Log identification method and device, electronic equipment and storage medium
An identification method and log technology, applied in the field of network security, can solve time-consuming and labor-intensive problems, achieve the effects of improving efficiency, facilitating log identification, and reducing the workload of research and judgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
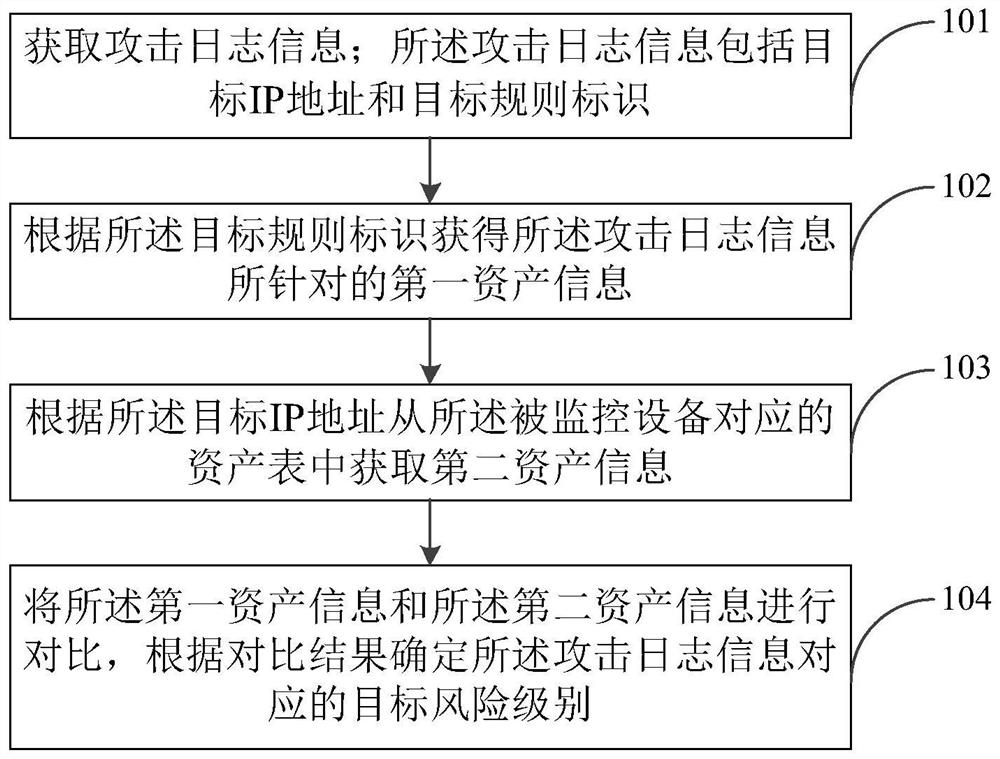
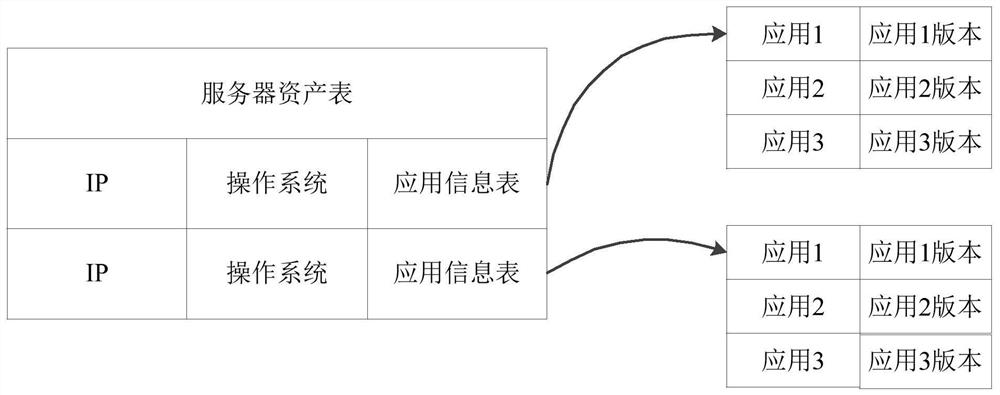
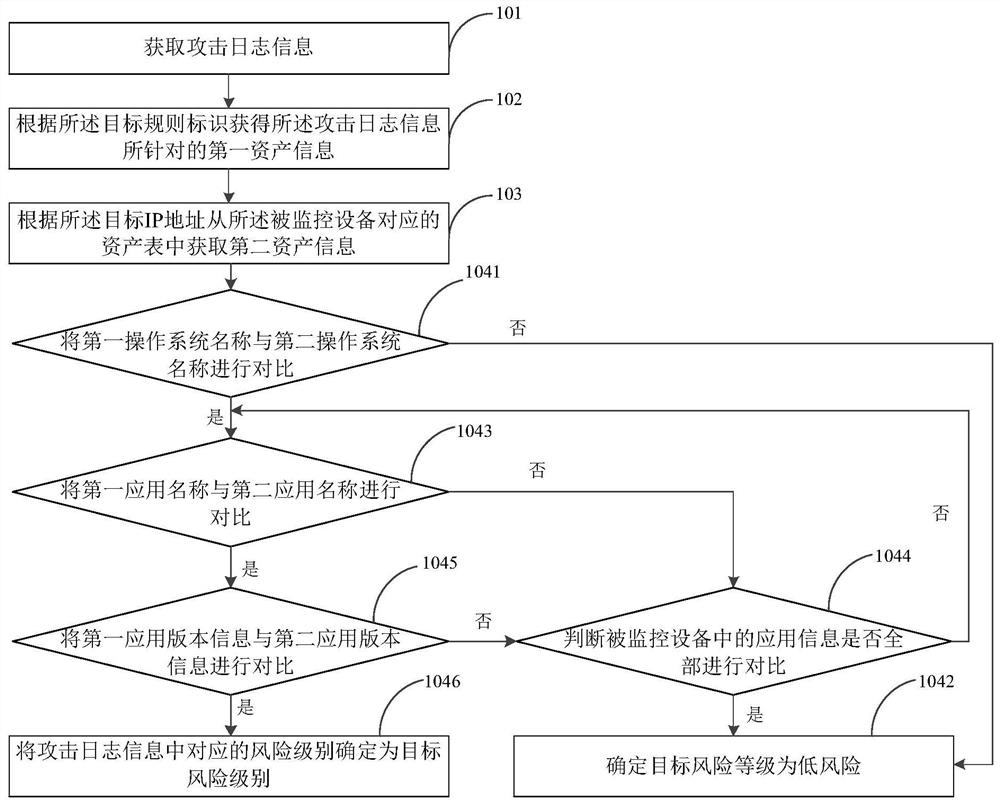
[0023] In view of the fact that firewalls generate a large number of attack logs, manually checking each attack log will consume a lot of manpower and material resources. Moreover, when there are many attack log information, manual inspection results will not be given in time, which will make the The operation of monitoring equipment is affected. In order to solve this technical problem, the present application focuses on the asset information targeted by the attack log information, and compares it with the asset information of the monitored device, so as to determine the risk level corresponding to the attack log information according to the comparison result. Therefore, the embodiment of the present application can determine whether the attack log information is a false positive through an automated research and judgment method, thereby reducing the consumption of human resources and improving the efficiency of identifying the attack log information.
[0024] The technical s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com