Enforcing threat policy actions based on network addresses of host threats
A network address and host technology, applied in digital transmission systems, secure communication devices, electrical components, etc., can solve problems such as insufficient security control at the periphery of the network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
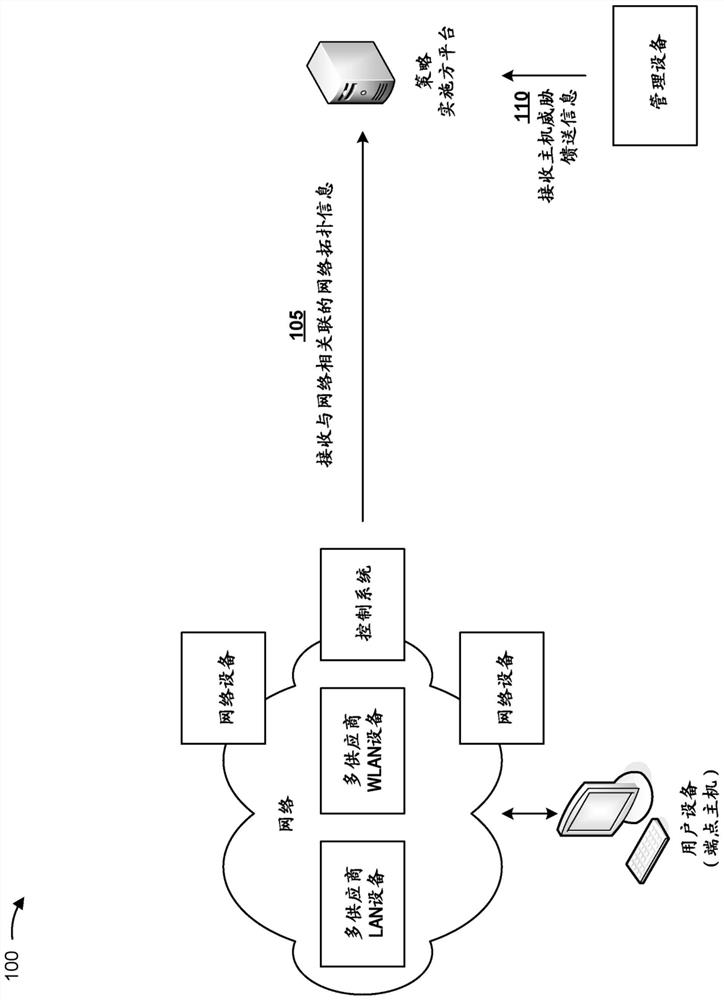
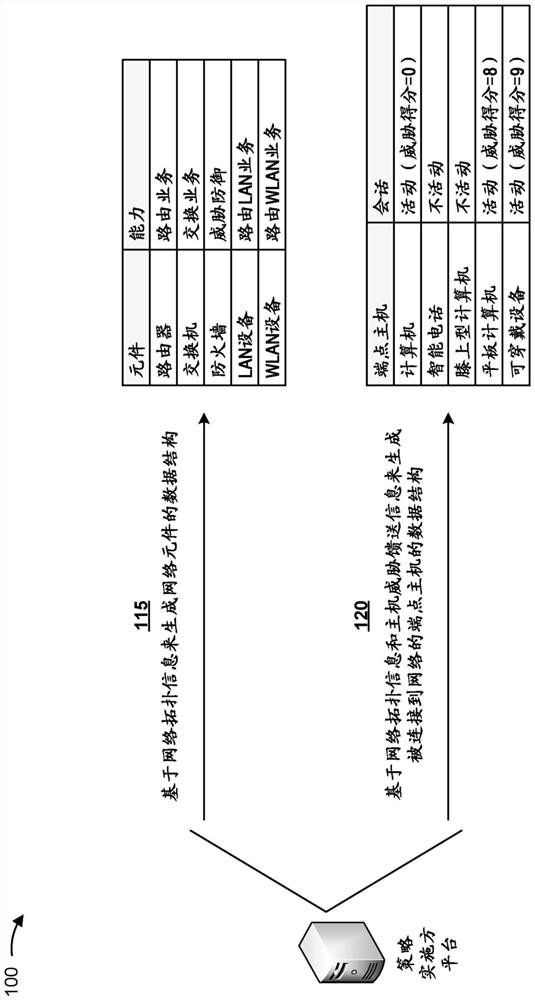
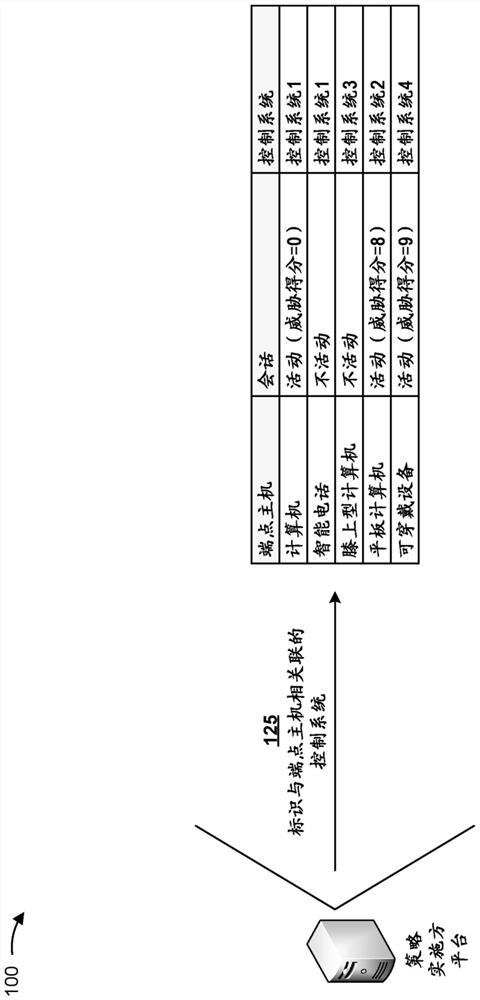
[0015] The following detailed description of example implementations refers to the accompanying drawings. The same reference numbers in different drawings may identify the same or similar elements.
[0016] A threat remediation system that is unaware of the mobility of potential endpoint host threats within a network introduces several challenges. For example, threat identification is limited to detection in the data path of endpoint host threats communicating with the network through perimeter network devices, the lateral spread of endpoint host threats inside the network cannot be detected and its further expansion cannot be controlled, and once the endpoint host threat moves to Depending on the network segment, endpoint host threats may gain additional access and privileges, thereby compromising unprotected network segments. As a result, threat remediation systems cannot consistently and effectively monitor, identify, and remediate endpoint host threats across the entire n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com