XSS fuzzy test case generation method based on time convolutional network
A convolutional network, time technology, applied in biological neural network models, neural learning methods, software testing/debugging, etc., can solve problems such as single type, poor variability of single characters, limited number of use cases, etc., to solve gradient explosion or gradient The effect of disappearing, good pertinence, and improving generation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The training data of the present invention is made up of some attack sentences of the XSS Filter Evasion Cheat Sheet in OWASP and some key load dictionaries open source on the Internet. Among them, 95% of the samples have been proved to be effective in practical applications, so XSS vulnerabilities can be discovered.
[0083] The present invention adopts following technical scheme and implementation steps:
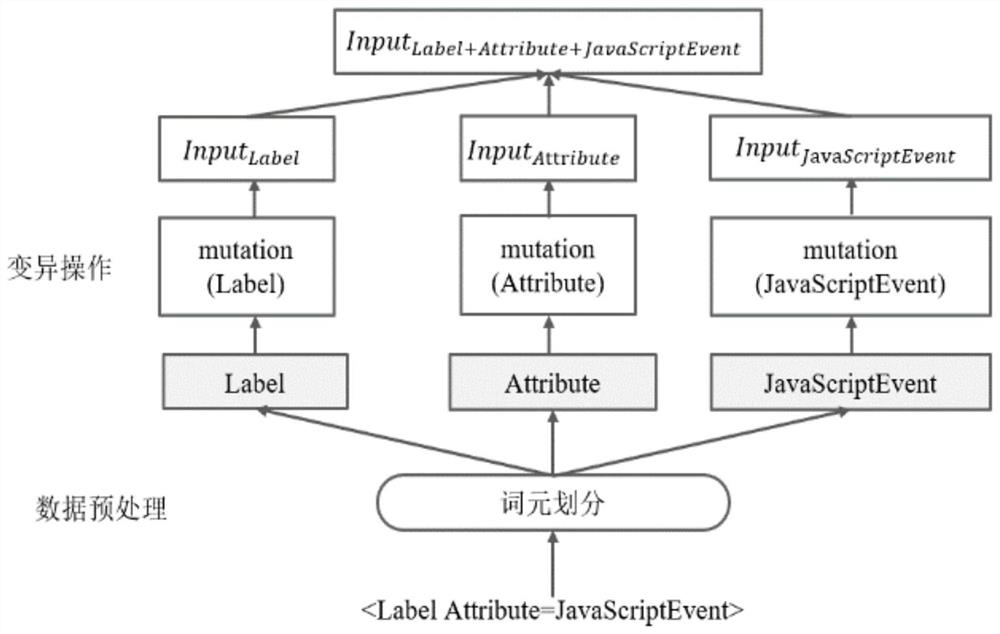
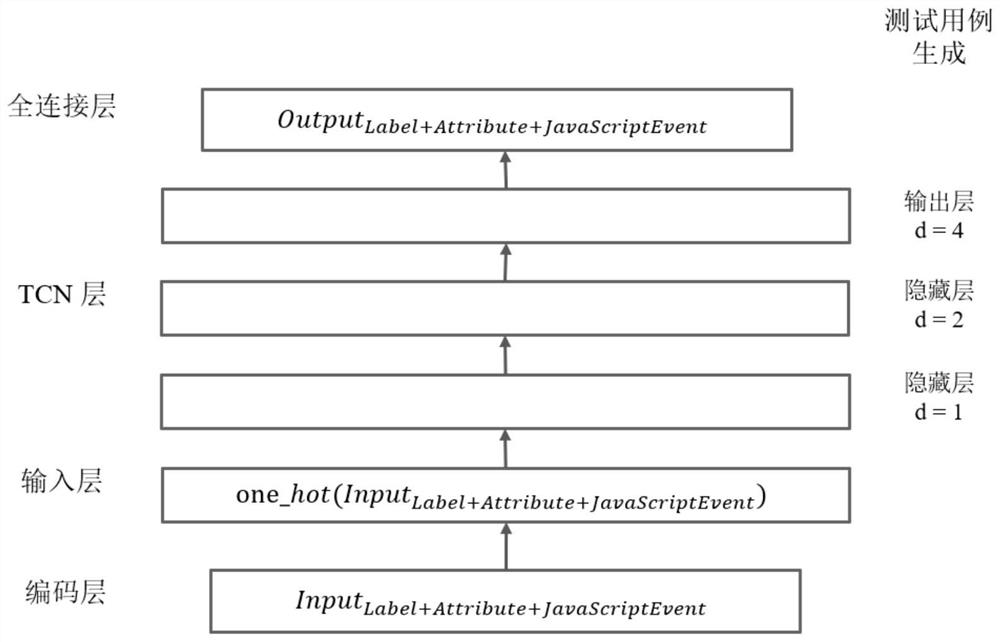
[0084] 1. Data preprocessing stage: determine the input and output variables of the temporal convolution network language generation model: take the XSS vulnerability test case as the research object, carry out structural division and mutation operation on the key load part in the XSS vulnerability test case, and obtain the mutation respectively After the labels, attributes and event functions, the expanded key load data set PM=(pm 1 ,pm 2 ,...,pm z ) as the input for the next stage;
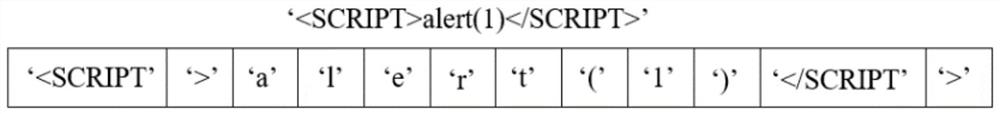
[0085] The basic form of the key payload Payload in an XSS test case can be e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com