Checkig method for protecting integrality of outline based on products of information technology of relational database
An integrity inspection and information technology technology, applied in the field of information technology product safety testing and evaluation equipment, which can solve problems such as difficulty in ensuring the consistency and scientificity of evaluation results, lack of strict evaluation process and methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
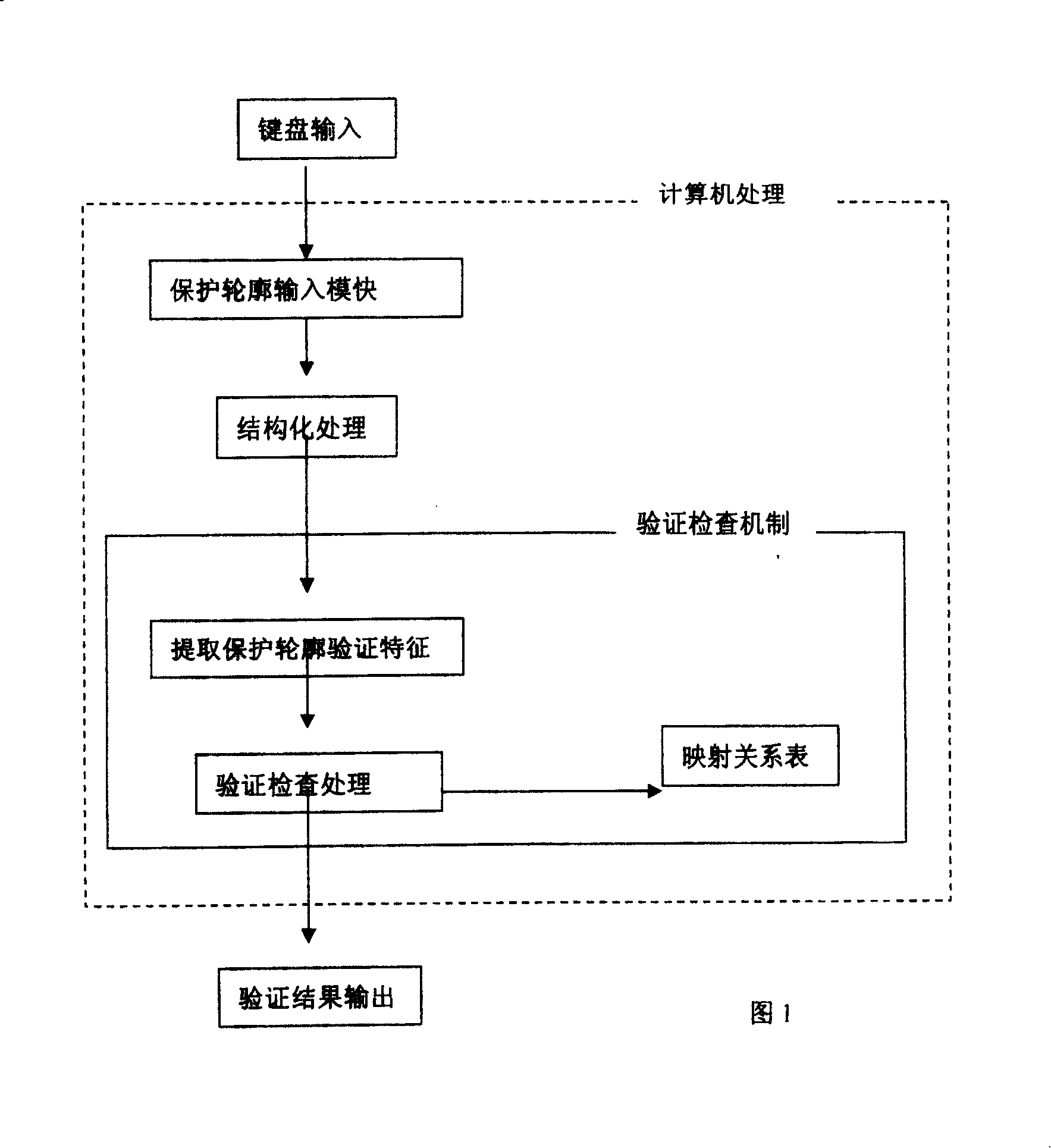
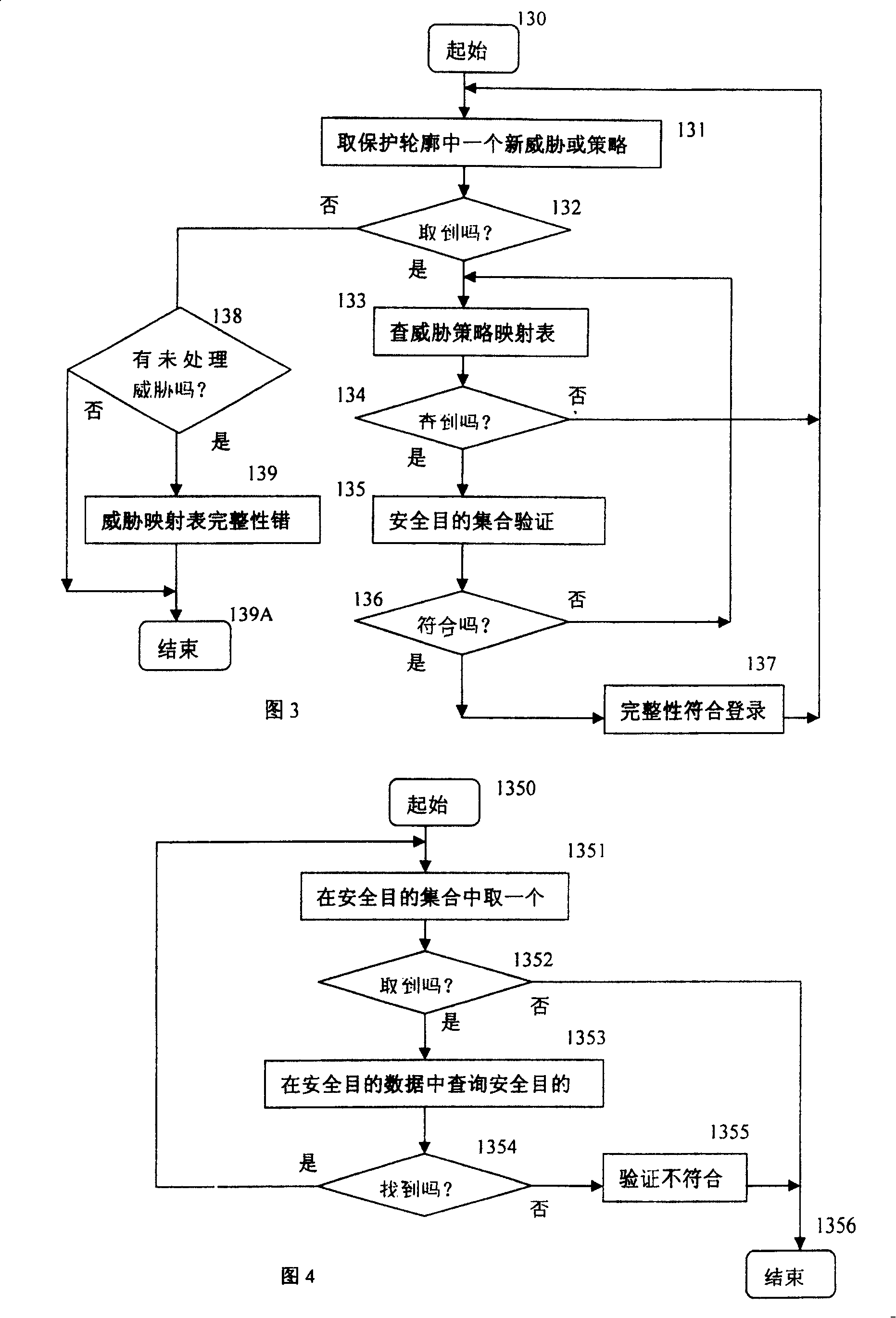
[0021] As shown in Figure 1, the safety detection and evaluation equipment inputs the protection profile to be evaluated through the keyboard, and uses the normalization module to convert the protection profile into structured organizational information that is easy to handle, including main data such as environmental analysis, safety purpose, and safety requirements. Then, the integrity check of the protection profile is performed by the verification check mechanism, and the threat policy mapping table (referred to as the threat mapping table) and the security purpose mapping table are queried and compared during the checking process.
