Method of isolation of bilayer VLAN port
A port isolation and port technology, applied in data exchange through path configuration, digital transmission system, electrical components, etc., can solve the problems of wasting user bandwidth, enlarging the broadcast domain, reducing security and reliability, etc., to improve security performance, the effect of increasing the communication rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
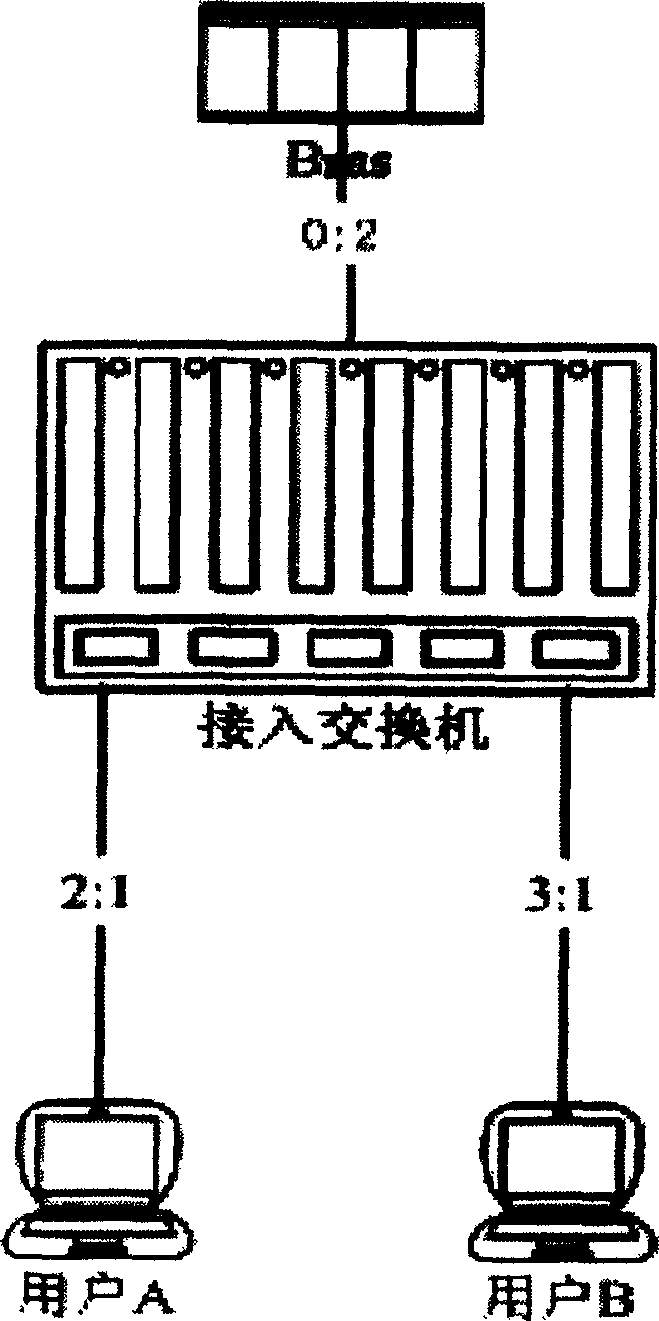
[0014] The present invention realizes the isolation of two-layer VLAN ports in this way: a user port restriction module is added to the FPGA on the VLAN service board, and the user port restriction module is used to restrict downlink broadcasting to users;
[0015] The service board receives the downlink message from the main control board, if the message is a broadcast message (ARP request, etc.), it discards it; if it is a unicast message, it releases it. The isolation user port restriction module of the present invention judges the message specifically by marking the VLAN port bitmap, that is, the broadcast domain position of the port is zero, and the port prohibits downlink broadcasting. Broadcast packets such as ARP requests from other port users to this port user are discarded, which not only controls invalid broadcasts, but also realizes isolation between users. Moreover, the user port restriction module of the present invention will not affect the passage of other mess...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com