Authentication System
a technology of authentication system and authentication method, applied in the field of hardware verification, can solve the problems of affecting the mapping of challenges to responses of the puf or the attached integrated circuit irreversibly, affecting the response of the puf, and many lack the essential characteristics of an ideal pu
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
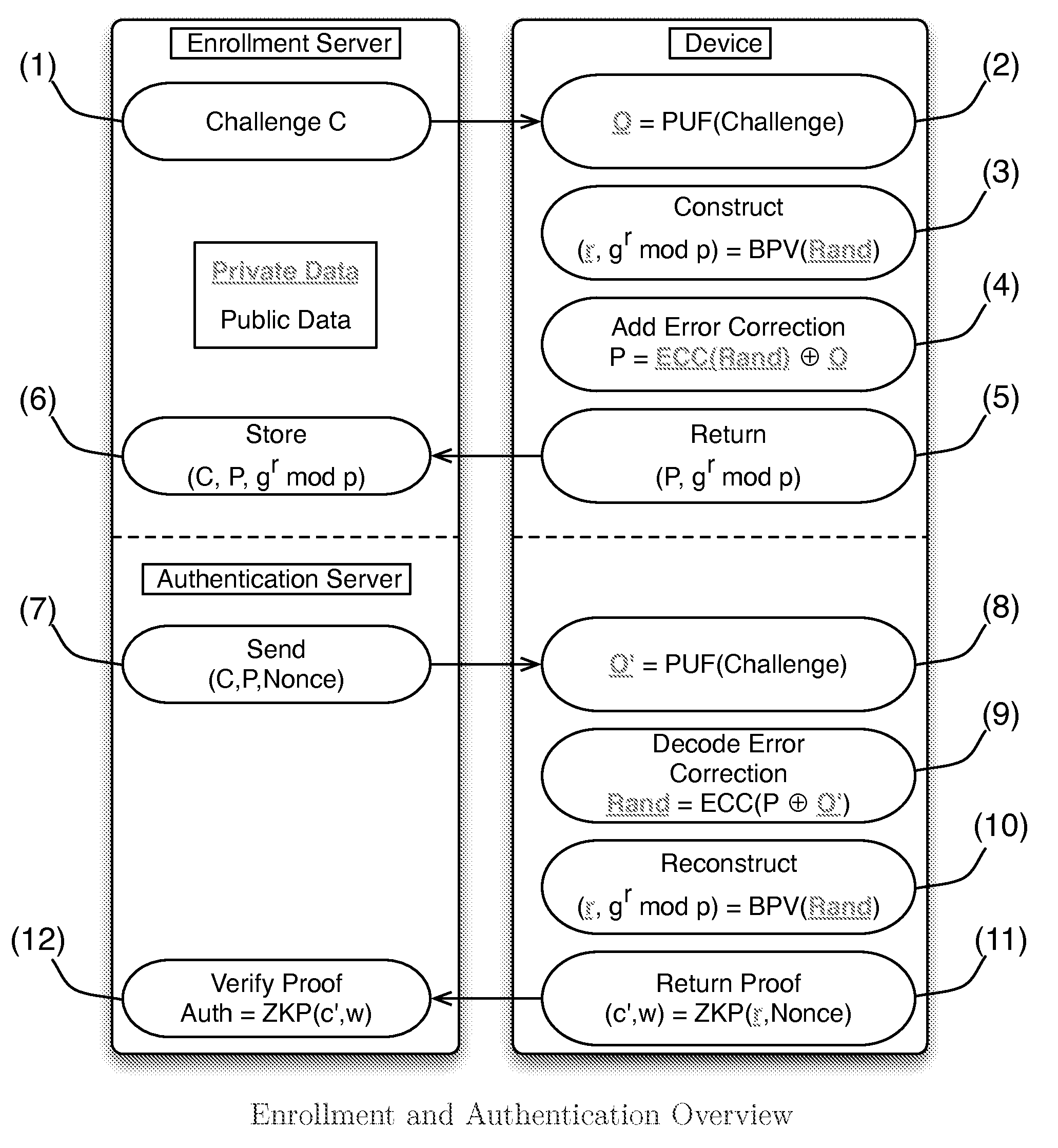
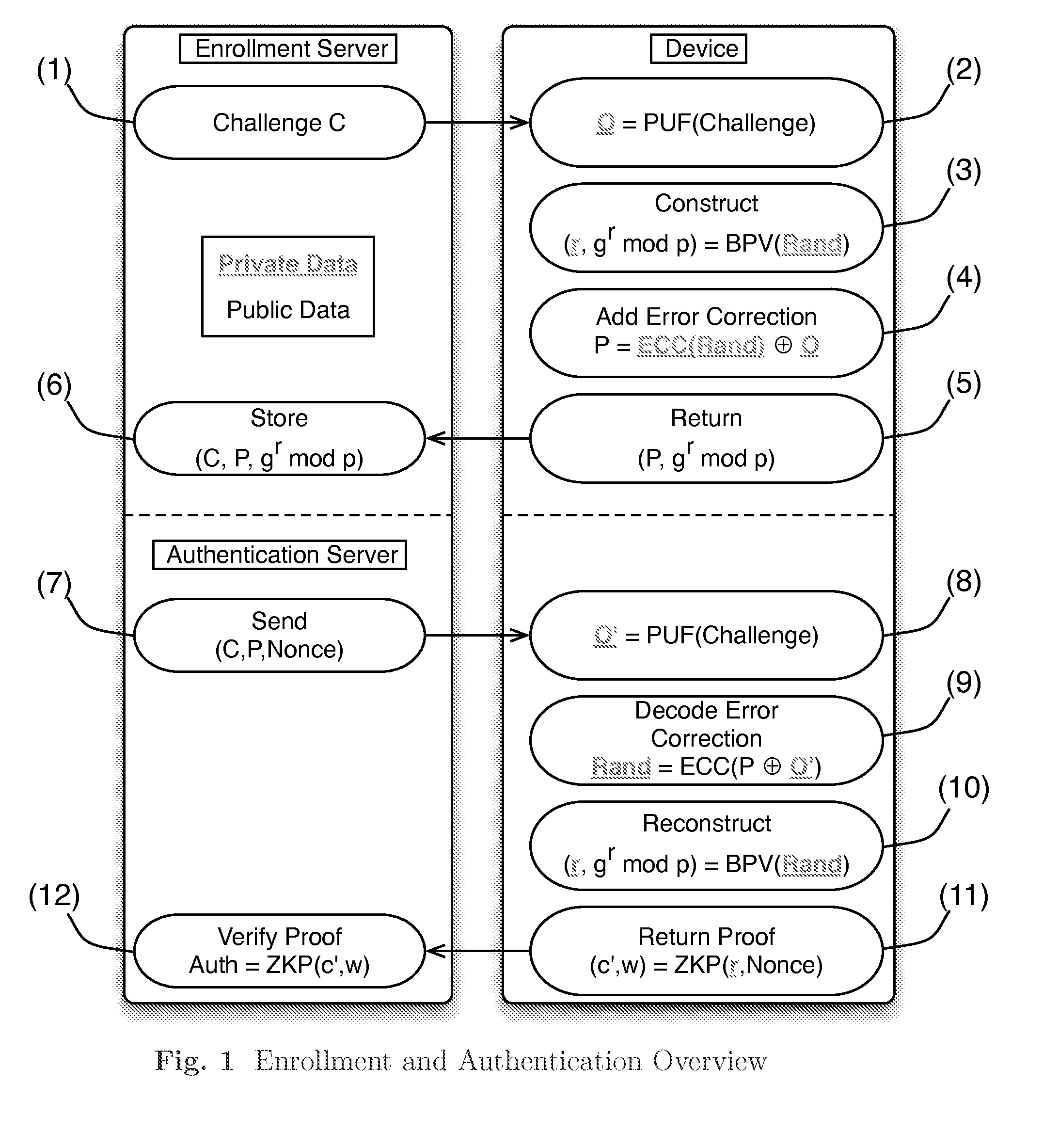
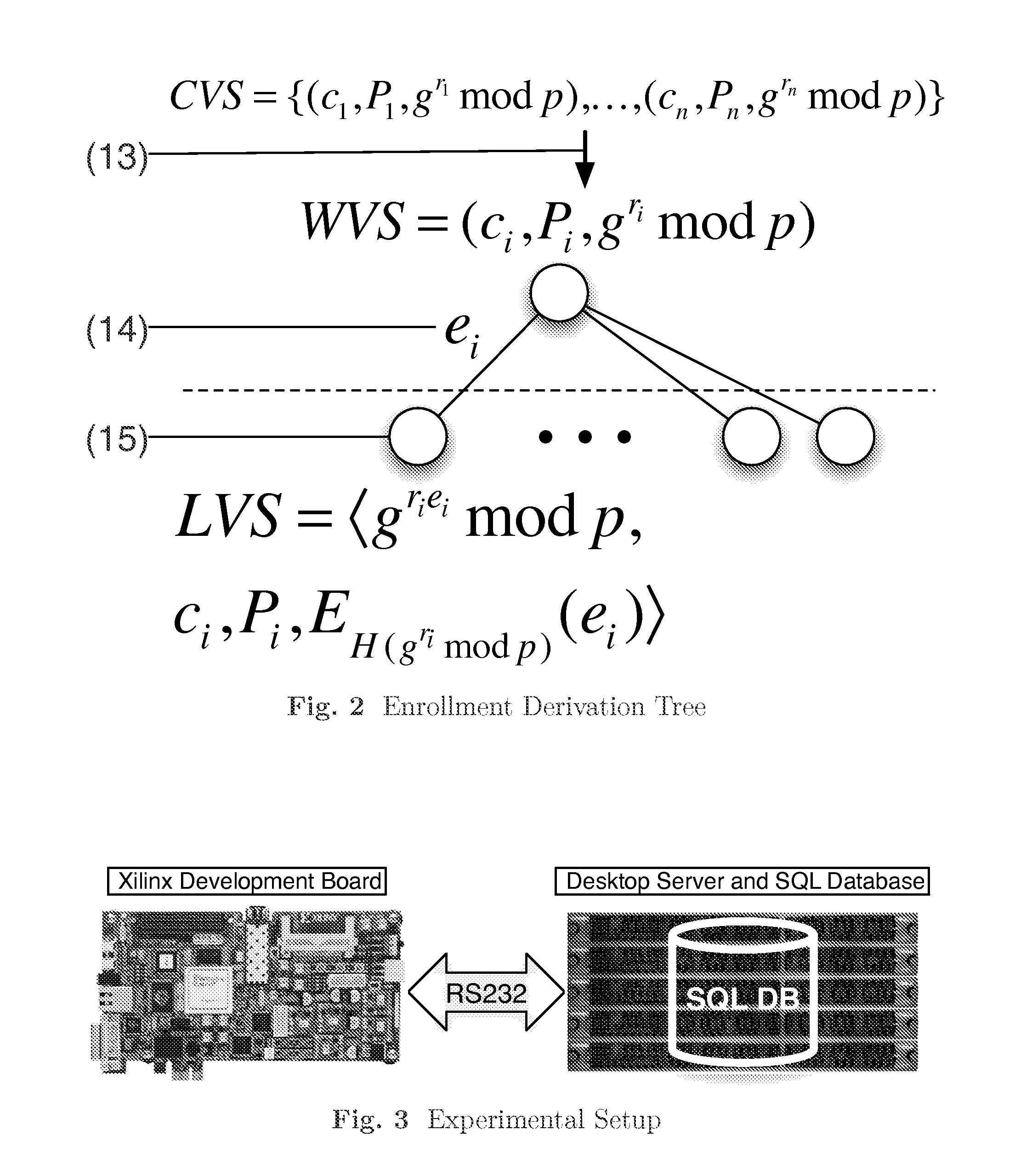
[0027]We review the enrollment and authentication protocols of Frikken et al. The authors consider PUF authentication in the context of banking authentication. The identity of banking clients is proved through a zero knowledge proof of knowledge, which demonstrates that the client knows a password and is in possession of a device capable of generating the discrete logarithm of a pre-enrolled group element. The construction is robust against many forms of attack, including device and server compromise by an adversary. Further, the construction is easily extended to support panic passwords, where authentication succeeds but the banking server is notified that the client was under duress. We build on a subset of the authors' construction in this work, removing the user and focusing only on authenticating the hardware.
[0028]We modify their protocol in two ways. First, we reduce the number of necessary modular multiplications, as the PUF itself resides on a resource-constrained device (i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com