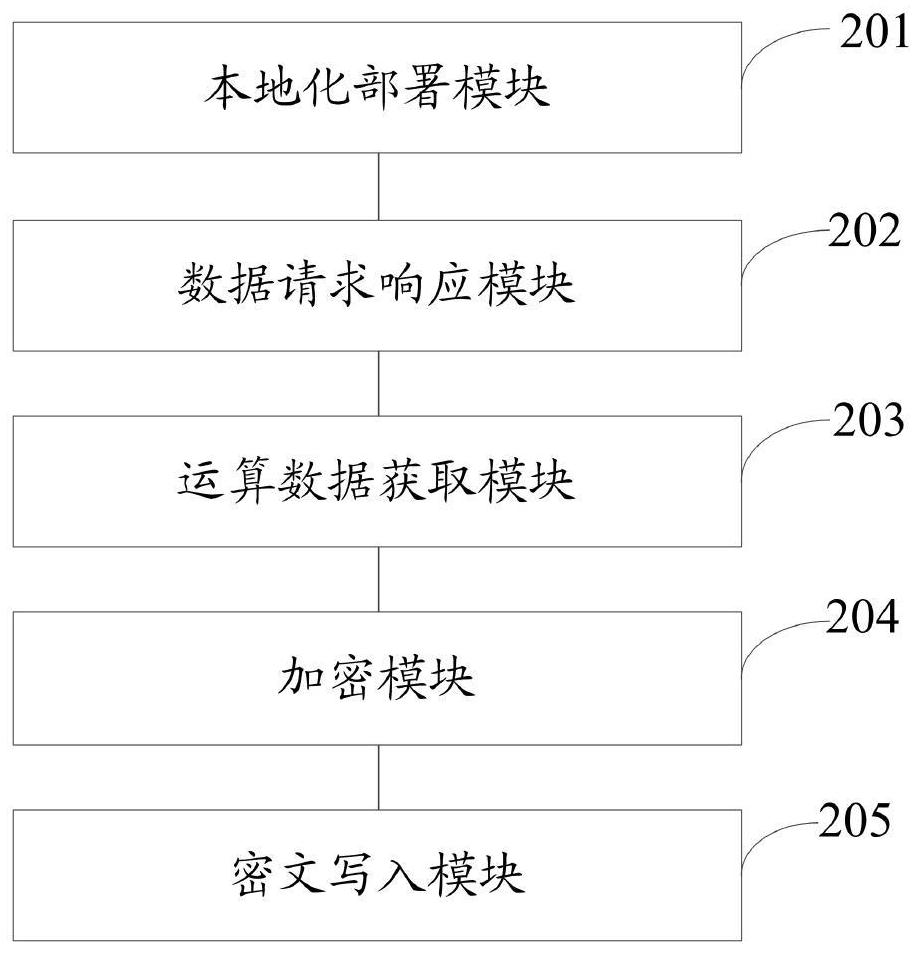
[0074] The data structure stored in the file in the embodiment of the present invention includes file header information (head), address information (address), file version information (vertion), account information (id), file generation time information (time), and data encryption technology identification information (DID); detailed as follows:
[0075] (1) Generation of private key and address:
[0076] (2) Encrypt the private key with a password to generate a key
[0077] (3) Write the corresponding string to the file:
[0078]
[0079] (4) Store the file on the local server.
[0080] (5) When a transaction request from a supply chain merchant is received, the file is parsed, the private key ciphertext and address are read from the file, and the ciphertext password is entered to decrypt the private key ciphertext before the transaction is performed.
[0081] The supply chain-based commercial data protection method and system provided by the present invention uses the generated priva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com