Method for realizing encrypting
An encrypted and encrypted device technology, which is applied in the field of information security, can solve the problems that it is impossible to avoid impersonating signatures or tampering with signature content, it is impossible to see the content to be encrypted, and tamper with user signatures, etc., so as to avoid impersonating signatures or tampering with signature content Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described in detail below in conjunction with the drawings and specific embodiments.
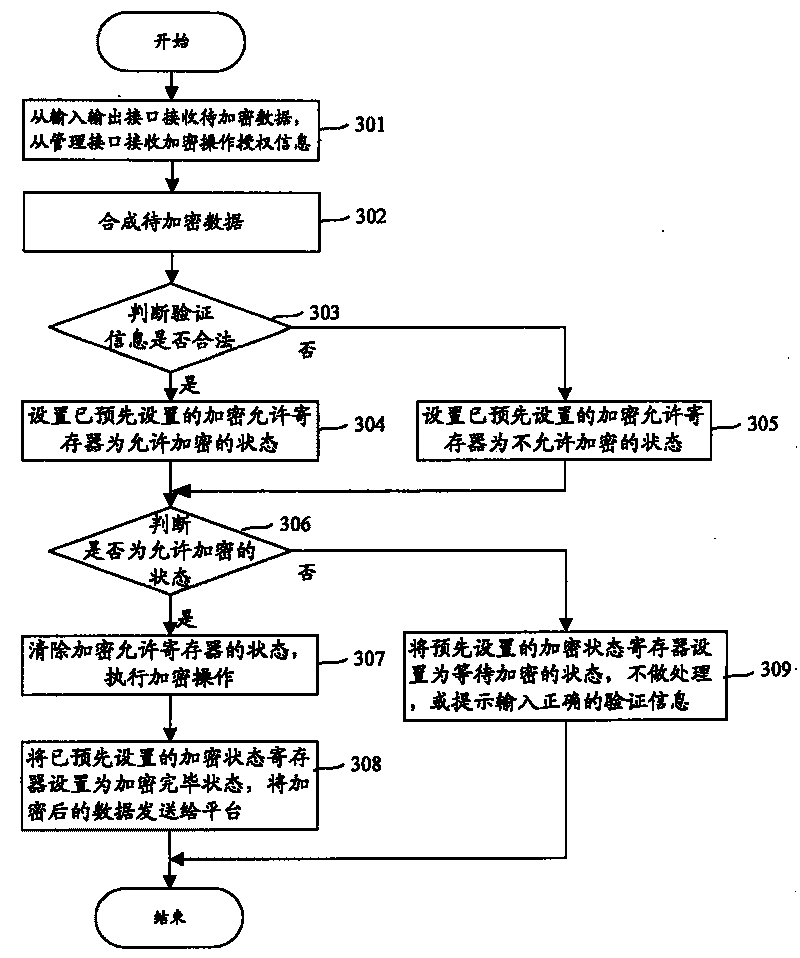
[0046] image 3 Shown is a schematic diagram of the process of implementing encryption by applying the present invention.
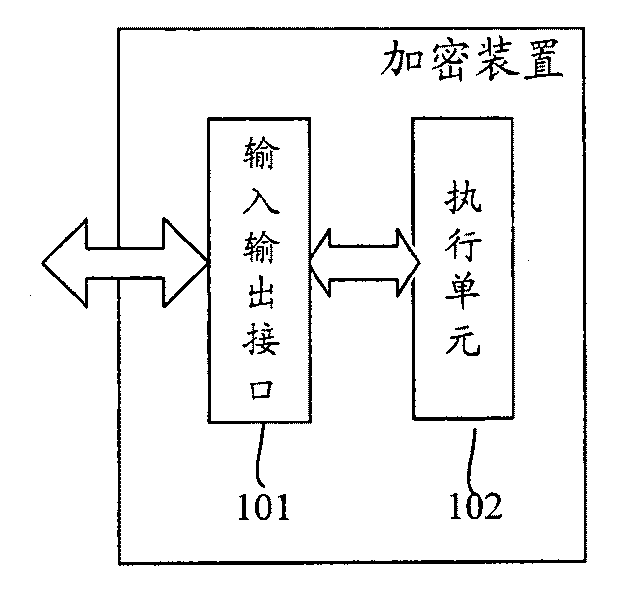
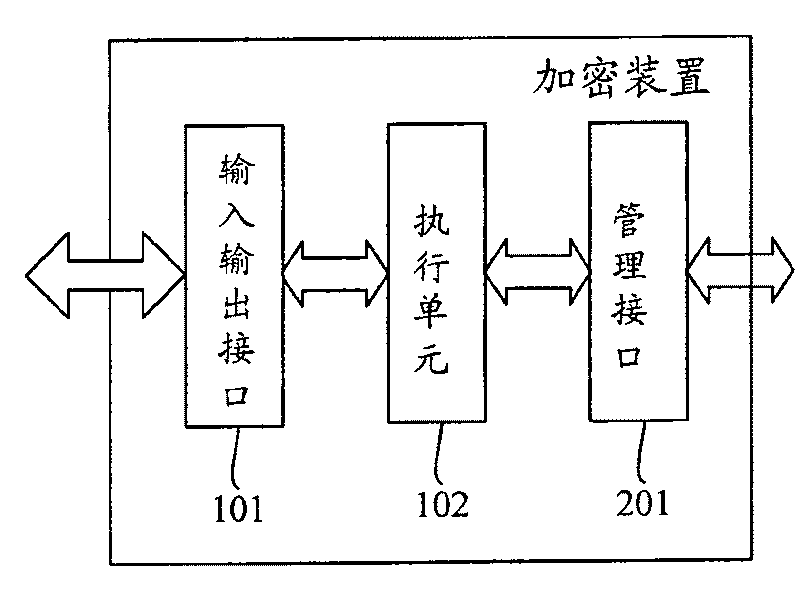
[0047] Step 301: The encryption device receives part of the data to be encrypted from the input and output interface, and receives the encryption operation authorization information containing the data elements to be encrypted from the management interface. The above part of the data to be encrypted is usually in plain text.
[0048] Step 302: The execution unit in the encryption device extracts the data element to be encrypted from the encryption operation authorization information, combines the data element to be encrypted with the received part of the data to be encrypted, and synthesizes the complete data to be encrypted.
[0049] Of course, the encryption operation authorization information can further include constraint condit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com