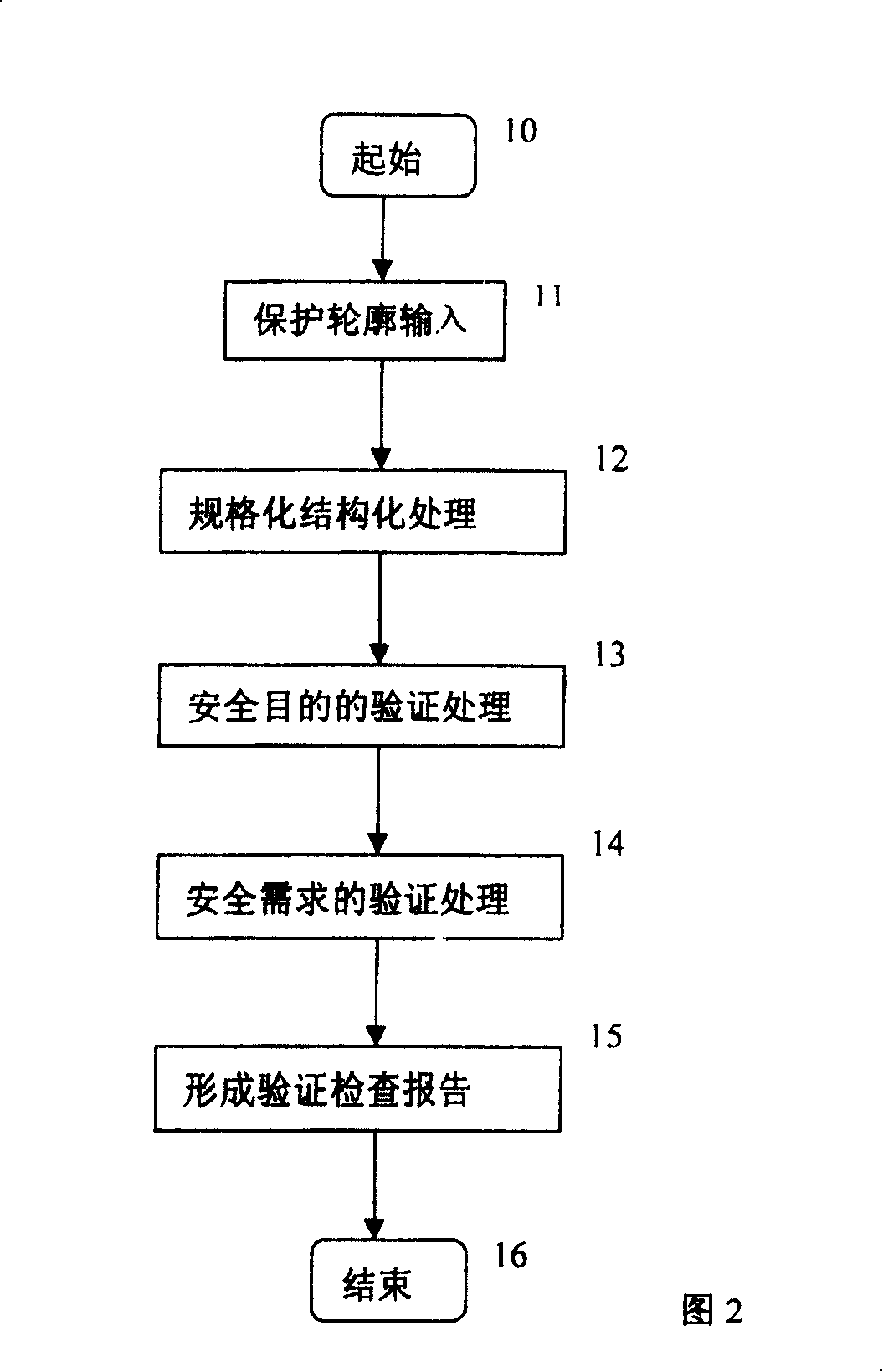
[0022]The method of the present invention is shown in FIG. 2 . Step 10 is the initial action. Step 11 is to input the protection profile to be evaluated. The protection profile includes protection profile identification, description, environment, security purpose, security requirements, and principles. Relevant to inspection and verification...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com