Concealed-enciphering machine-reading anti-fcke method for holographic mobile database
A mobile database and database technology, applied in the direction of electrical digital data processing, special data processing applications, computer parts, etc., can solve the problems of single pattern, easy to decipher anti-counterfeiting combination, loss of anti-counterfeiting, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
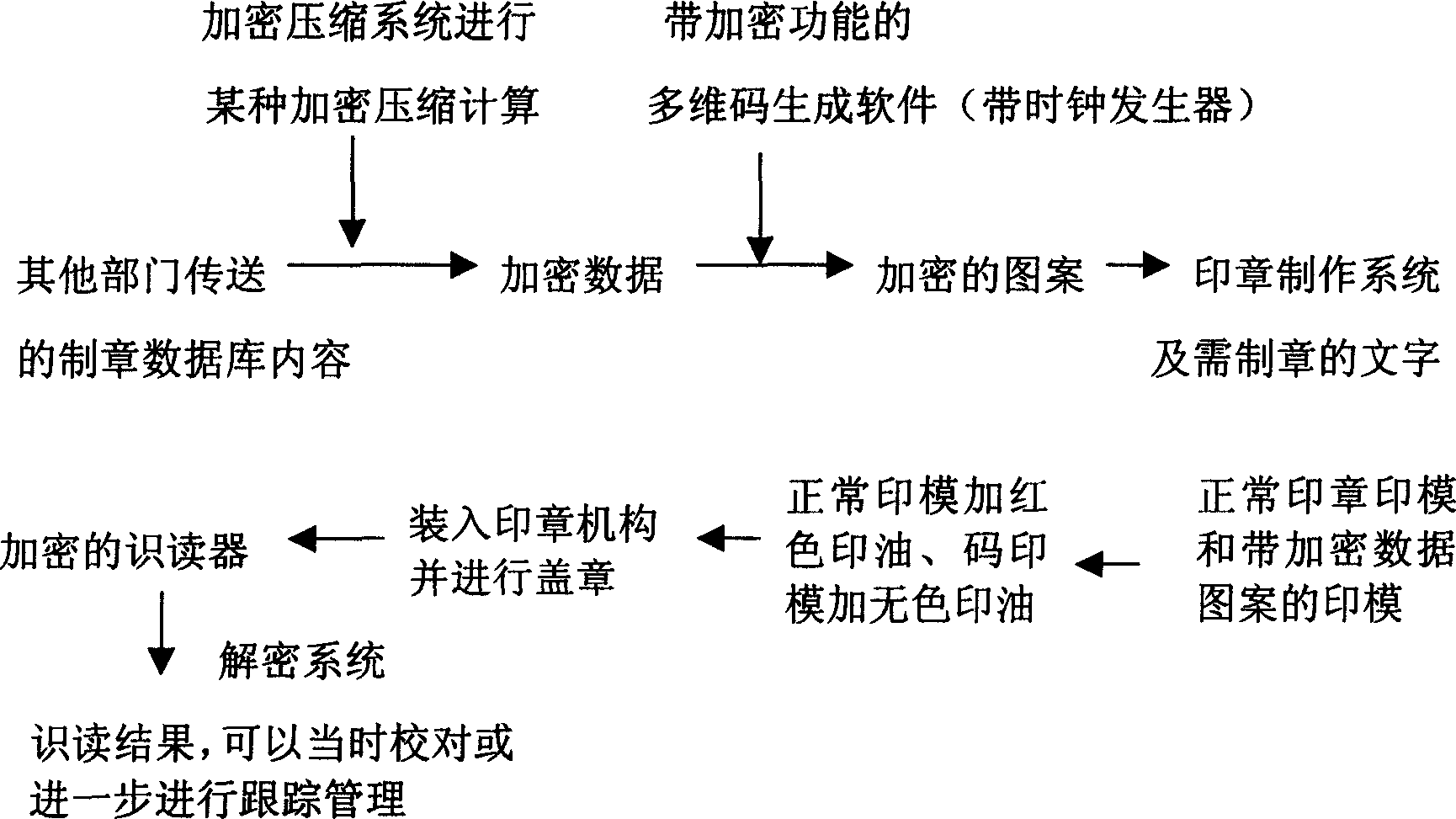
[0009] Anti-counterfeiting of the seal: the anti-counterfeiting seal of the present invention has an invisible holographic mobile database. The anti-counterfeiting seal and graphics generated by this technology are completely different from the traditional anti-counterfeiting technology. It not only has patterns and text, but also can be: photos, fingerprints, All digitizable information such as palm prints, signatures, sounds, texts, etc. The specific content of the invisible holographic self-contained mobile database is determined by the requirements of the user or the application field. The holographic self-contained mobile database is movable, and the seal transferred by the seal can still be reliable under less than 50% damage or defacement Obtain all the information of the seal accurately and accurately. This is the most fundamental requirement for the anti-counterfeiting and digitalization of the seal. The characteristics of the seal itself are that it is impossible to guar...
Embodiment 2
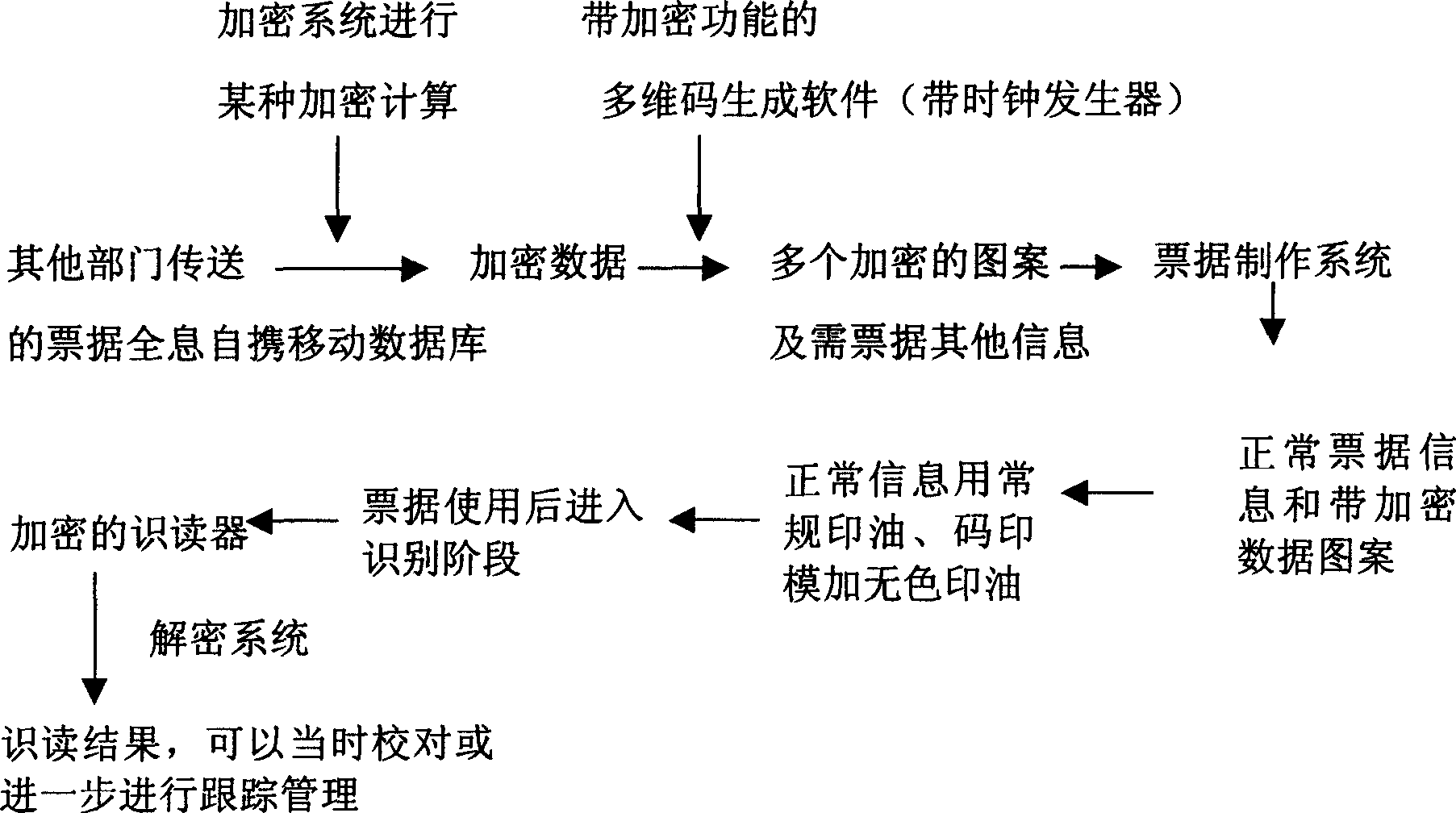
[0016] Anti-counterfeiting of bills: bills contain not only patterns and texts, but also photos, fingerprints, palm prints, signatures, sounds, texts and other digitized information. The specific content of the invisible holographic self-carried mobile database is determined by the requirements of the user or application field. The characteristics of the self-contained mobile database are determined by the characteristics of the bill itself. This holographic self-contained mobile database is movable. The carrier of the database-the anti-counterfeiting pattern in the bill can still be reliably damaged or defaced under the condition of less than 50% , Accurately obtain all the information of the carrier.
[0017] The content of the holographic self-portable mobile database of the bill is encrypted by the current 128-bit digital certificate. In order to realize the holographic self-portable mobile database on the bill, multi-dimensional codes (one-dimensional code, two-dimensional co...
Embodiment 3
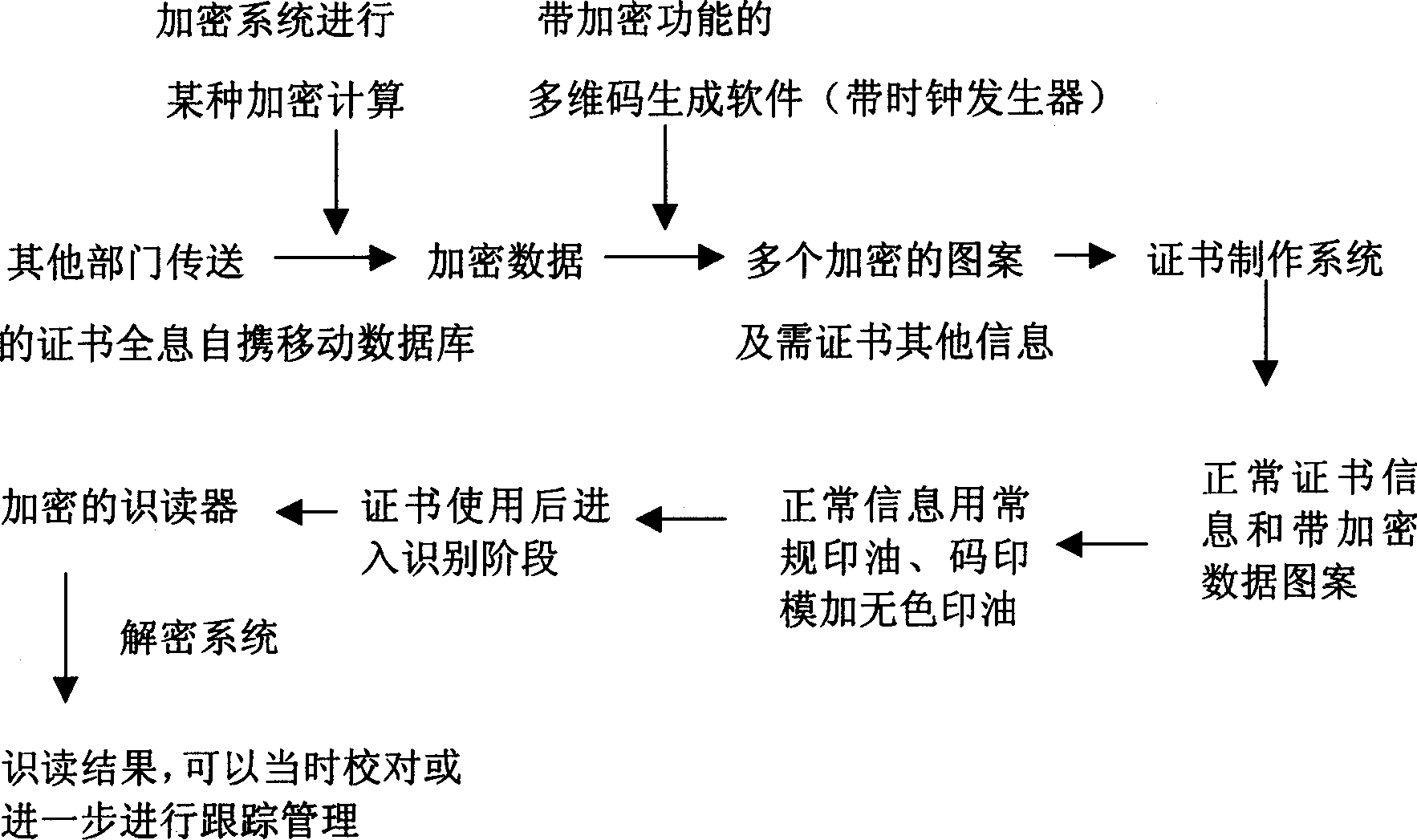
[0024]The anti-counterfeiting method of the certificate: There are not only patterns and words in the certificate, but also all digitized information such as photos, fingerprints, palm prints, signatures, sounds, and words. The specific content of the invisible holographic self-carried mobile database is determined by the requirements of the user or application field. The characteristics of the self-contained mobile database are determined by the characteristics of the certificate itself, and the holographic self-contained mobile database is movable. This can greatly expand the information form and volume of traditional certificates. The holographic self-carrying mobile database means that the anti-counterfeiting pattern in the database carrier-certificate can reliably and accurately obtain all the carrier's information even when less than 50% is damaged or defaced. This is the most fundamental requirement for certificate anti-counterfeiting electronic and digitalization. Because ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com