AMF based on MEC and identity authentication method, construction method and device thereof
An identity authentication and two-way authentication technology, applied in the field of mobile communications, can solve the problems of ineffective reduction of access authentication delay and inefficiency, and achieve the effect of avoiding network congestion and reducing signaling overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
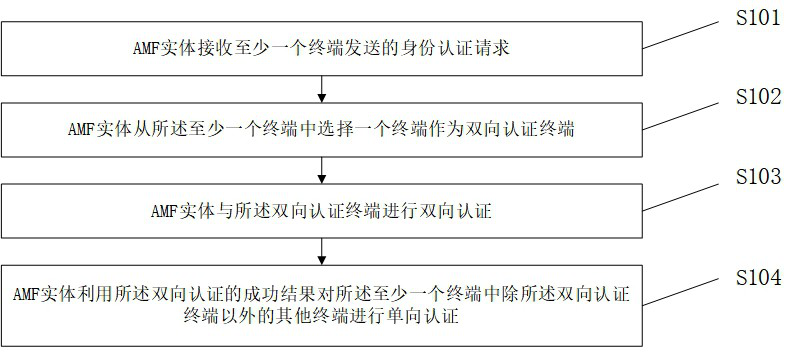
[0077] Such as figure 1 As shown, a MEC-based AMF entity identity authentication method includes:
[0078] S101: The AMF entity built on the edge physical infrastructure receives an identity authentication request sent by at least one terminal;
[0079] Among them, the AMF entity is constructed as follows:
[0080] Select edge physical infrastructure;
[0081] Leverage NFV to build AMF entities on edge physical infrastructure;
[0082] Calculate the network element security value of the AMF entity in real time;
[0083] When the network element security value of the AMF entity does not meet the predetermined requirement, replace the edge physical infrastructure on which the AMF entity is constructed until the network element security value of the AMF entity meets the predetermined requirement.
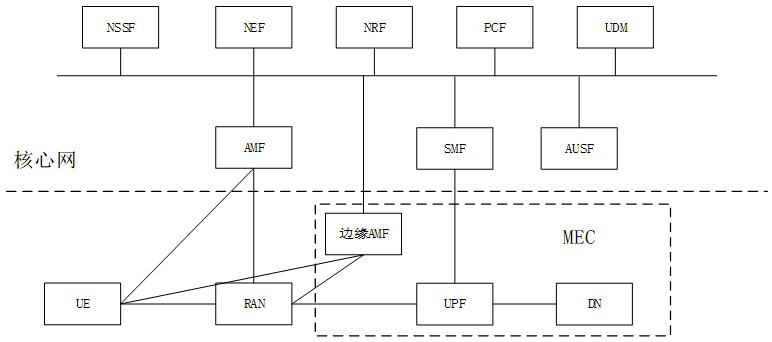
[0084] Such as figure 2 AMF entities are shown built on edge physical infrastructure (i.e. figure 2 "Edge AMF") network architecture.
[0085] MEC uses the computing and stora...
Embodiment 2
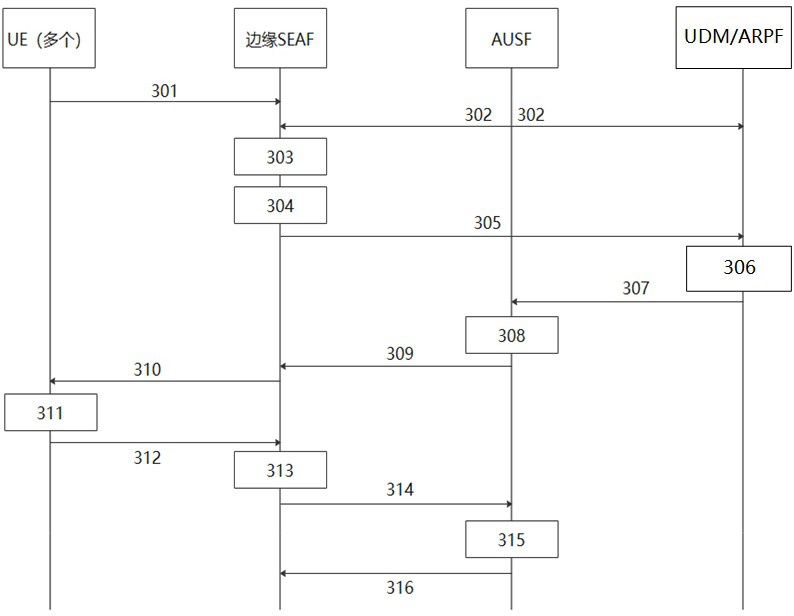
[0133] Such as Figure 4 As shown, Embodiment 1 of the present disclosure can also be improved as follows:
[0134] The method also includes:
[0135] S105: When the two-way authentication fails, the AMF entity reselects a terminal from the at least one terminal as a two-way authentication terminal; and performs two-way authentication on the reselected two-way authentication terminal.
Embodiment 3
[0137] Based on the same inventive idea as in Embodiment 1, as Figure 5 As shown, the present disclosure also provides a MEC-based AMF entity, including:
[0138] An authentication request receiving module 100, configured to receive an identity authentication request sent by at least one terminal;
[0139] An authentication selection module 200, configured to select a terminal from the at least one terminal as a two-way authentication terminal;
[0140] A two-way authentication module 300, configured to perform two-way authentication with the two-way authentication terminal;
[0141] The one-way authentication module 400 is configured to use the successful result of the two-way authentication to perform one-way authentication on other terminals in the at least one terminal except the two-way authentication terminal.
[0142] Among them, the AMF entity is constructed as follows:
[0143] Select edge physical infrastructure;
[0144] Leverage NFV to build AMF entities on ed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com