Firewall equipment regular matching method and device and computer readable storage medium
A matching method and firewall technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of regular matching, such as poor scalability, poor flexibility, and investment in manpower development, to achieve the effect of reducing protocol configuration and improving scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
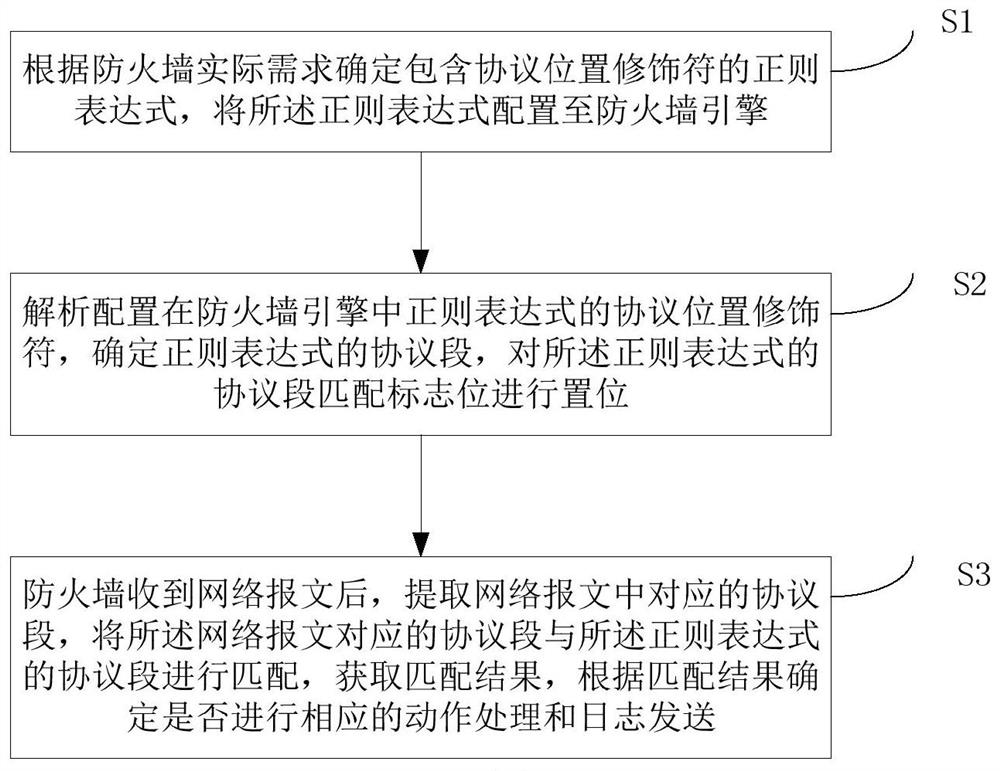
[0024] The embodiment of the present invention provides a regular matching method for a firewall device, and its flowchart is as follows: figure 1 As shown, the regular matching method of the firewall device includes the following steps:
[0025] Determine the regular expression containing the protocol position modifier according to the actual requirements of the firewall, and configure the regular expression to the firewall engine;
[0026] Parse the protocol position modifier of the regular expression configured in the firewall engine to determine the protocol segment of the regular expression, and set the protocol segment matching flag of the regular expression;
[0027] After the firewall receives the network message, it extracts the corresponding protocol segment in the network message, matches the protocol segment corresponding to the network message with the protocol segment of the regular expression, obtains the matching result, and determines whether to proceed accord...
Embodiment 2
[0136] The present invention also provides a regular matching device for firewall equipment, including a processor and a memory, and a computer program is stored in the memory, and when the computer program is executed by the processor, the implementation of any of the above-mentioned embodiments can be realized. Firewall device regular matching method.
Embodiment 3
[0138] The present invention also provides a computer-readable storage medium, on which a computer program is stored. When the computer program is executed by a processor, the firewall device regular matching method as described in any embodiment is realized.
[0139] It should be noted that the parts that are not repeatedly described in Embodiments 1-3 can be used for reference.
[0140] The invention discloses a firewall equipment regular matching method, device and computer-readable storage medium. The regular expression including the protocol position modifier is determined according to the actual requirements of the firewall, and the regular expression is configured to the firewall engine; the analysis is configured in the firewall engine The protocol position modifier of the regular expression determines the protocol segment of the regular expression, and the protocol segment matching flag of the regular expression is set; after the firewall receives the network message, ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap