Security element
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
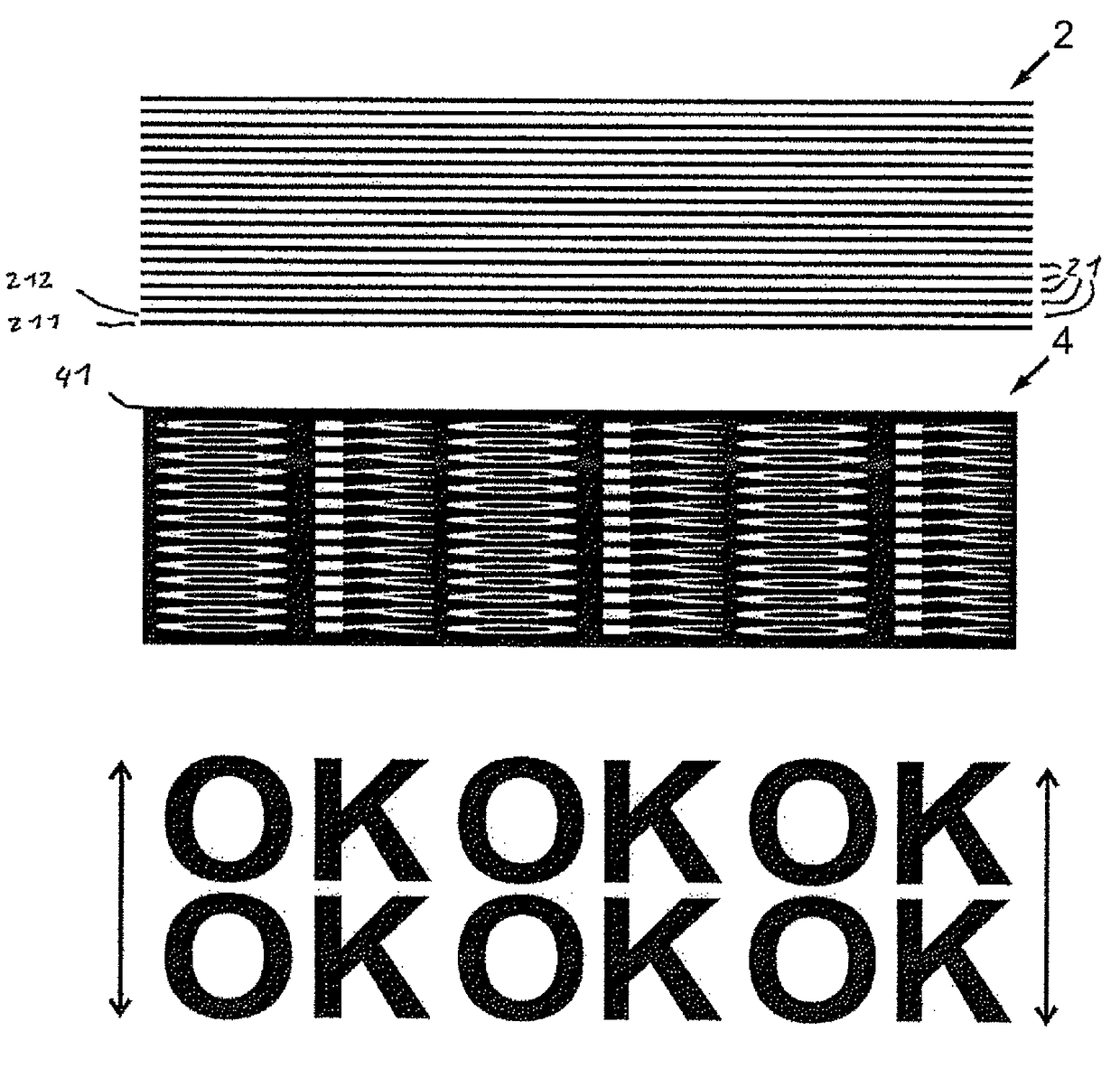
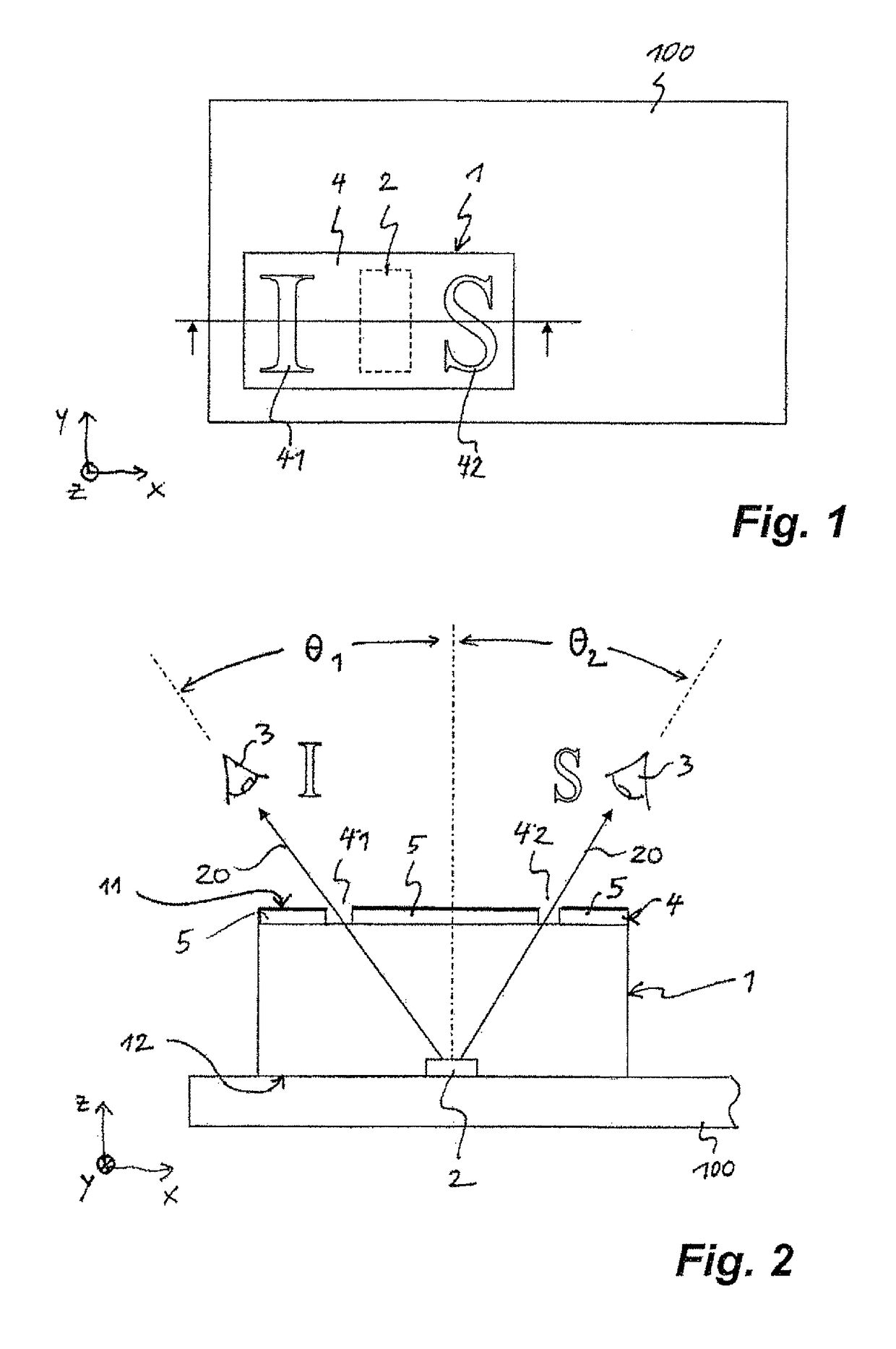
[0107]FIG. 1 shows a security document 100, attached to the viewing side of which there is a security element 1, which is intended to make falsification of the security document 100 more difficult. The security element 1 comprises a mask layer 4 that has transparent openings 41, 42 in the form of capital letters “I” and “S”, and a luminous layer 2 arranged between the mask layer 4 and the security document 100. The luminous layer has a rectangular outline, as viewed in the direction perpendicular to the xy plane, wherein the longer sides extend in the y direction.
