Method for recording and reproducing compacted voice file by using decryption key
A technology for audio files and recording methods, applied in the direction of preventing unauthorized use of memory, protecting stored content from loss, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Hereinafter, according to the embodiment of the present invention, the decoding key recording method and reproducing method of the compressed audio file will be described in detail with reference to the accompanying drawings.
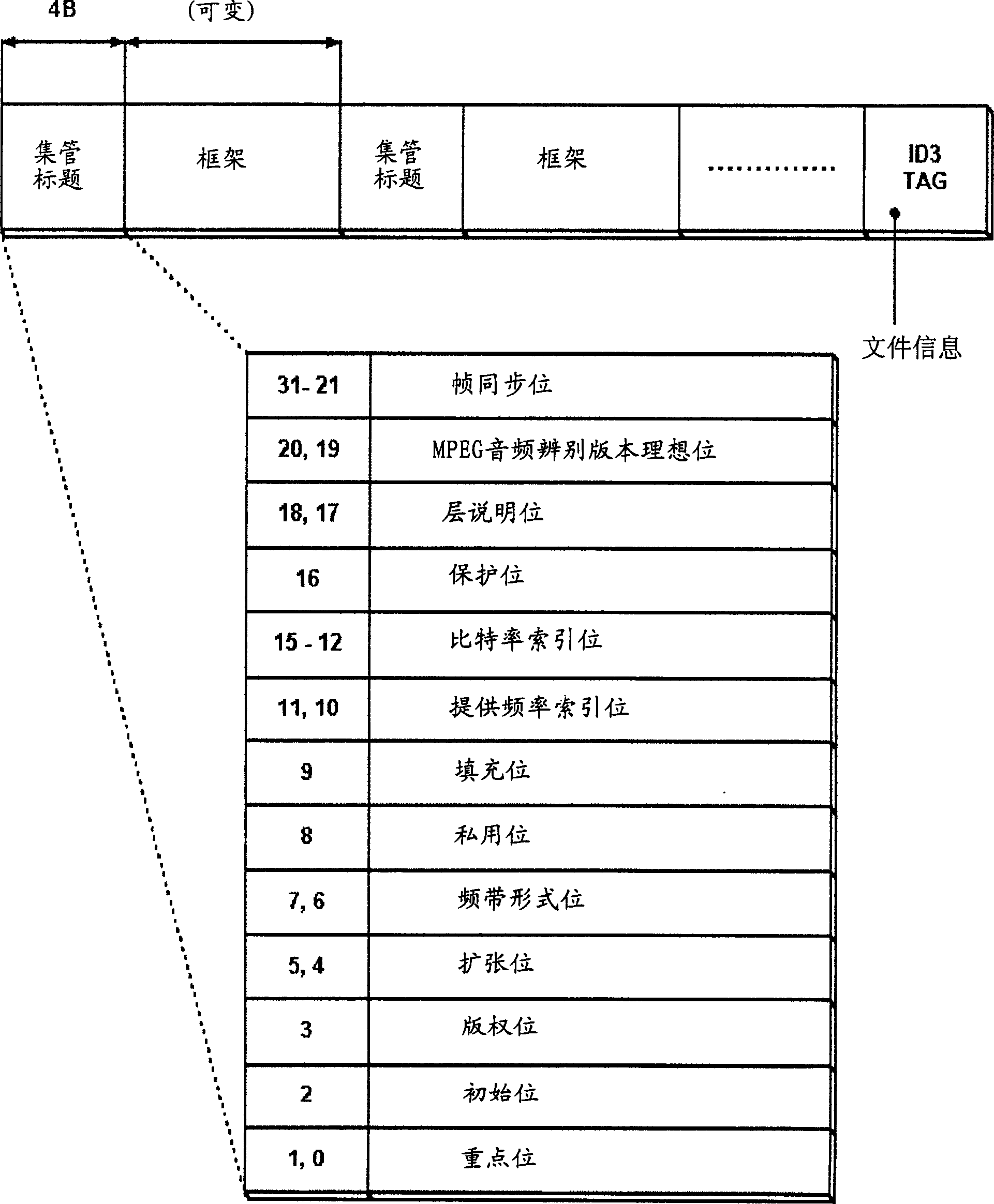
[0025] see figure 2 , figure 2 Shown is the composition diagram of the MP3 audio file in which the decryption key is dispersedly recorded in an embodiment of the present invention.
