Cryptographic data verification method
A technology of data and data sets, used in digital data authentication, digital data protection, electrical digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
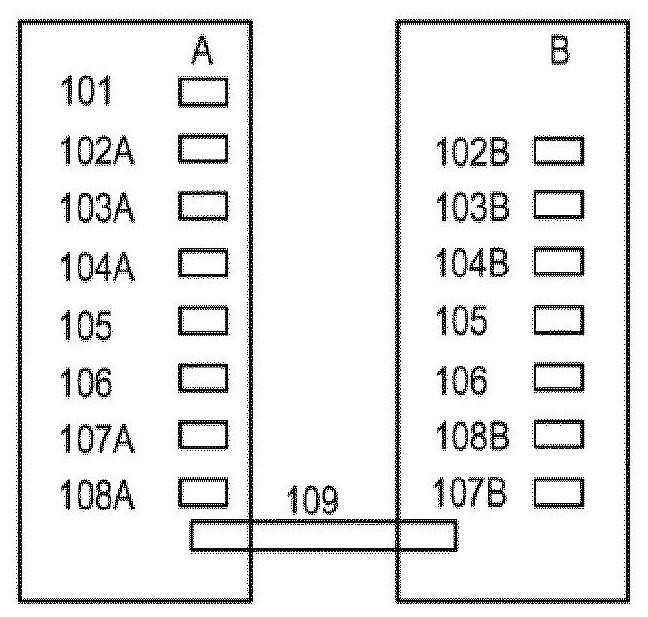
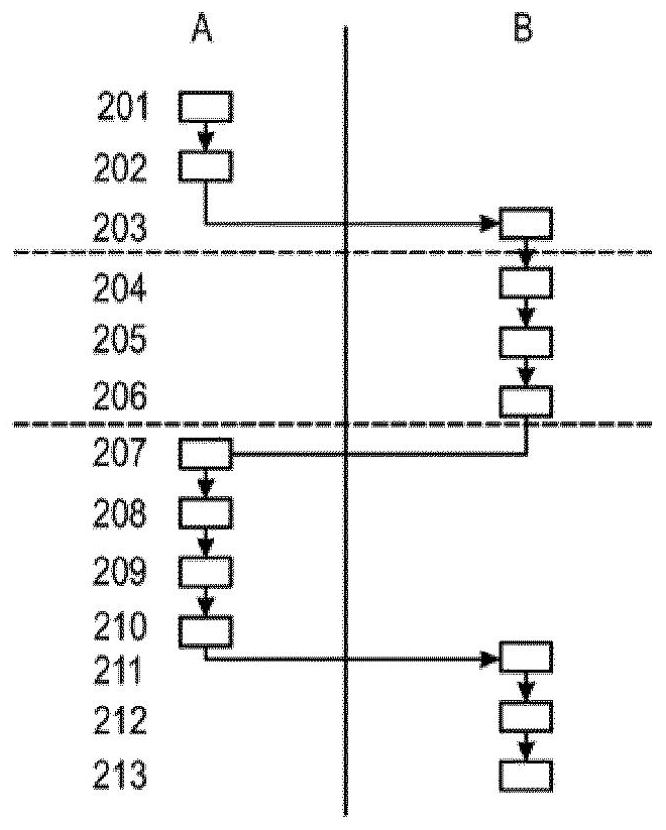
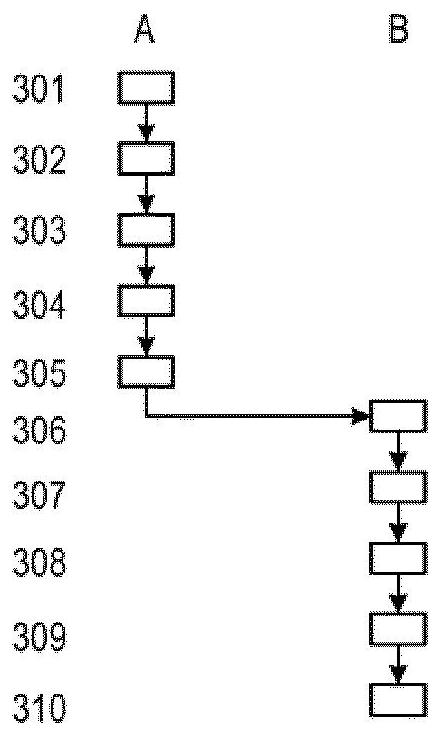
[0128] figure 1 Schematically shows the data and functions for implementing the invention according to the first variant or the second variant, where a message 101 has to be sent by device A to device B via a data transmission channel 109, possibly a secure or unsafe.
[0129] Device A may be a personal computer or a smart phone, device B is an email server, and message 101 is, for example, an email sent by a computer or phone over the Internet.
[0130] Device A can also be a server that sends emails or web pages, and device B is a personal computer or smart phone that receives said emails or web pages.
[0131] Device A could even be a measuring device, for example for measuring the consumption of electricity, gas or water, or for measuring the wear of parts in a machine, message 101 being the result of such a measurement, device B collecting the measurements and passing A server that communicates with a measurement device in a telecommunication network (eg IoT, Wi-Fi netw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com