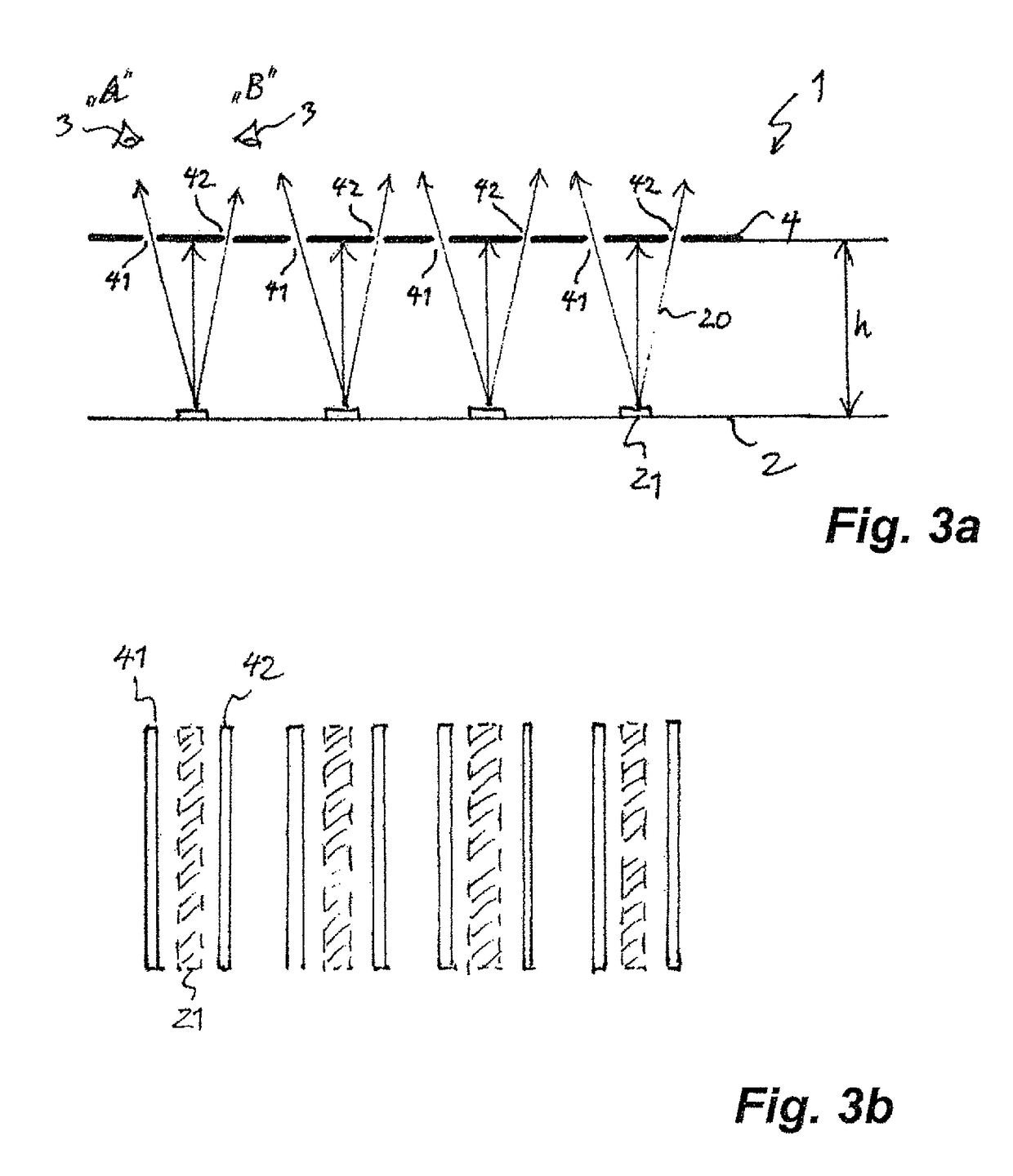
[0108]FIG. 2 shows a section through the security element 1, along the line II-II indicated in FIG. 1. The security element 1 is constituted by a flexible, multilayer foil body that is attached by its underside 12 to a side of the security document 100, e.g. affixed by means of an adhesive layer, and the viewing side 11 of which faces towards a viewer 3 of the security element 1. The foil body 1 comprises the luminous layer...
PUM
| Property | Measurement | Unit |
|---|---|---|
| Fraction | aaaaa | aaaaa |
| Fraction | aaaaa | aaaaa |
| Thickness | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com