Method of Encrypted Communication with Restricted Rate of Stored Encryption Key Retrievals
a technology of encrypted communication and encryption key, applied in the field of secure communication, can solve the problems of home refill operation or clone manufacture in countries with weak industrial property protection, consumer to blame system manufacturer and not admit the use of non-authorized consumables, and slightly complicate matters, so as to frustrate the attacker and reduce nois
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0106]Particular embodiments of the invention will now be described with reference to the Applicant's Memjet™ printing system. However, the skilled worker will understand that the invention is not restricted to use in a printing system and may be employed in a wide range of applications requiring encrypted communication and authentication of related entities.
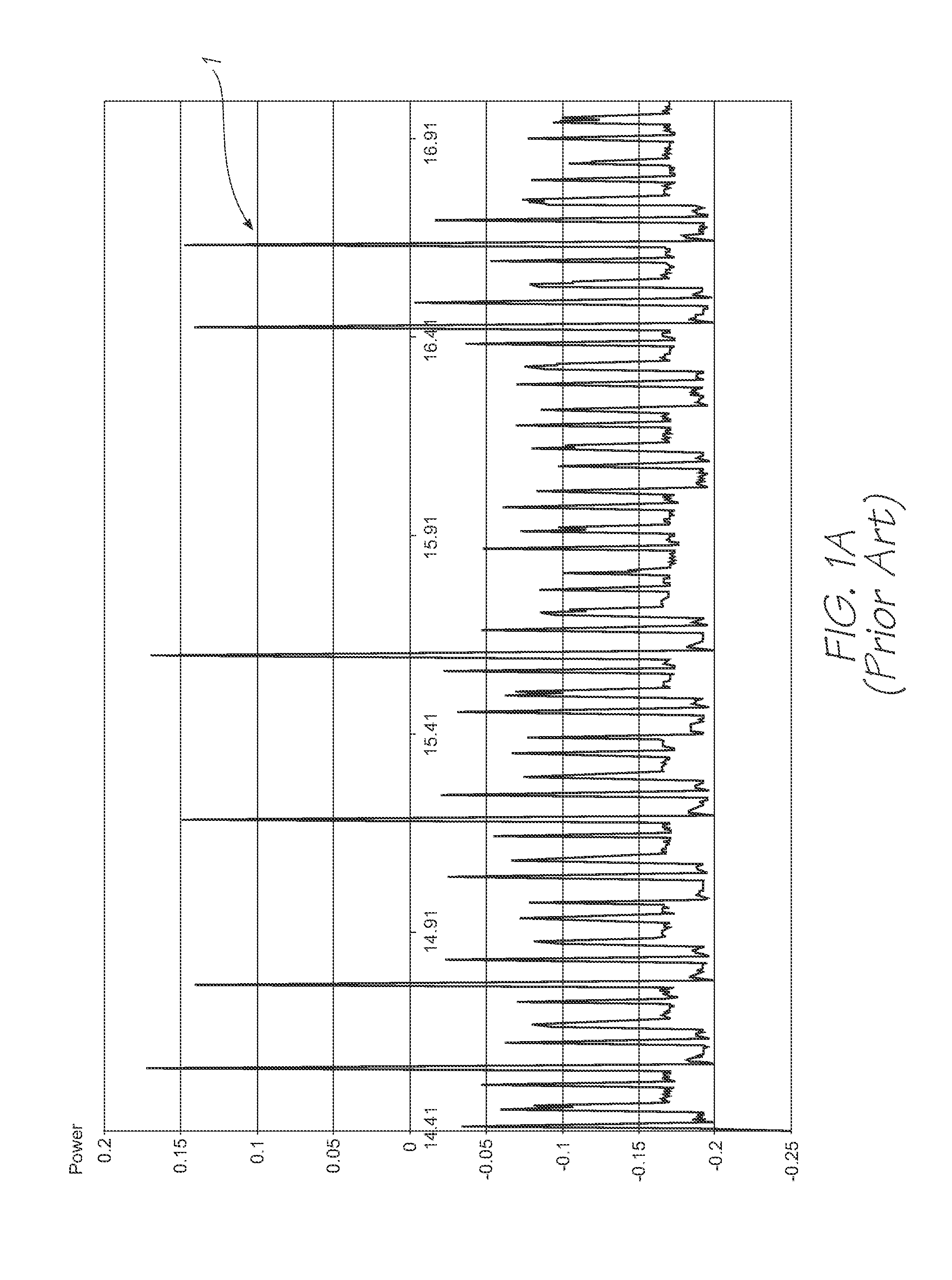
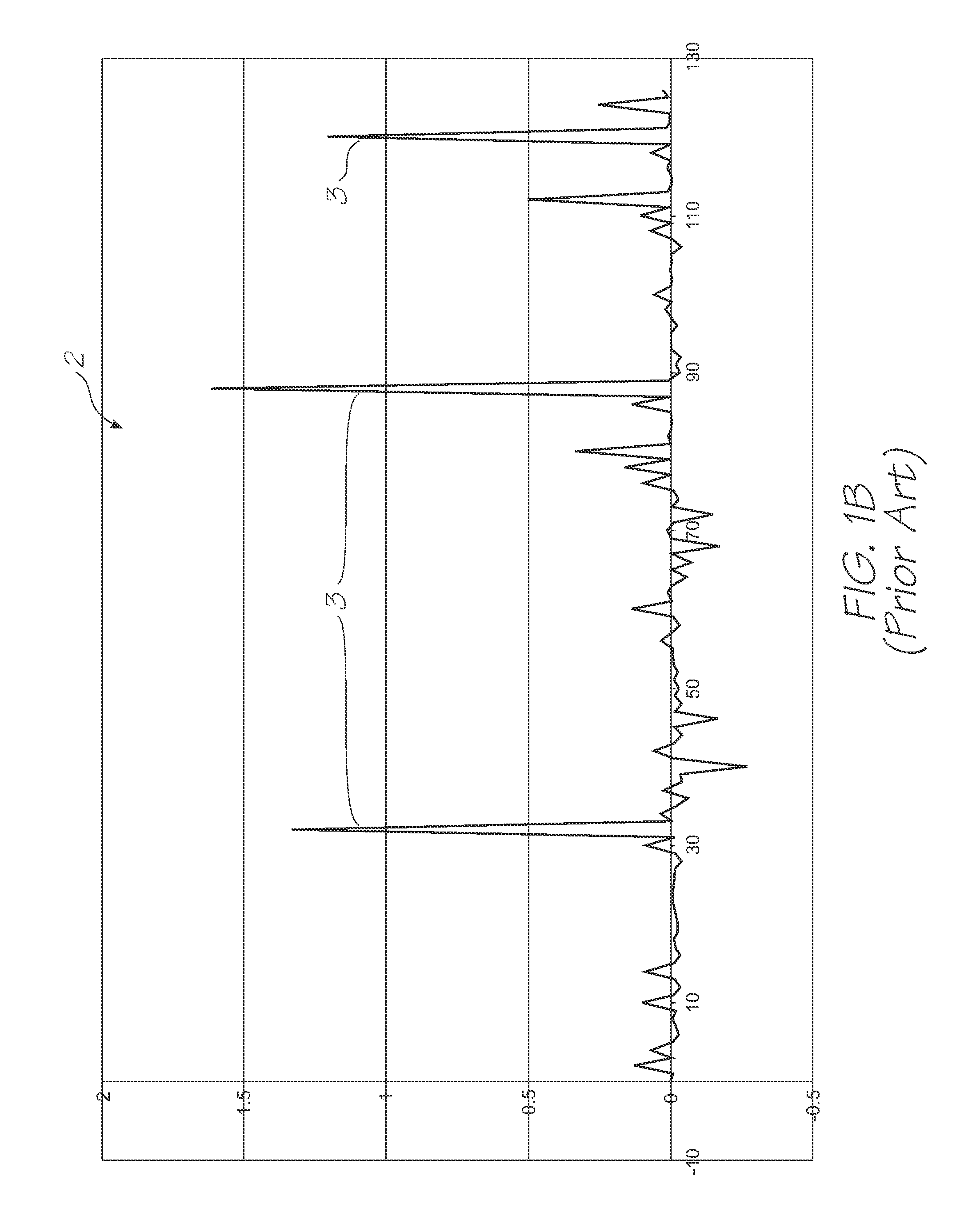
Side Channel Behaviour of Prior Art QA Chip
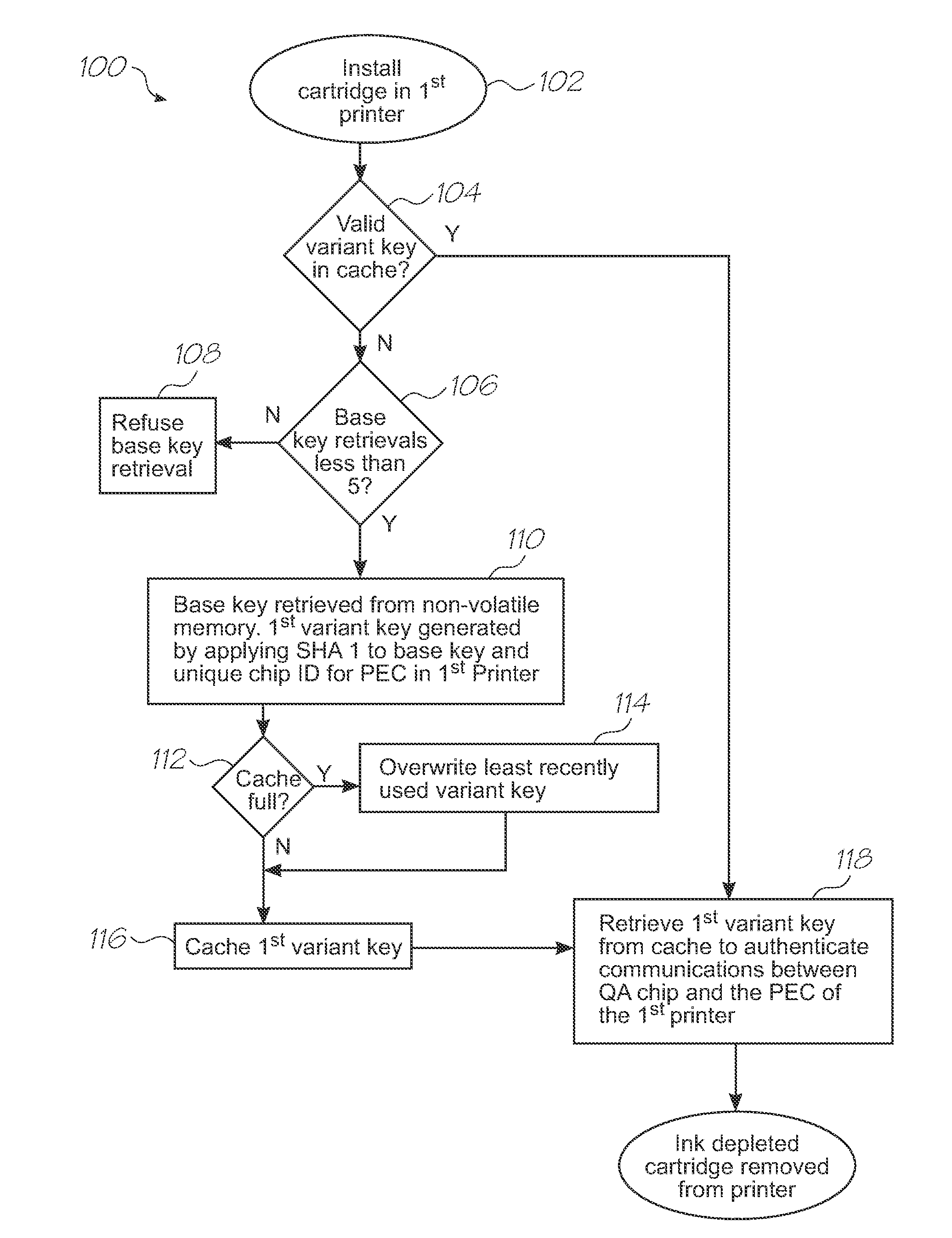
[0107]The invention builds on the key management mechanisms presented in U.S. Pat. No. 7,557,941 cross referenced above and therefore adheres to the same terminology. Each ink cartridge in a Memjet™ Printer contains a QA (Quality Assurance) Chip that stores and uses a valuable base key to authenticate itself to software running in the Print Engine Controller (SOPEC) chip. Compromise of this key would allow an attacker to build clone ink cartridges that are accepted by any printer of the appropriate model.
[0108]The prior art or unimproved QA Chip will, in response to an attacker's comman...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com