Detection method of access control list ACL and network equipment
An access control list and network device technology, applied in the field of communications, can solve problems such as low ACL detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The embodiments of the present application will be further described in detail below in conjunction with the accompanying drawings.
[0035] In order to facilitate understanding, a description of concepts related to the present application is given for reference, as follows:
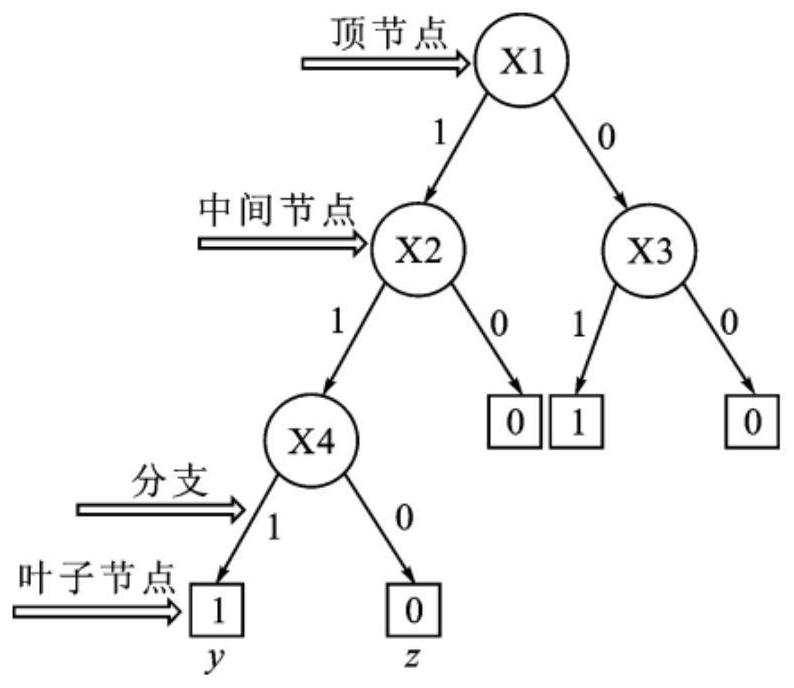
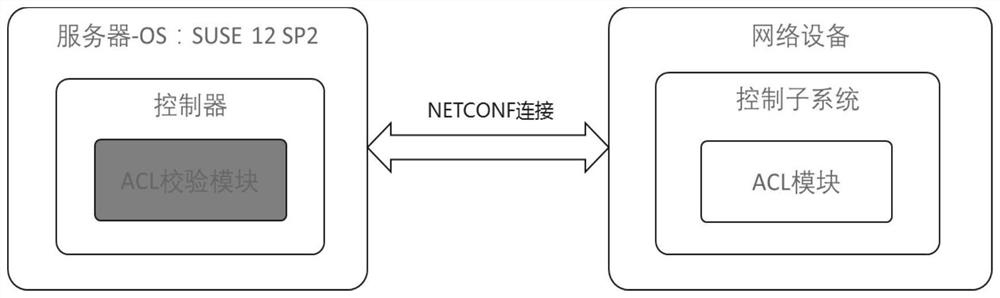
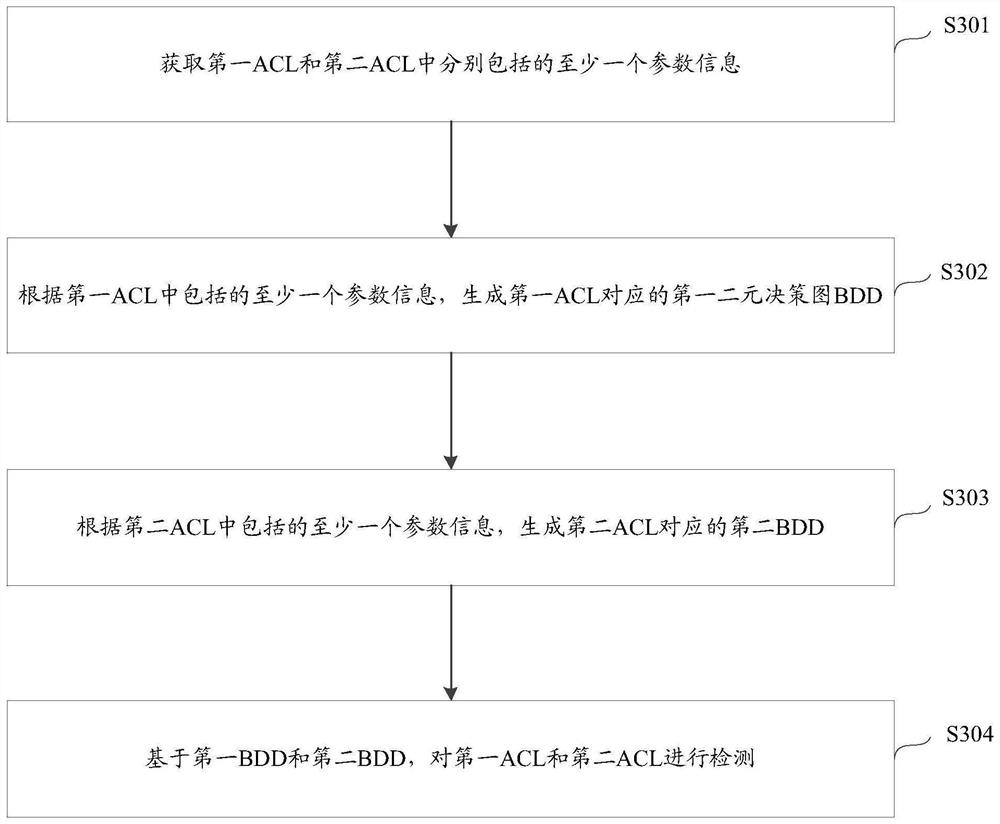
[0036] 1) Access control list (acces control list, ACL): The instruction list of the router and switch interface, including a series of matching rules, conditions and actions, used to control the data packets entering and leaving the port. The role of ACL includes restricting network traffic, providing control means for communication traffic, providing basic means for network security access, and improving network performance.
[0037]According to the application purpose of the ACL, the ACL can be divided into the following types: (1), basic ACL: formulate rules only according to the layer-3 source IP address. (2) Advanced ACL: Formulate rules based on the third and fourth layers of information s...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap