Method for enabling a trusted dialog for collection of sensitive data
a trusted dialog and data technology, applied in the computer field, can solve the problems of insufficient methods and programs to prevent a rogue application from spoofing the appearance of a legitimate or trusted application, affecting the security of both the software platform and the user's sensitive data, and increasing the importance of protecting such data from exploitation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] Reference will now be made in detail to the presently preferred embodiments of the invention, examples of which are illustrated in the accompanying drawings.
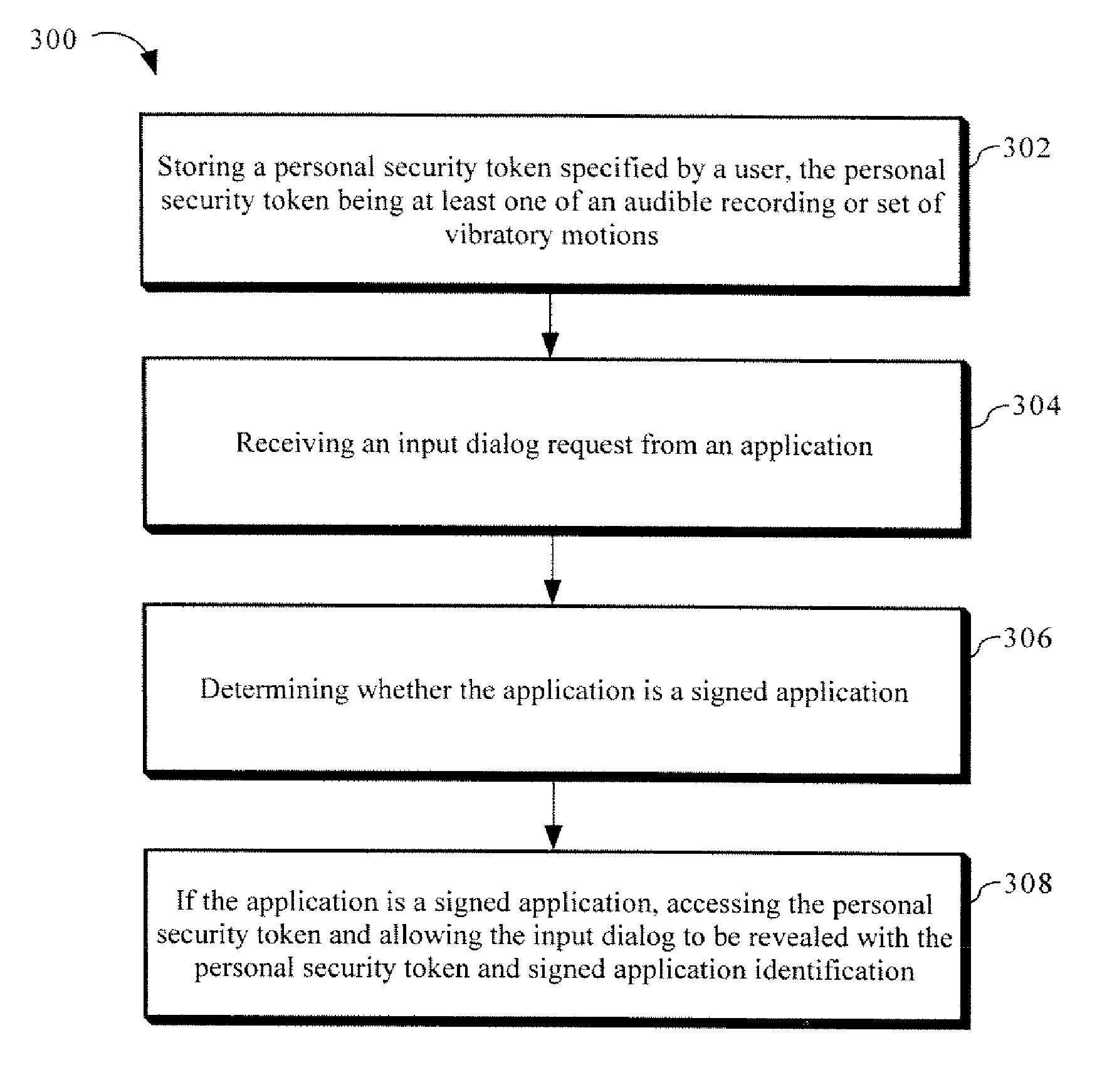
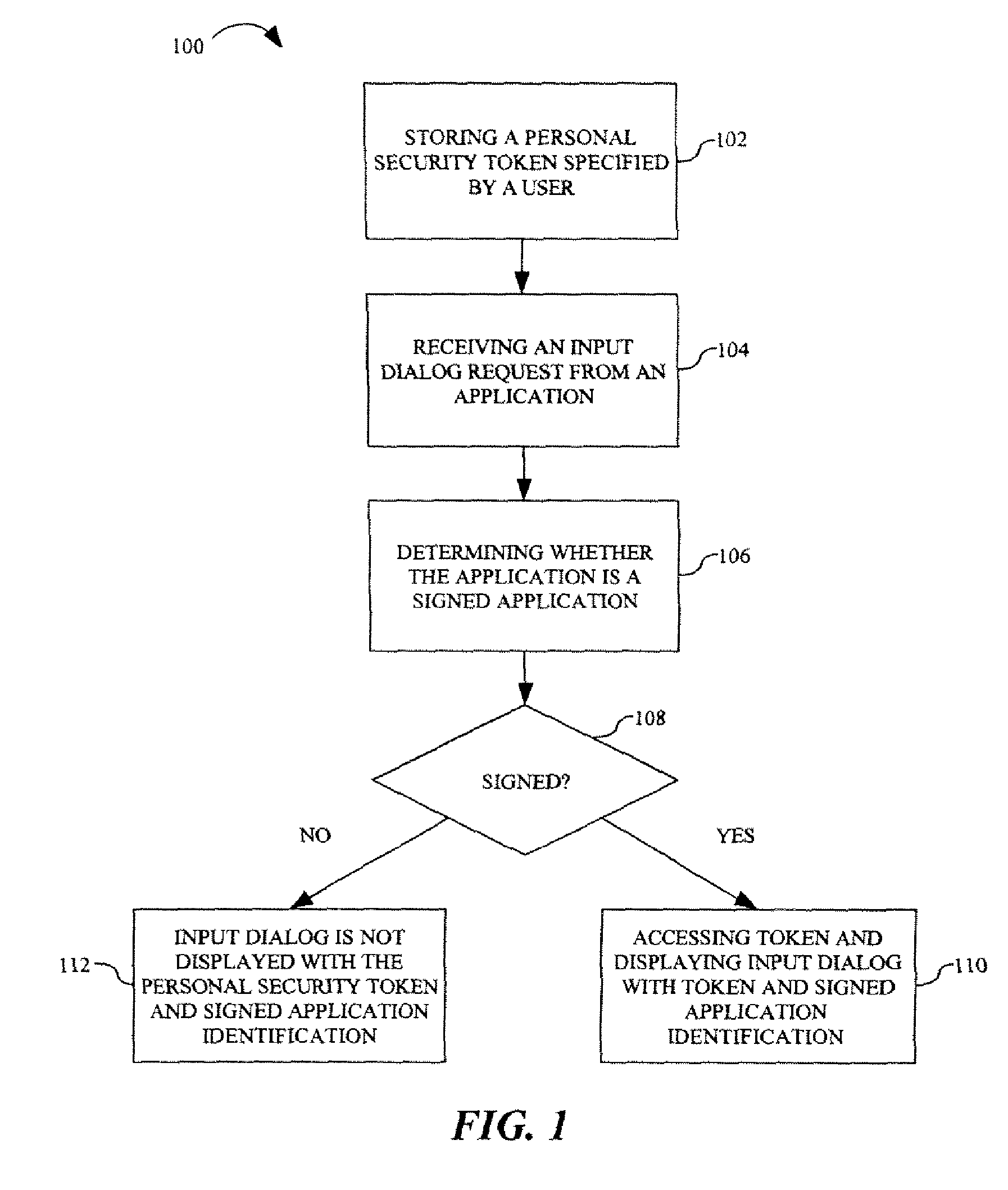
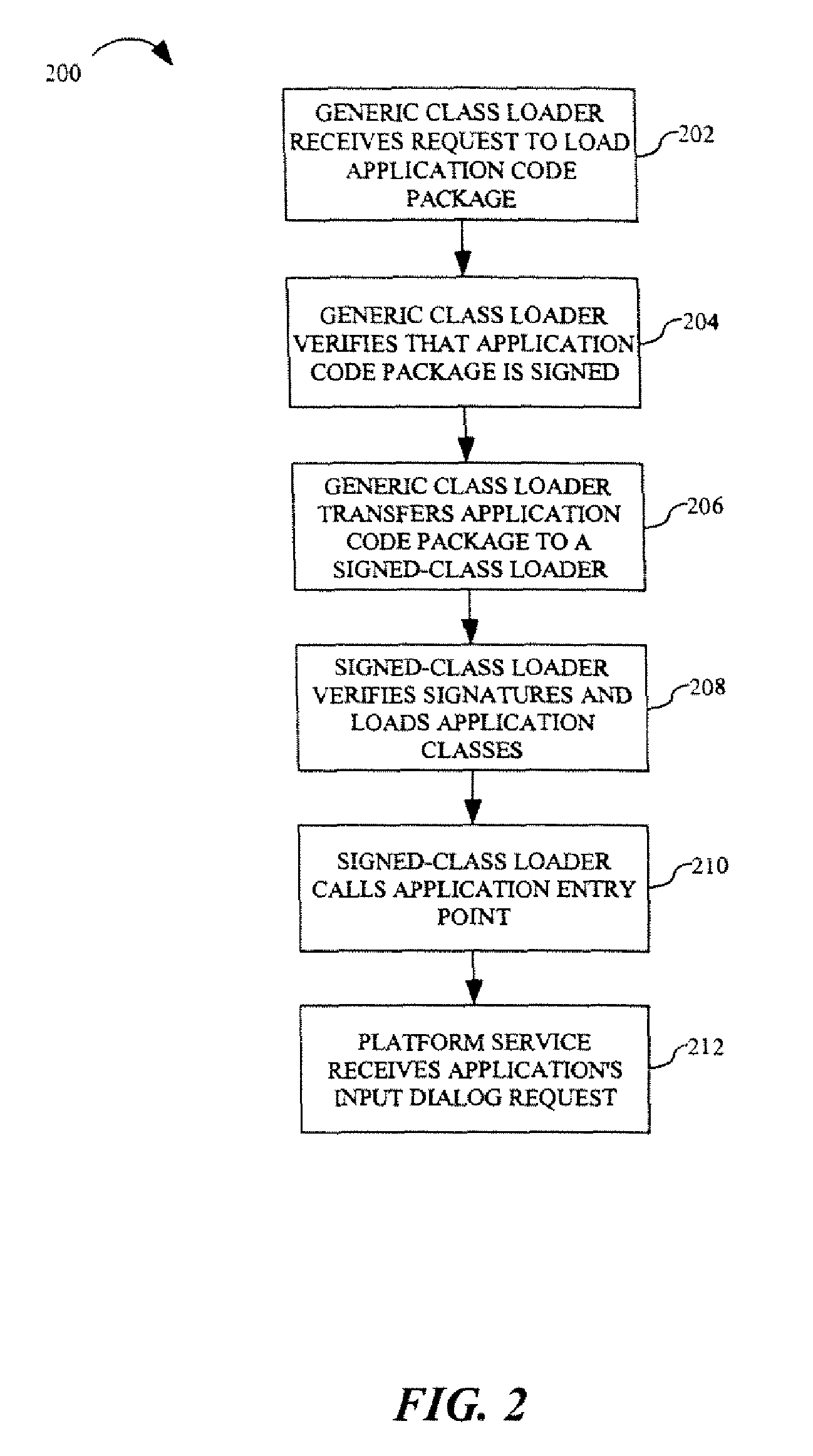
[0014] Referring to FIGS. 1 and 2, a method for enabling a trusted dialog for collection of sensitive data in accordance with an embodiment of the present invention is discussed. The method 100 includes storing a personal security token specified by a user 102. In a present embodiment, a user of a computing device, such as a personal computer, personal digital assistant (PDA) and the like, during initial setup / login, is asked by the software platform of the computing device to enter or select a personal security token. For example, the software platform may cause a message or prompt to be generated and displayed on a display screen of the user's computing device asking the user to enter a personal security token. The personal security token is selected by the user, via keyboard or mouse entry, and is stored by a platform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com