A cloud security access system and method
A secure access and cloud technology, applied in the field of network security management, can solve the problems of data transmission process being easily intercepted by others, information leakage, etc., and achieve the effect of accurate comparison and high comparison efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
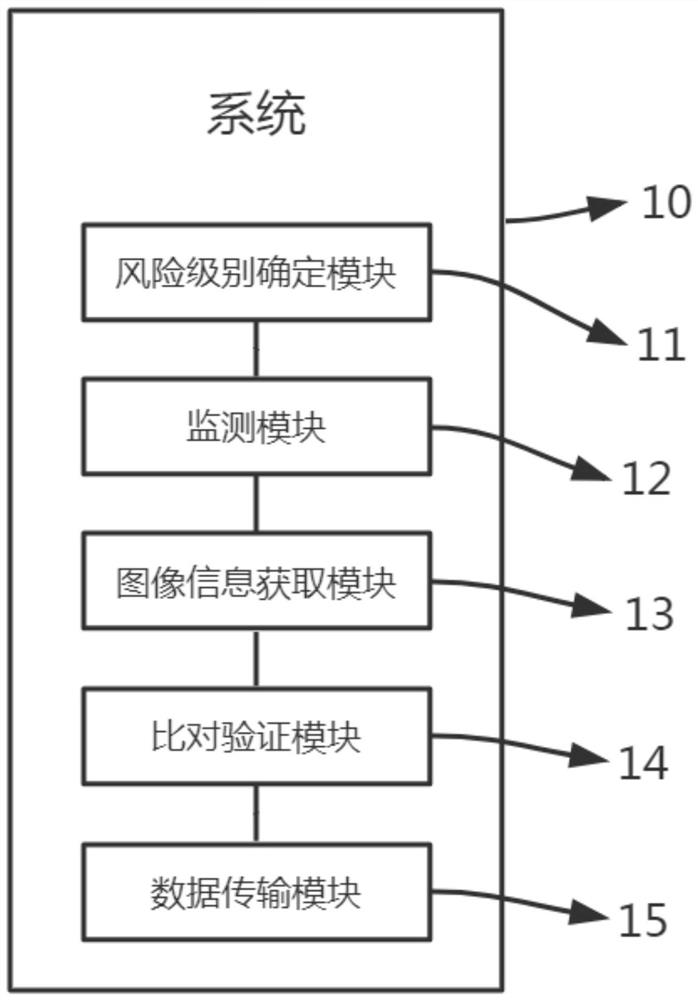
[0071] figure 1 A block diagram of the composition and structure of a cloud security access system is shown. In this embodiment of the present invention, a cloud security access system is provided, and the system 10 includes:
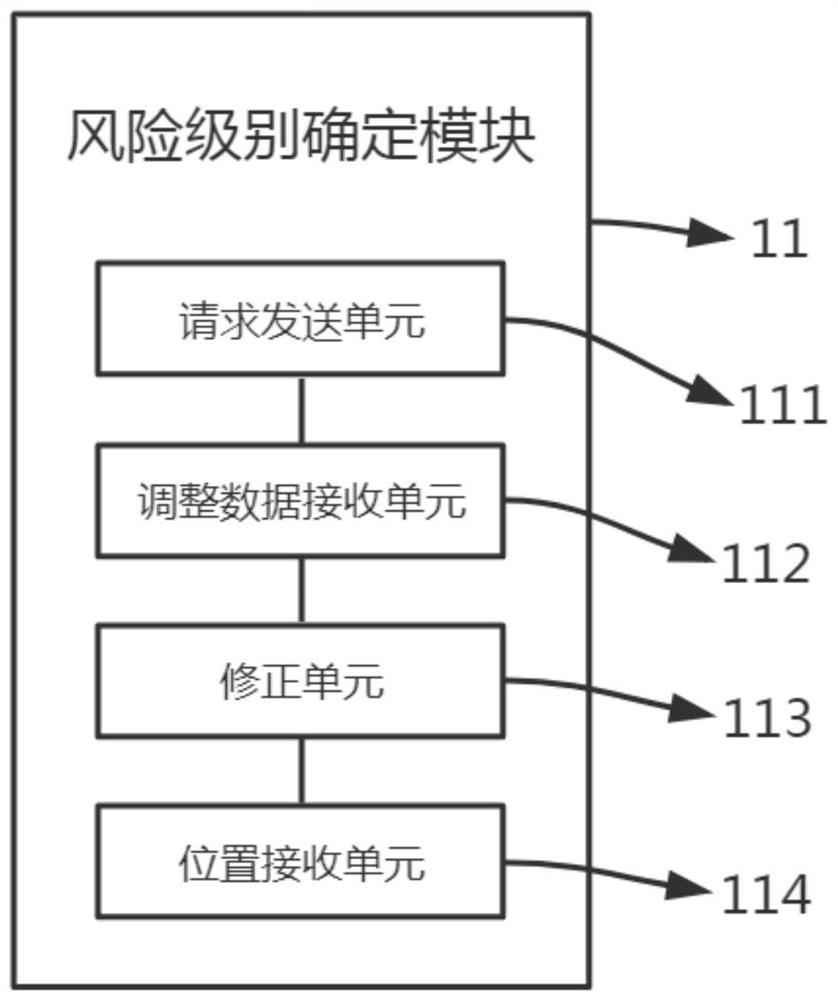
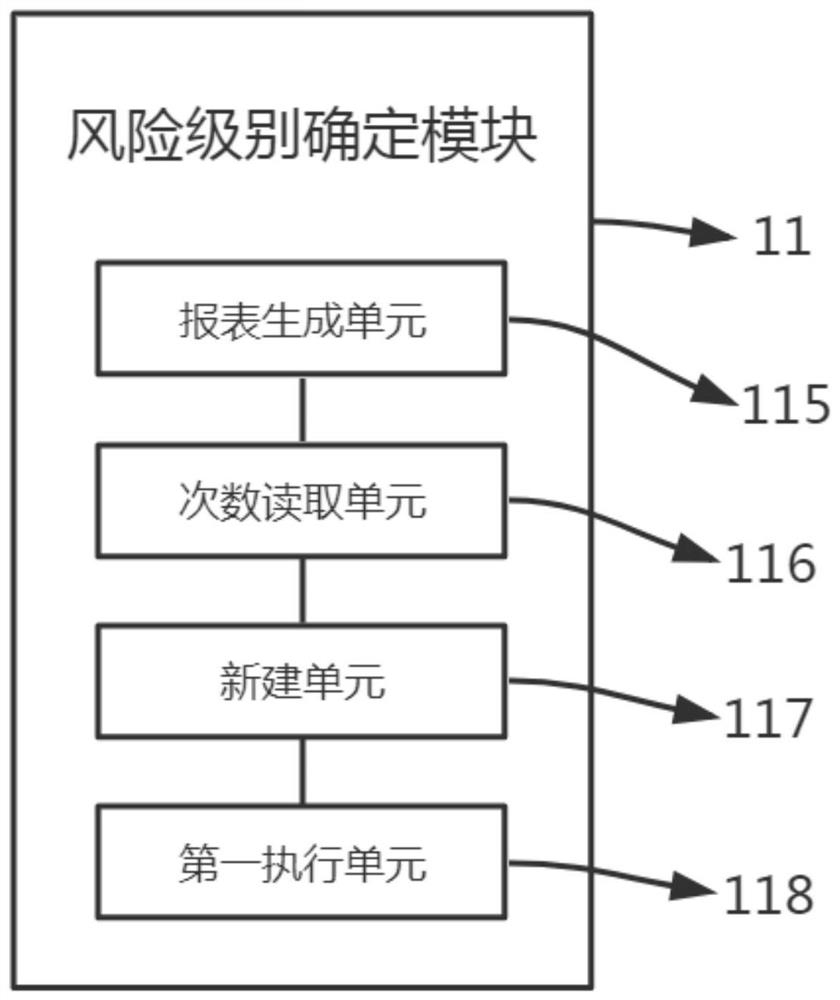
[0072] a risk level determination module 11, configured to receive an access request, obtain location information, and determine a risk level according to the location information;
[0073] The monitoring module 12 is used for real-time monitoring information input port when the risk level reaches a preset level threshold;
[0074] The image information acquisition module 13 is used to lock the information input port, determine the cloud address, and obtain the image information of the information input interface when the information input port is monitored;
[0075] A comparison verification module 14, configured to obtain a base image according to the cloud address, and compare and verify the image information based on the base image;
[0076] The d...
Embodiment 2
[0122] Figure 8 A flow block diagram of a cloud security access system and method is shown. In an embodiment of the present invention, a cloud security access method is provided, and the method includes:
[0123] Step S100: receiving an access request, acquiring location information, and determining a risk level according to the location information;
[0124] Step S200: when the risk level reaches a preset level threshold, real-time monitoring information is entered into the port;
[0125] Step S300: when the information entry port is monitored, the information entry port is locked, the cloud address is determined, and the image information of the information entry interface is obtained;
[0126] Step S400: Acquire a base image according to the cloud address, and compare and verify the image information based on the base image;
[0127] Step S500: After the image information passes the comparison and verification, unlock the information entry port, obtain user account infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com