Blockchain semantic analysis method based on authenticable data structure
A technology of authentication data and semantic analysis, applied in the blockchain field, can solve problems such as difficult compilers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
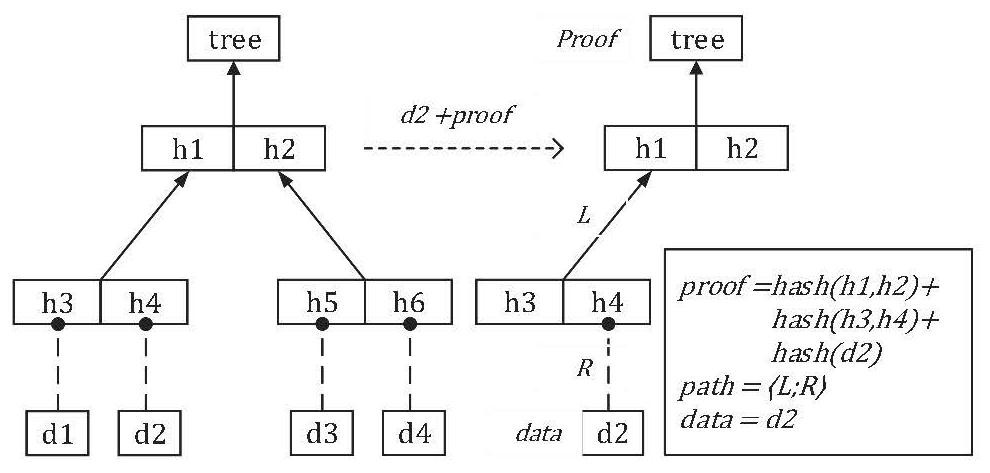
[0189] 1. Data acquisition:
[0190] a) Abstract the certifiable data structure into a signature through the Modular mechanism:
[0191] moduletypeAUTHENTIKIT=sig
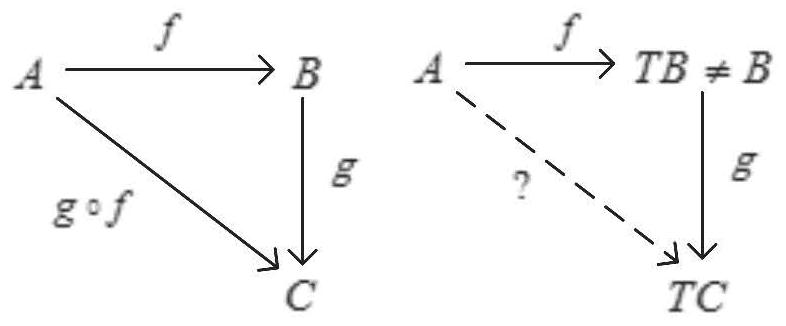
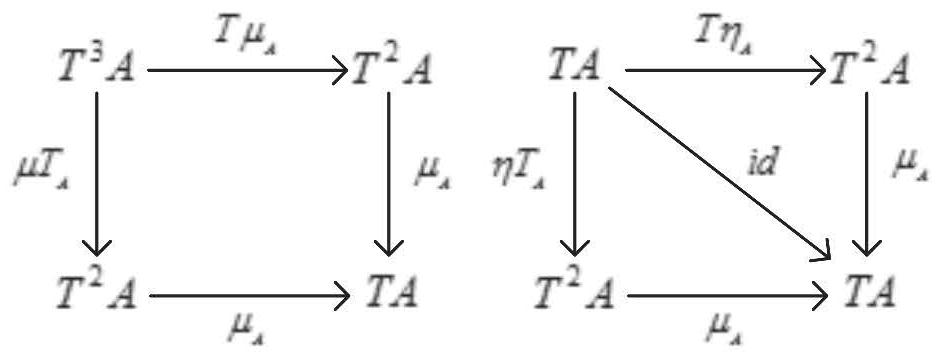
[0192] b) Describe the abstract certifiable computing unit, map, join, and bind. For details, please refer to the complete Monad interface code snippet of certifiable computing:
[0193] type'a authenticated_computation
[0194] val return: 'a->'a authenticated_computation
[0195] val(>>=):'a authenticated_computation->
[0196] ('a -> 'b authenticated_computation) ->
[0197] 'b authenticated_computation
[0198] c) Prove that the data flow to be verified is continuous, that is, the data is required to be continuous and complete. Specifically participate in the function definition code snippet of Auth and Unauth:
[0199] val auth:'aAuthenticatable.evidence->'a->'aauth
[0200] val unauth: 'a Authenticatable.evidence->'a auth->
[0201] 'a authenticated_computation
[0202] d) Generate proof stream. Si...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap