Handle identification system-oriented DDoS defense method
A technology of identification and system, which is applied in the field of communication and information technology security, can solve the problems of consuming network resources and Internet DDoS defense methods cannot be used directly.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in detail through specific embodiments below in conjunction with the accompanying drawings, but it does not constitute a limitation to the present invention.
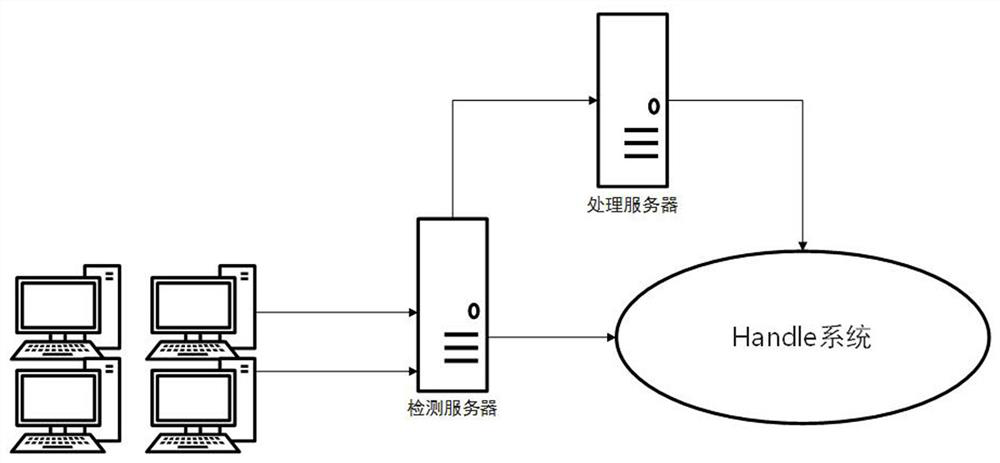
[0038] Deploy a detection server before the Handle ID query reaches the recursive query node, and perform DDoS attack detection on the server. In addition, a processing server is deployed to process Handle identification query requests exceeding the limit value. The Handle identification system of the method of the present invention deploys sub-node servers such as figure 1 shown.
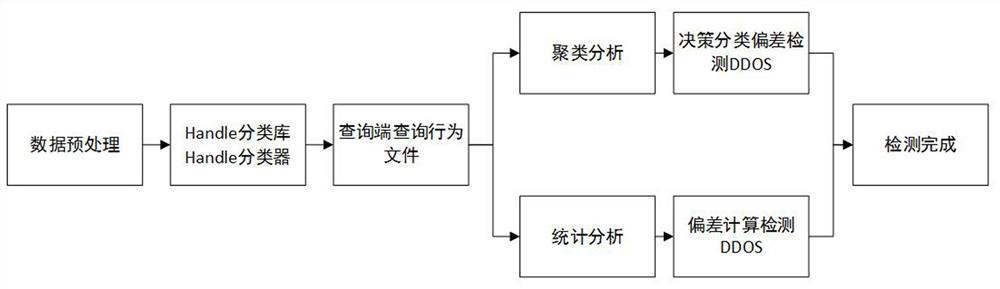
[0039] A DDoS defense method oriented to the Handle identification system is divided into five modules, which are the Handle function topic determination module, cluster analysis module, statistical analysis module, detection module, and layered speed limit processing module.
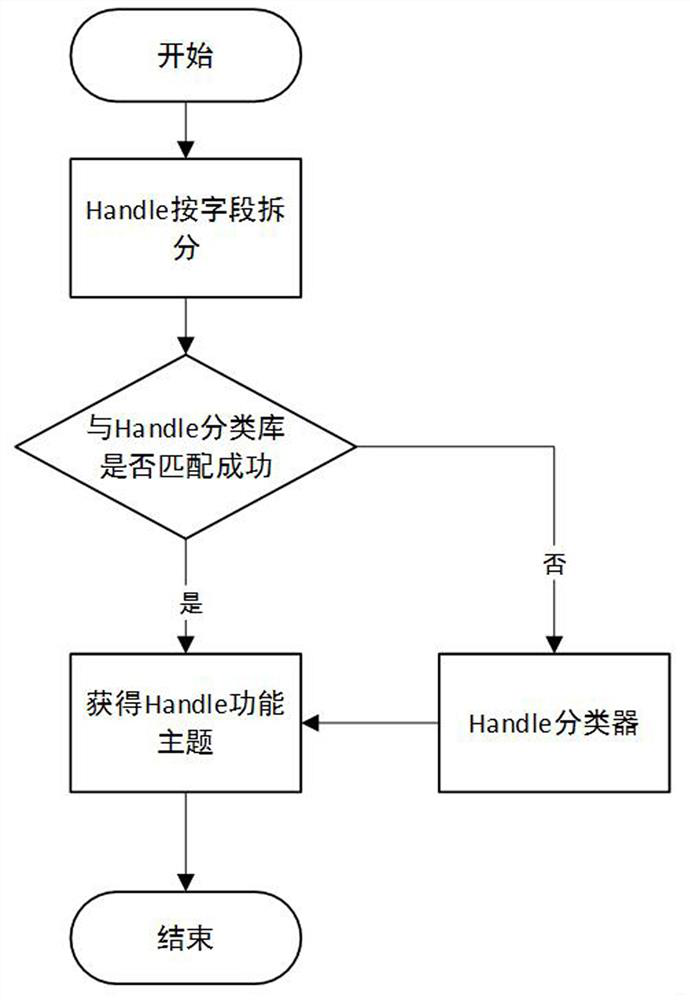
[0040] 1. For the Handle function topic determination module, two methods of establishing a Handle classification lib...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com