Industrial anomaly monitoring method and device, computer equipment and readable storage medium
An anomaly monitoring and industrial technology, applied in the fields of computer equipment and readable storage media, devices, and industrial anomaly monitoring methods, can solve problems such as incomplete monitoring, vulnerable industrial systems, and in-depth protocol analysis, so as to avoid intrusion attacks. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
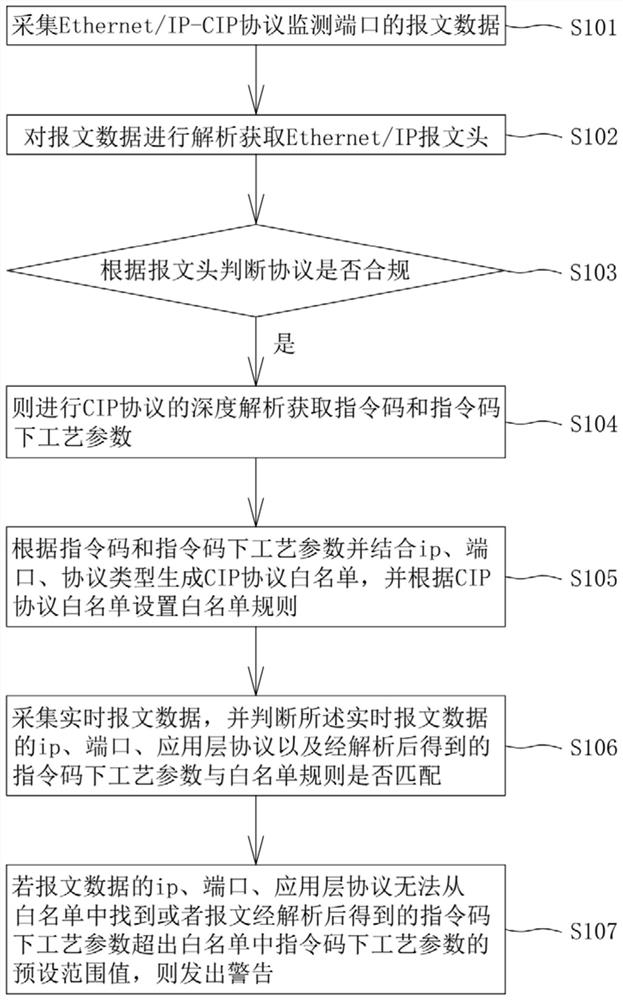
[0044] This embodiment provides an industrial abnormality monitoring method. figure 1 is a flow chart of an industrial abnormality monitoring method according to an embodiment of the present application, such as figure 1 As shown, the process includes the following steps S101-S107:
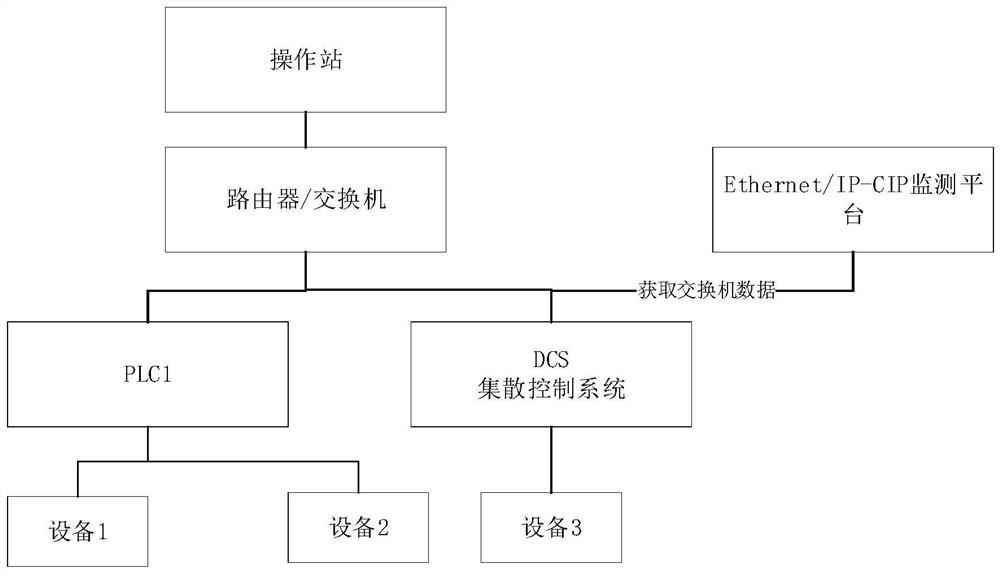
[0045] Step S101, collecting packet data of the Ethernet / IP-CIP protocol monitoring port.
