A business behavior security control method, system and device
A technology of security control and behavior, applied in the field of Internet information security and anti-cheating, can solve problems such as modification and optimization, single dimension, and inability to implement strategies in time, and achieve the effects of monitoring data fluctuations, reducing accidental injury rates, and optimizing strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical solutions of the present invention will be clearly and completely described below in conjunction with the accompanying drawings and specific embodiments.
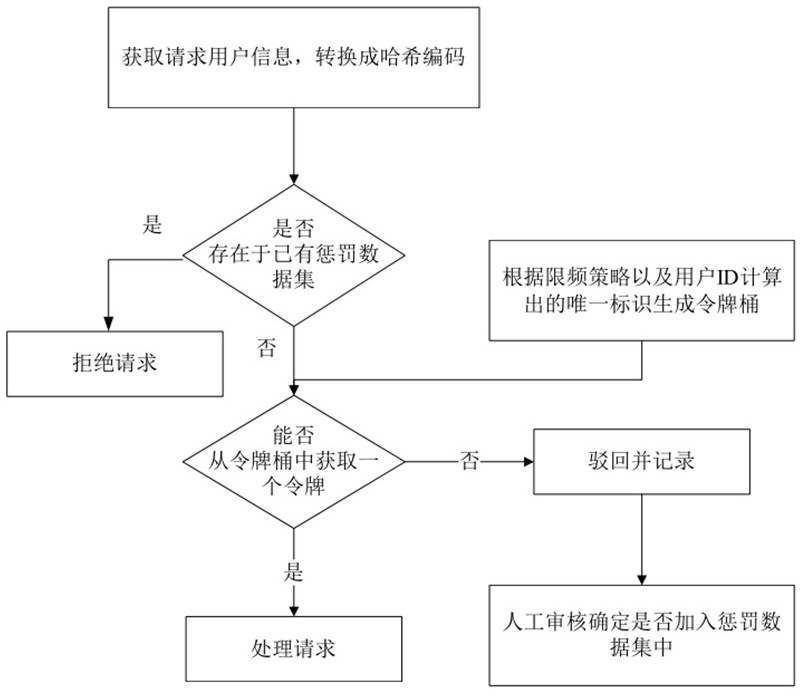
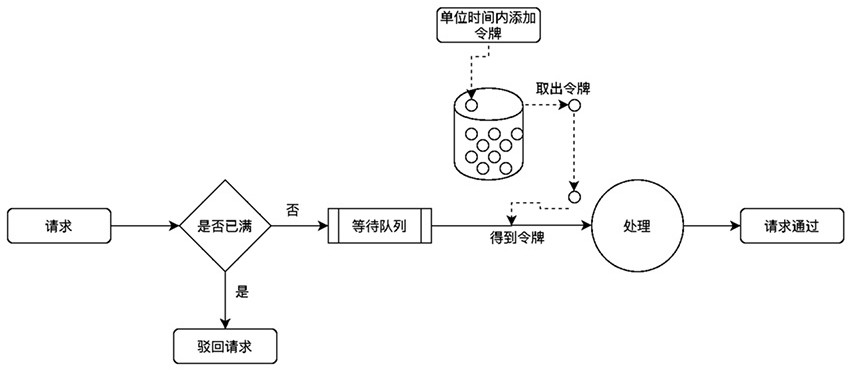
[0029] like figure 1 As shown, a business behavior security control method disclosed in the embodiment of the present invention mainly includes the following steps:
[0030] S1: Validation of user information. Obtain requesting user information, including user characteristic value data carried in the user request, or characteristic value data and request type, and judge whether it exists in the existing penalty data set, and reject the user's request operation if it exists. In this embodiment, the characteristic value data of the user includes one or more of the user ID, the user mobile phone number, the user WeChat ID, the user device number, and the user IP address.
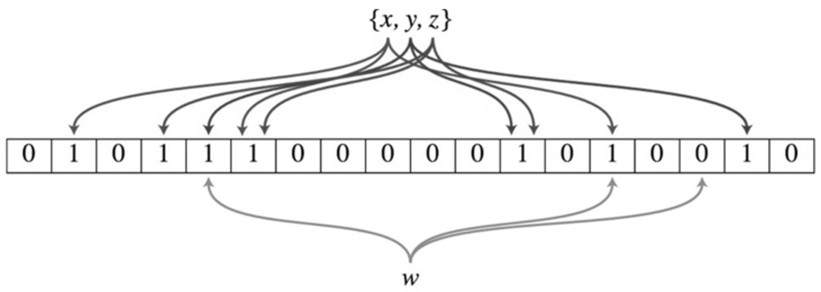
[0031] In order to improve the efficiency of user information verification, the user feature value data obtained in this step is conv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com