User name sample labeling method and device, electronic equipment and storage medium
A user name, sample technology, applied in the field of network security, can solve the problem of inaccurate model recognition results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
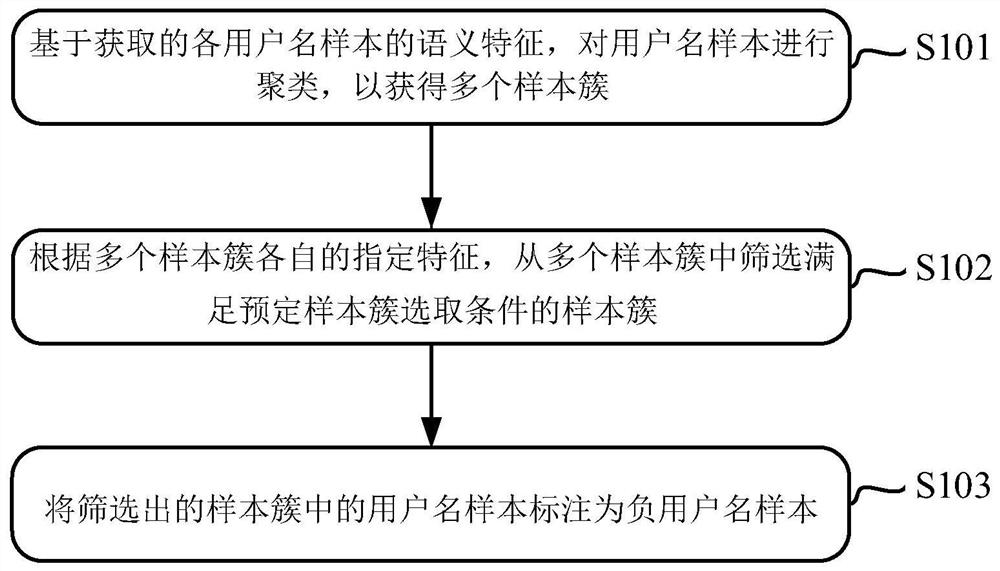
[0082] figure 1 is a flow chart of a method for labeling user name recognition samples according to an exemplary embodiment, as shown in figure 1 As shown, this method can improve the accuracy of the recognition results of the username recognition model.
[0083] The execution subjects of the method include but are not limited to servers, personal computers, notebook computers, tablet computers, smart phones and other intelligent electronic devices that can execute predetermined processing procedures such as numerical calculations and / or logic calculations by running predetermined programs or instructions. Wherein, the server may be a single server or multiple servers. The method may include the steps of:
[0084] In step S101, based on the acquired semantic features of each user name sample, the user name samples are clustered to obtain a plurality of sample clusters.
[0085] In an implementation manner, before step S101 is performed, acquiring a user name sample may also...
Embodiment 2
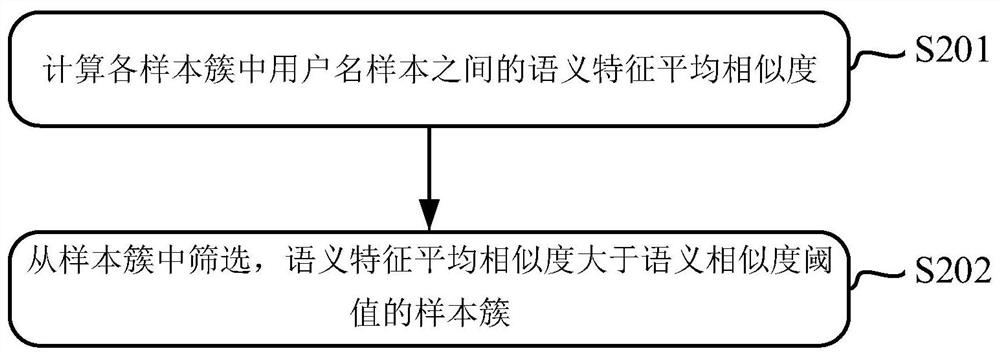
[0150] figure 2 is a flow chart of a method for labeling user name samples according to an exemplary embodiment, as shown in figure 2 As shown, in step S102, according to the specified characteristics of the multiple sample clusters, the sample clusters that meet the predetermined sample cluster selection conditions are selected from the multiple sample clusters, including the following steps S201 to S202:
[0151] The specified features of the sample cluster include: the average similarity of semantic features between different username samples in the sample cluster;
[0152] The sample cluster selection conditions include: the average semantic feature similarity between different user name samples in the sample cluster is greater than the semantic similarity threshold.
[0153] In step S201, calculate the semantic feature average similarity between user name samples in each sample cluster;
[0154] In an optional implementation manner, calculating the average semantic fe...
Embodiment 3
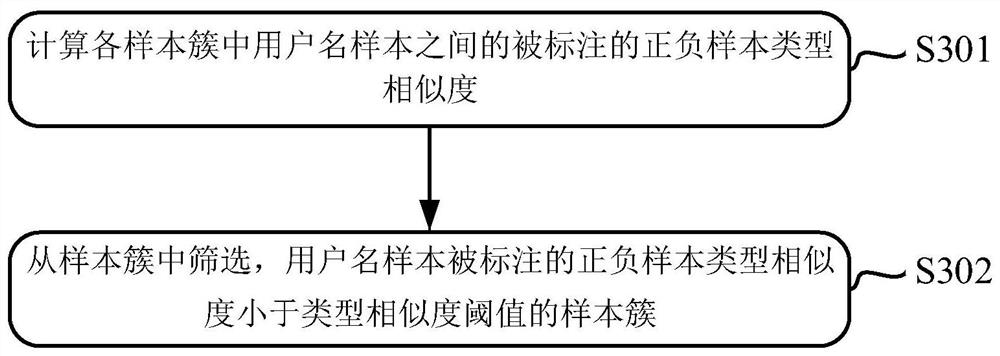
[0166] image 3 is a flow chart of a method for labeling user name samples according to an exemplary embodiment, as shown in image 3 As shown, in step S102, according to the respective specified characteristics of the multiple sample clusters, the sample clusters that meet the predetermined sample cluster selection conditions are selected from the multiple sample clusters, including the following steps S301 and S302:
[0167] Among them, the specified characteristics of the sample cluster include: the similarity of the positive and negative sample types marked by the user name sample in the sample cluster;
[0168] Predetermined sample cluster selection conditions include: the positive and negative sample type similarity of the user name sample marked in the sample cluster is less than the type similarity threshold.
[0169] In step S301, the labeled positive and negative sample type similarities between user name samples in each sample cluster are calculated.
[0170] In a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com