[0046] Wherein, the packet data of the Ethernet / IP-CIP protocol monitoring port includes explicit packets and implicit packets.
[0047] Step S102, analyzing the message data to obtain the Ethernet / IP message header.
[0048] Wherein, before the step of analyzing the message data to obtain the Ethernet / IP message header, all message data is filtered through the port to filter out the CIP protocol message.
[0049] Step S103, judging whether the protocol is compliant according to the packet header;
[0050] Step S104, if it complies with the regulations, perform in-depth analysis of the CIP protocol to o...
Embodiment 2
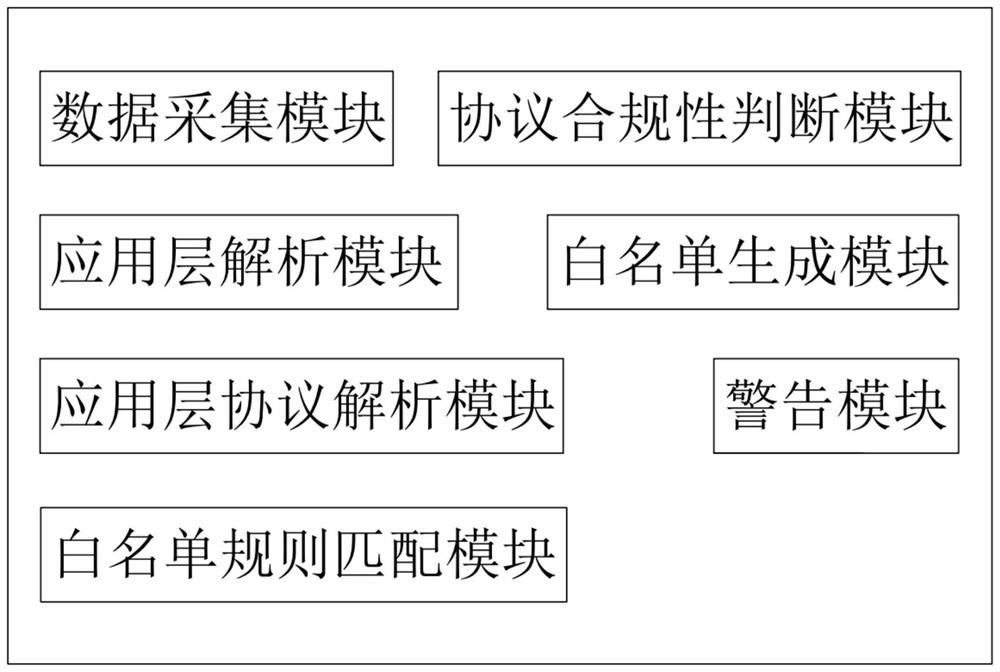
[0087] image 3 is a structural block diagram of an industrial anomaly monitoring device according to an embodiment of the present application, such as image 3 As shown, the device includes:
[0088] Data collection module: used to collect the message data of Ethernet / IP-CIP protocol monitoring port.
[0089] Application layer parsing module: used to parse the packet data to obtain the Ethernet / IP packet header.
[0090] Protocol compliance judging module: used to judge whether the protocol is compliant according to the packet header.
[0091] Application layer protocol analysis module: used to conduct in-depth analysis of the CIP protocol to obtain the instruction code and process parameters under the instruction code if it complies with the regulations.
[0092] Whitelist generation module: used to generate a CIP protocol whitelist based on the command code and process parameters under the command code combined with ip, port, and protocol type, and set whitelist rules ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com