Authority authentication method and authority information processing method and device
A technology of authority authentication and communication device, which is applied in the field of communication and can solve problems such as network equipment being unable to connect to authority control servers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0103] The embodiments of the present application provide a rights authentication method, rights information processing method and device, which can determine whether a peer communication device supports a certain network function.
[0104] For ease of understanding, possible application scenarios of the embodiments of the present application are first introduced.
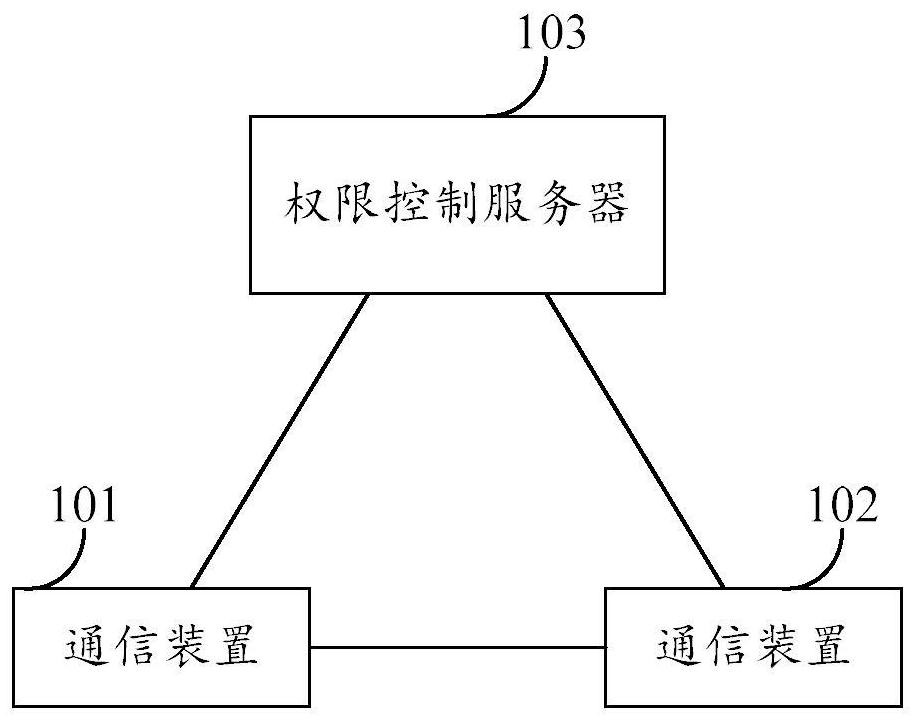
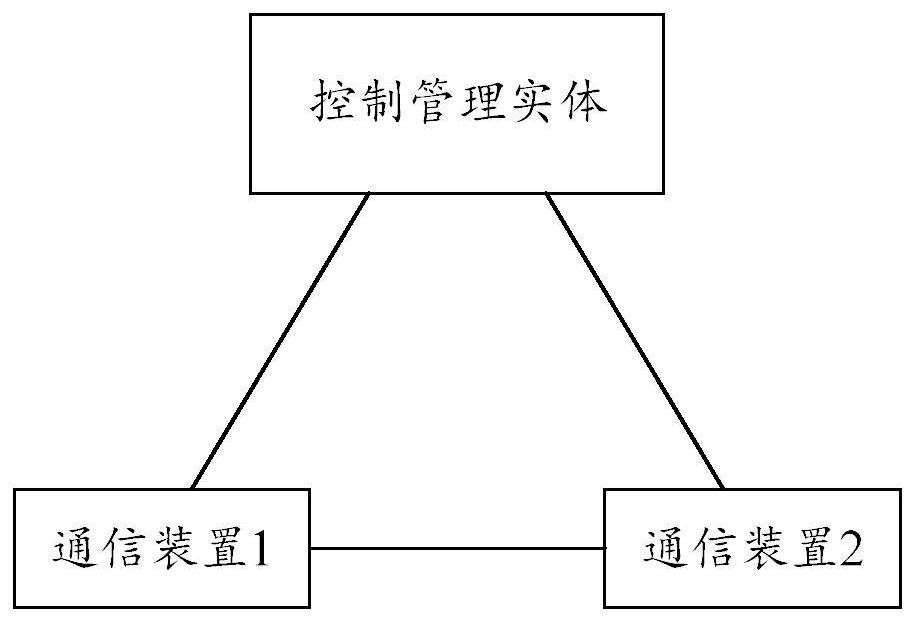
[0105] see Figure 1a , which is a schematic diagram of an exemplary application scenario. like Figure 1a As shown, communication between the communication device 101 and the communication device 102 is possible. Before the communication device 101 and the communication device 102 need to cooperate to implement the network function a, the communication device 101 can determine whether the communication device 102 supports the network function a, and correspondingly, the communication device 102 can determine whether the communication device 101 supports the network function a. If the communication device 101 dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com