Regular rule generation method based on unsupervised thought in mimicry WAF
An unsupervised and rule-based technology, applied in the field of network security, can solve problems such as difficulty in evaluation, system complexity, and impossibility to repair vulnerabilities, and achieve the effect of strengthening security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
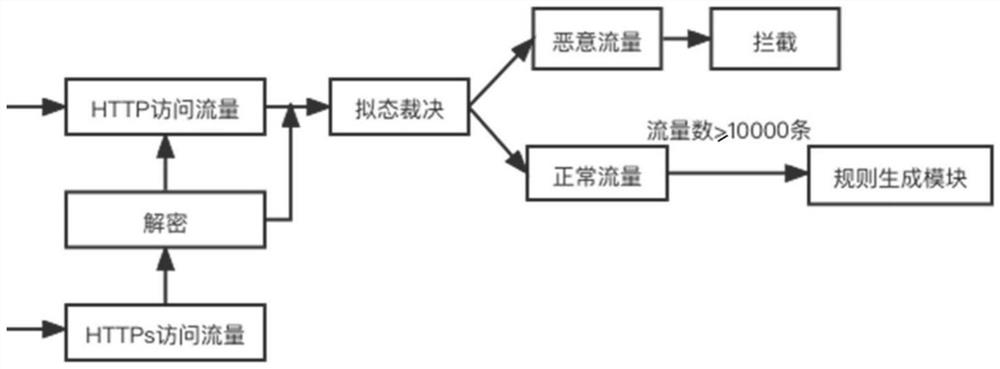
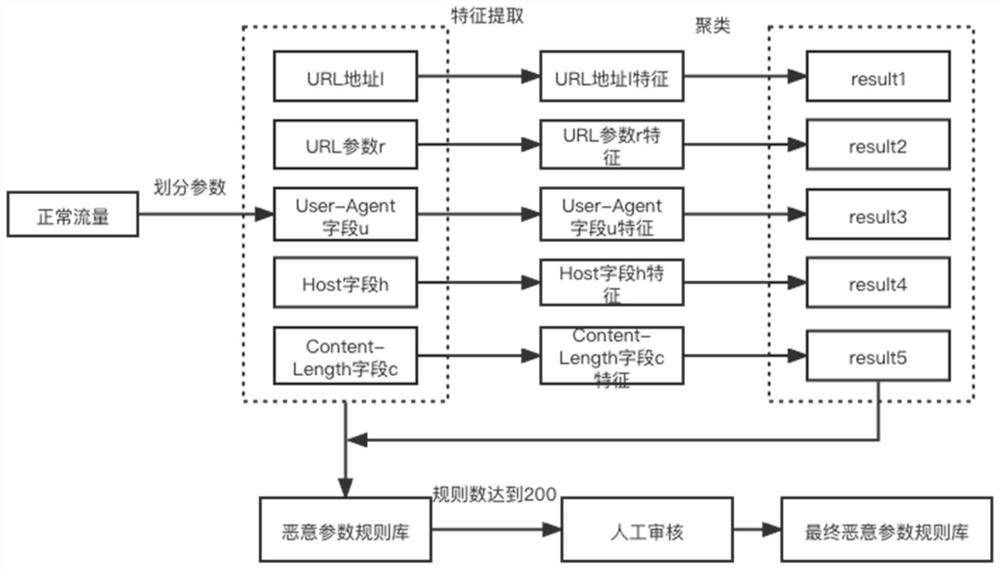
[0031] The invention discloses a method for generating regular rules based on an unsupervised idea in the mimic WAF, which is used for generating regular rules in the mimic WAF, and supplements the regular rule library in real time according to new traffic. The present invention designs a mimic ruling module, a traffic collection module, a parameter extraction module, a parameter feature extraction module, a clustering module, a rule generation module, and a manual review module, and counts the traffic passing through the regularity detection module. When the traffic reaches 10,000 , start the unsupervised generation rule engine, extract the parameters in the traffic, and input the parameter value into the feature extraction module to obtain the feature vector, perform clustering, input the clustered parameter value into the rule base to be selected, and manually select the parameter level rule to add to The rule base is a supplement to the regular rule base in Mimic WAF.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com