Binding by hash
A hashing and assembly technology, applied in the field of component integrity systems and tools, can solve problems such as damage to application software and hardware environments, failure to protect application version upgrades, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
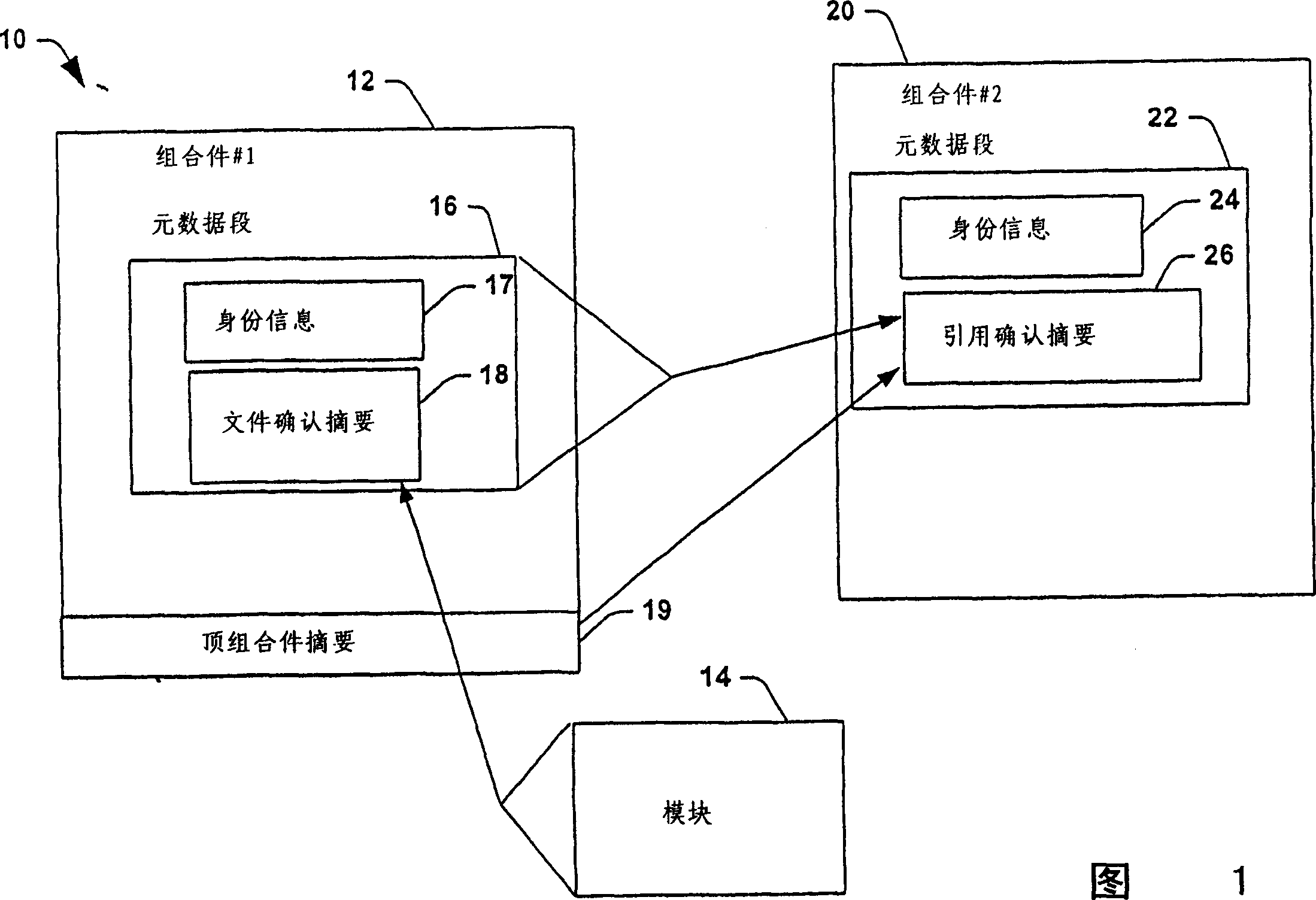
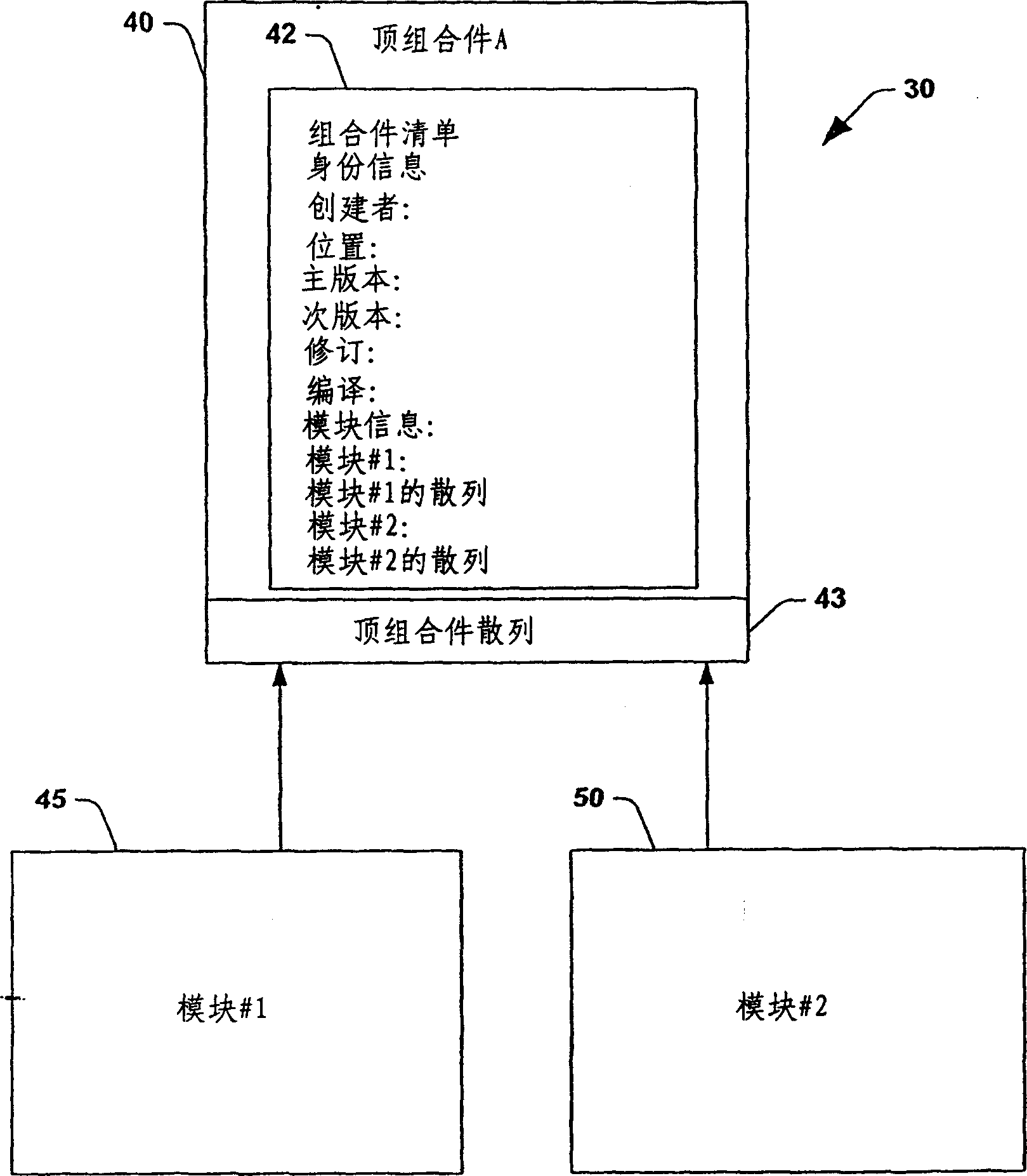
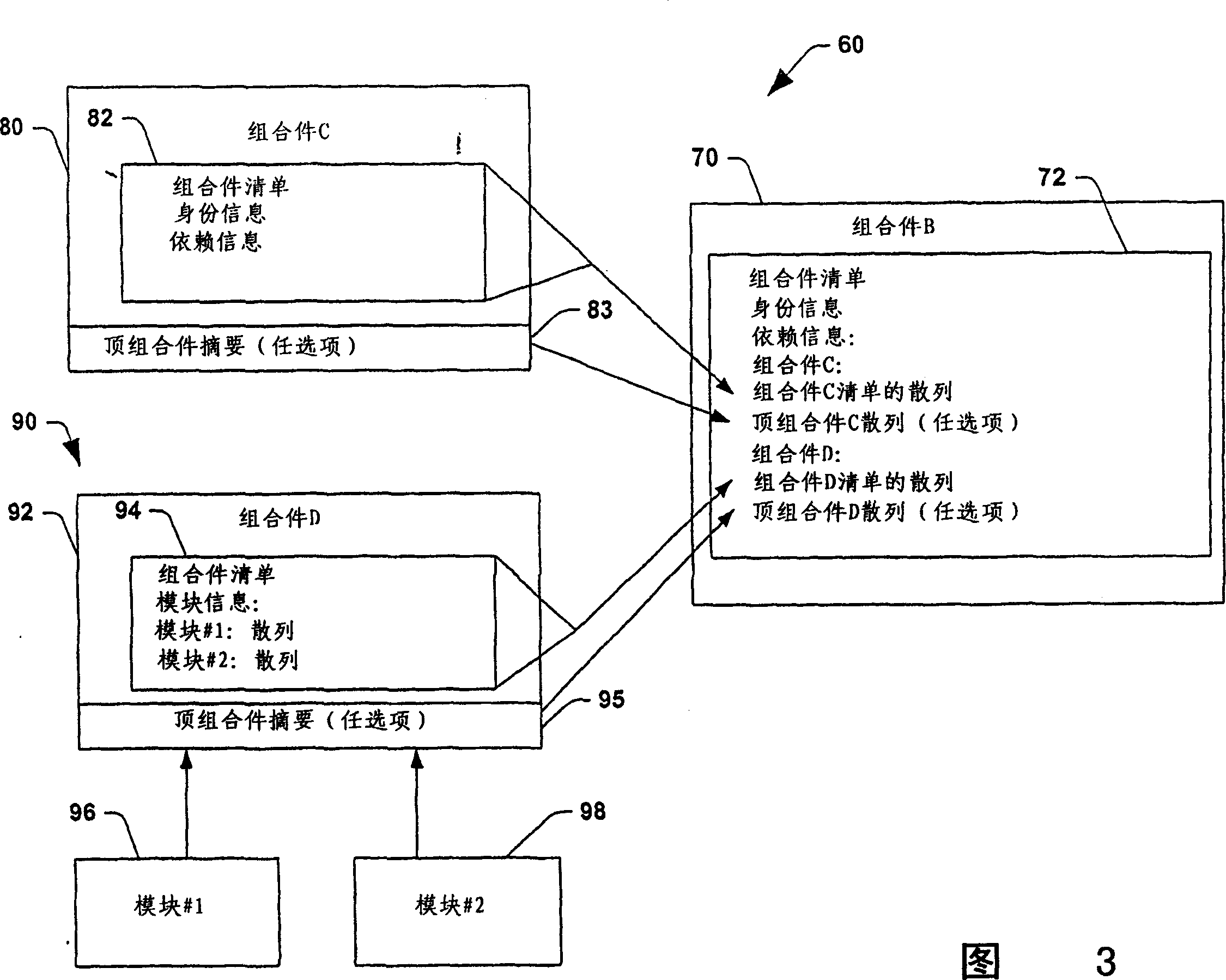
[0024] The invention will now be described with reference to the drawings in which like reference characters correspond to like elements throughout the specification. The present invention is by reference to a system and method that facilitates the integrity of components used by applications during runtime. These components are usually dynamic-link libraries (DLLs), but can also include definition files, description files, and executable files that are linked to the application at runtime. An assembly in accordance with at least one aspect of the subject invention is defined herein as components that include metadata defining the assembly, metadata describing the components that make up the assembly, and metadata describing the assemblies on which the assembly depends . The present invention uses cryptographic techniques, such as hashing, to ensure the integrity of assemblies used by applications. In addition, the present invention allows a large DLL file to be divided into...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com