[0026] to refer to figure 1 As stated above, in an MP3 audio file, at least one frame containing a 4-byte fixed-length header and an arbitrary "variable length" is recorded, including the above-mentioned MP3 audio file. 128 bytes tag information.
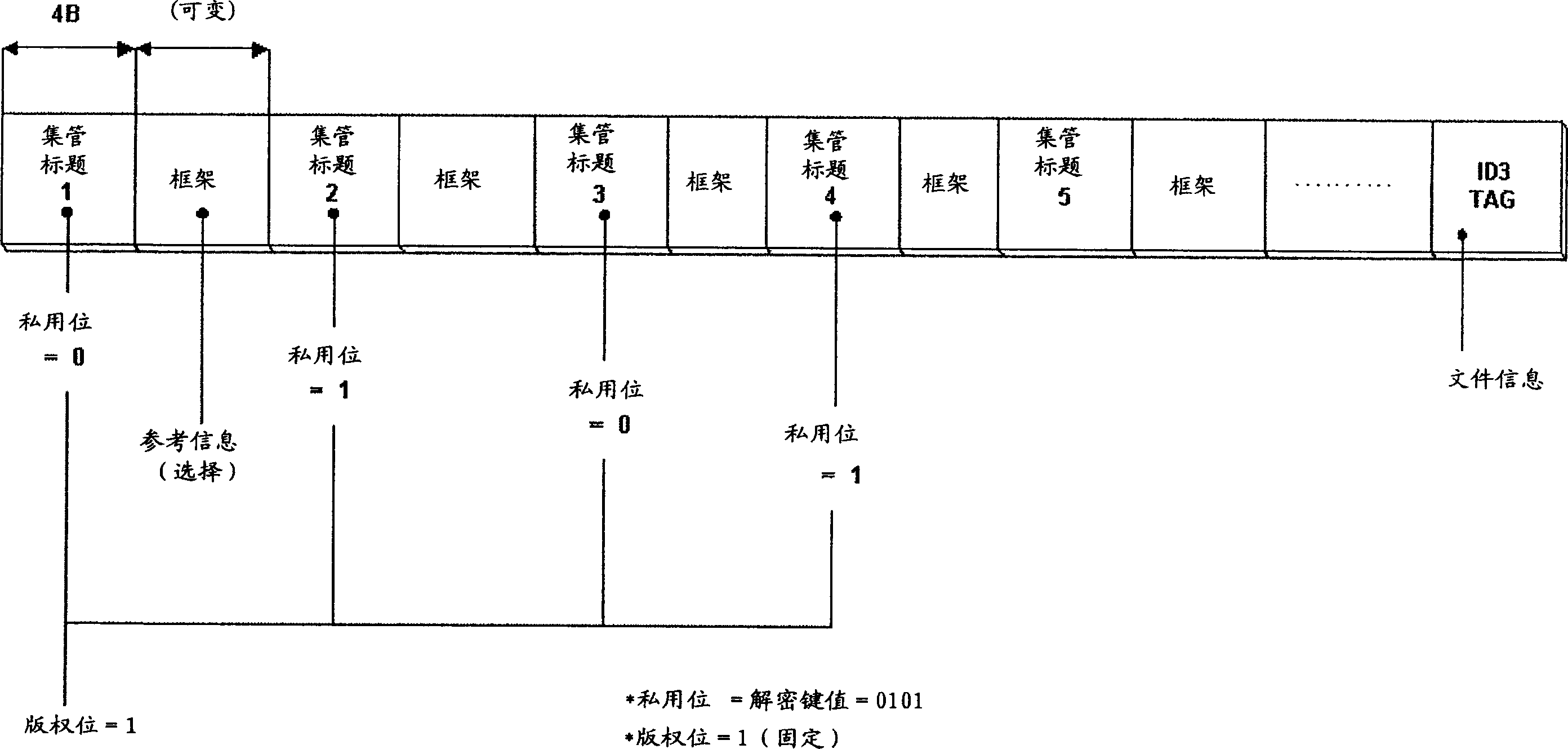
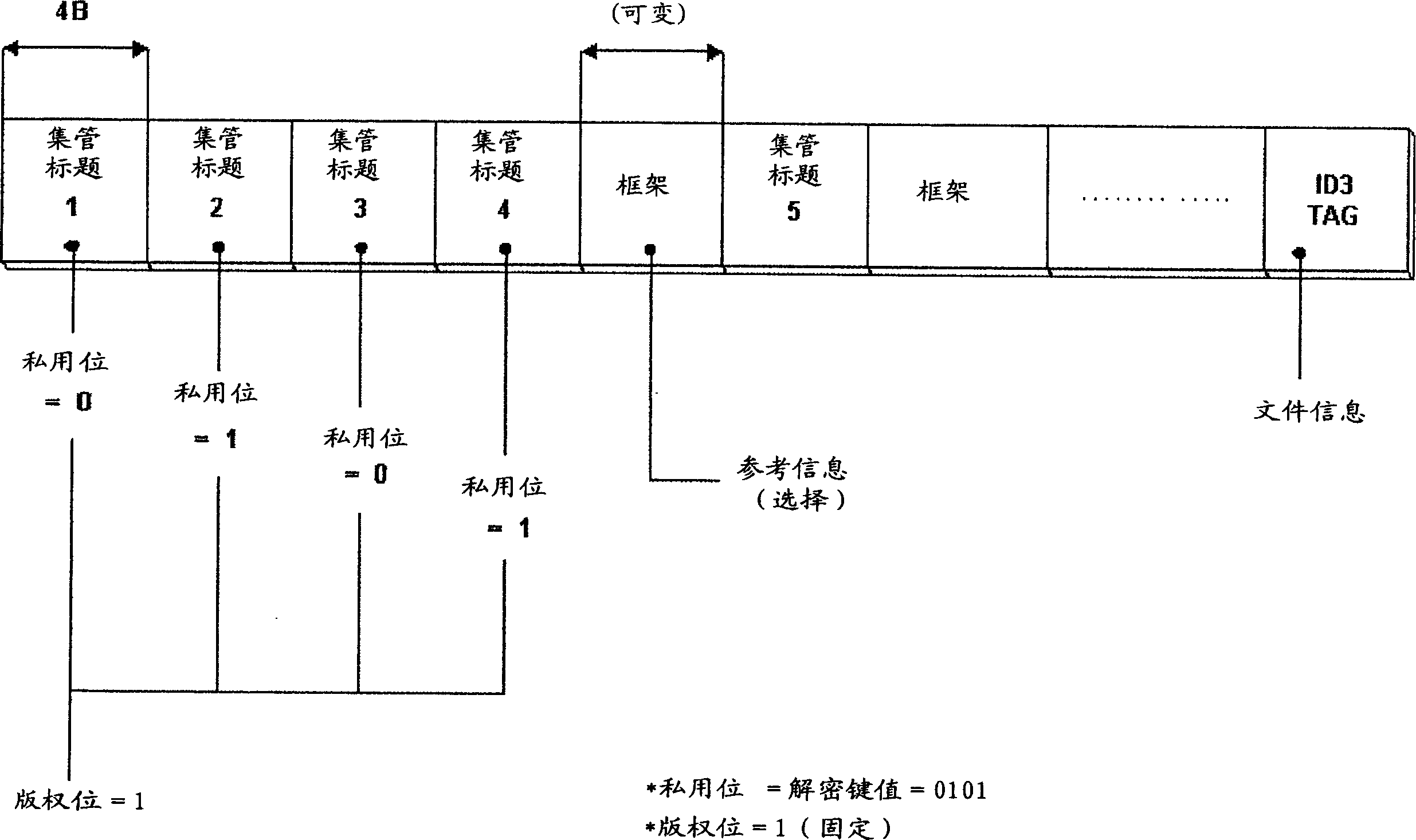
[0027] According to the decryption key method according to the present invention, the encrypted compressed audio data is recorded in the above-mentioned frame field, and the decryption key for decryption will be distributed and recorded in several header records recorded in the front area of the MP3 audio file, in p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com