Identifying illegal base stations
A technology for illegal base stations and base stations, which is applied in the field of identifying illegal base stations and can solve the problems of data theft, interception, and malware download of wireless devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
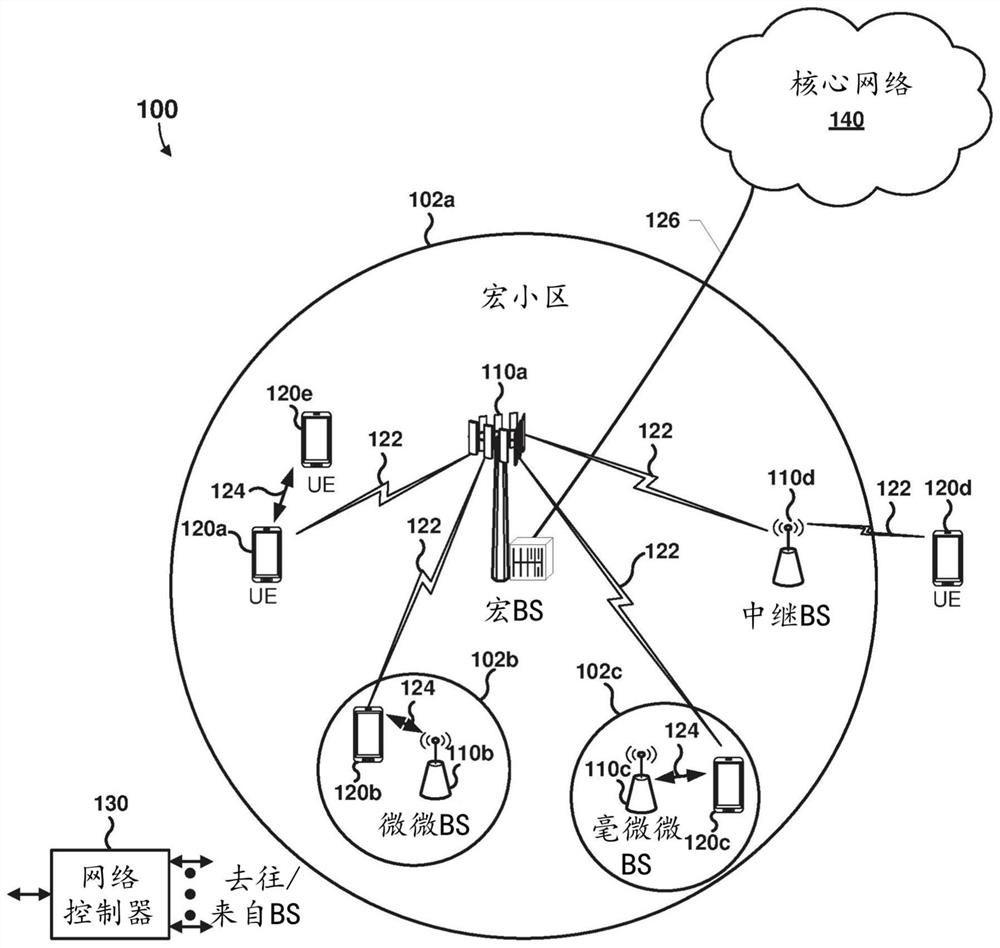
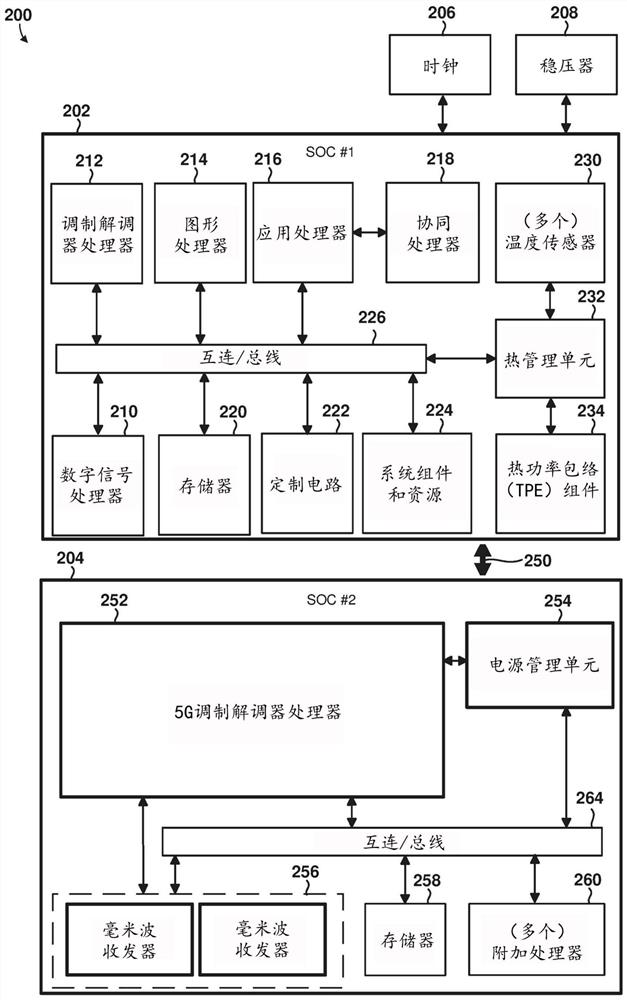
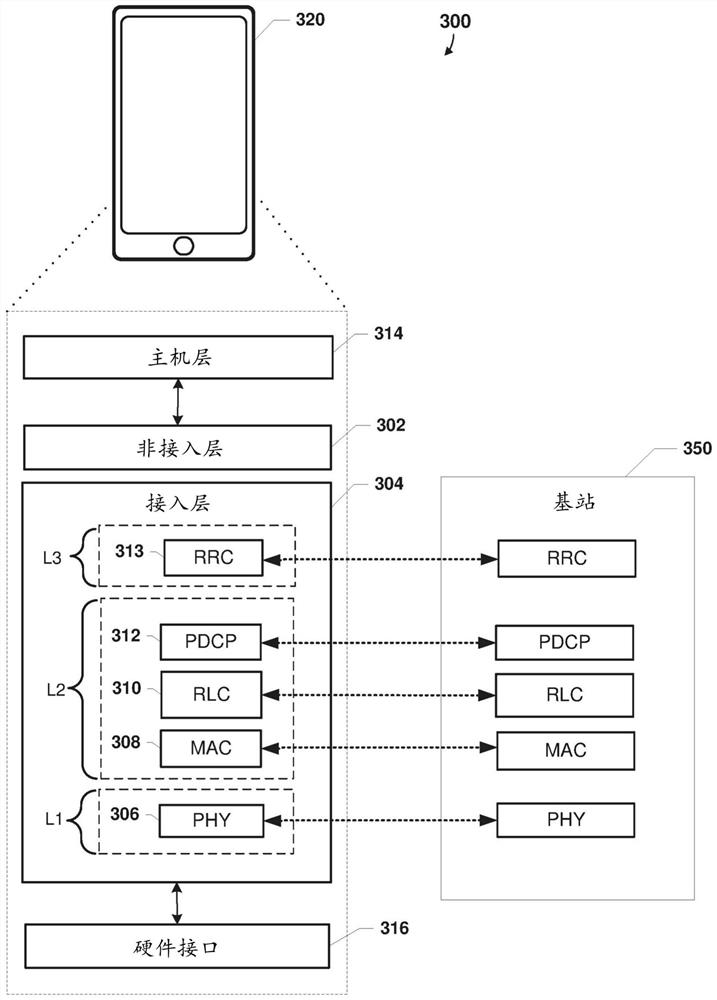
[0021] Various embodiments will be described in detail with reference to the accompanying drawings. Wherever possible, the same reference numbers will be used throughout the drawings to refer to the same or like parts. References to specific examples and implementations are for illustrative purposes and are not intended to limit the scope of the claims.
[0022] Various embodiments include methods and wireless devices configured to identify rogue base stations using various methods. In some embodiments, the processor of the wireless device can determine that the device is a suspicious base station, and the processor of the wireless device can transmit one or more forged messages to the device. Based on the response message or more than one response message received from the device in response to the one or more forged messages, the processor of the wireless device can determine whether the suspected base station is a rogue base station or a legitimate base station. In variou...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap