Safety protection module of mobile communication equipment and its processing method
A mobile communication device, a trusted technology, applied in electrical components, transmission systems, etc., can solve problems such as fragility, and achieve the effects of accurate and credible results, guaranteed process, and convenient implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] The present invention will be described in further detail below in conjunction with the accompanying drawings.
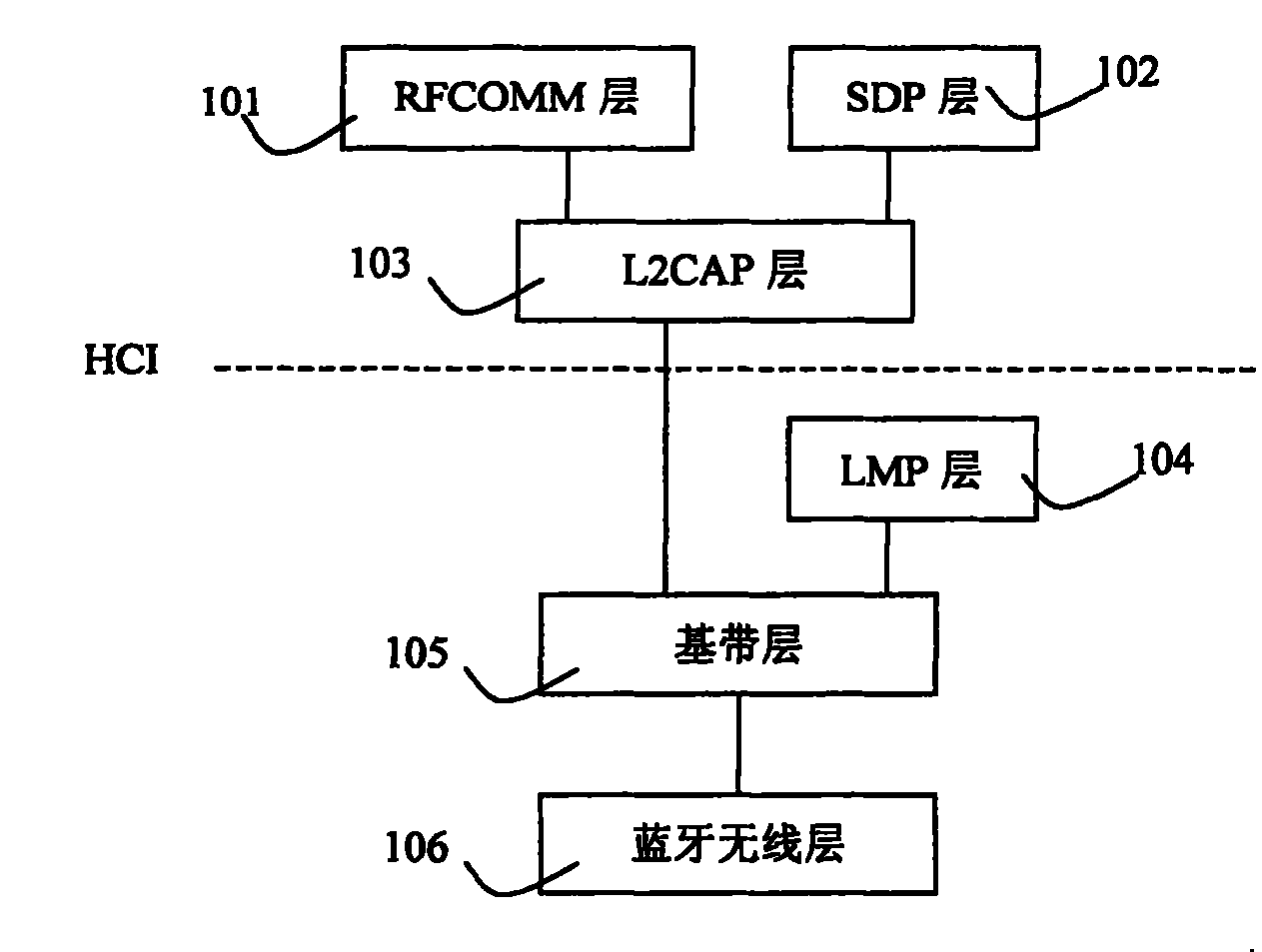
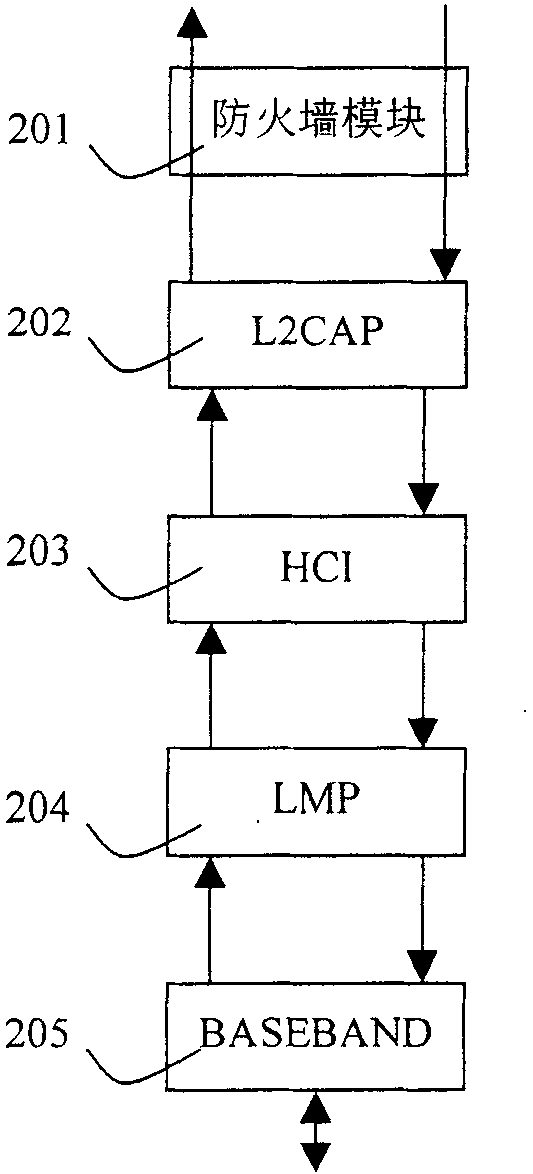
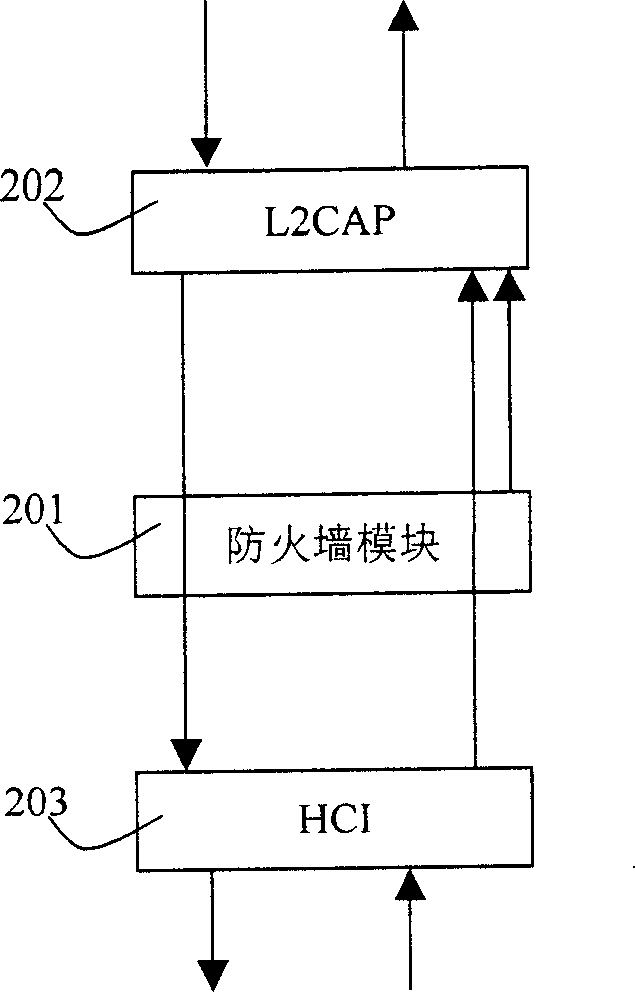
[0012] The invention inserts a firewall module in the bluetooth device. Figure 2A What is shown is that when the Bluetooth device is used as a slave unit, the insertion position of the firewall module 201 is at the upper layer of the Logical Link Control and Adaptation Protocol (L2CAP) 202, and the following are the basic modules of the Bluetooth device: Host Control Interface (HCI) 203 , link management layer (LMP) 204 , baseband layer (BASEBAND) 205 . This structure is mainly to prevent unknown nodes from attempting to make illegal connections and steal local data. After receiving the L2CA_ConnectInd (connection) event from the L2CAP layer 202, the firewall module 201 filters and analyzes the data packet, confirms whether it is a trusted node, and sends L2CA_ConnectRsp (permission) or L2CA_ConnectRspNeg (forbidden) to the L2CAP layer 202 according to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com