Intermediate system used for distinguishing and tracing user
An intermediate system and user technology, applied in the field of network security, can solve problems such as permanent identification is not suitable for user status record index
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings.
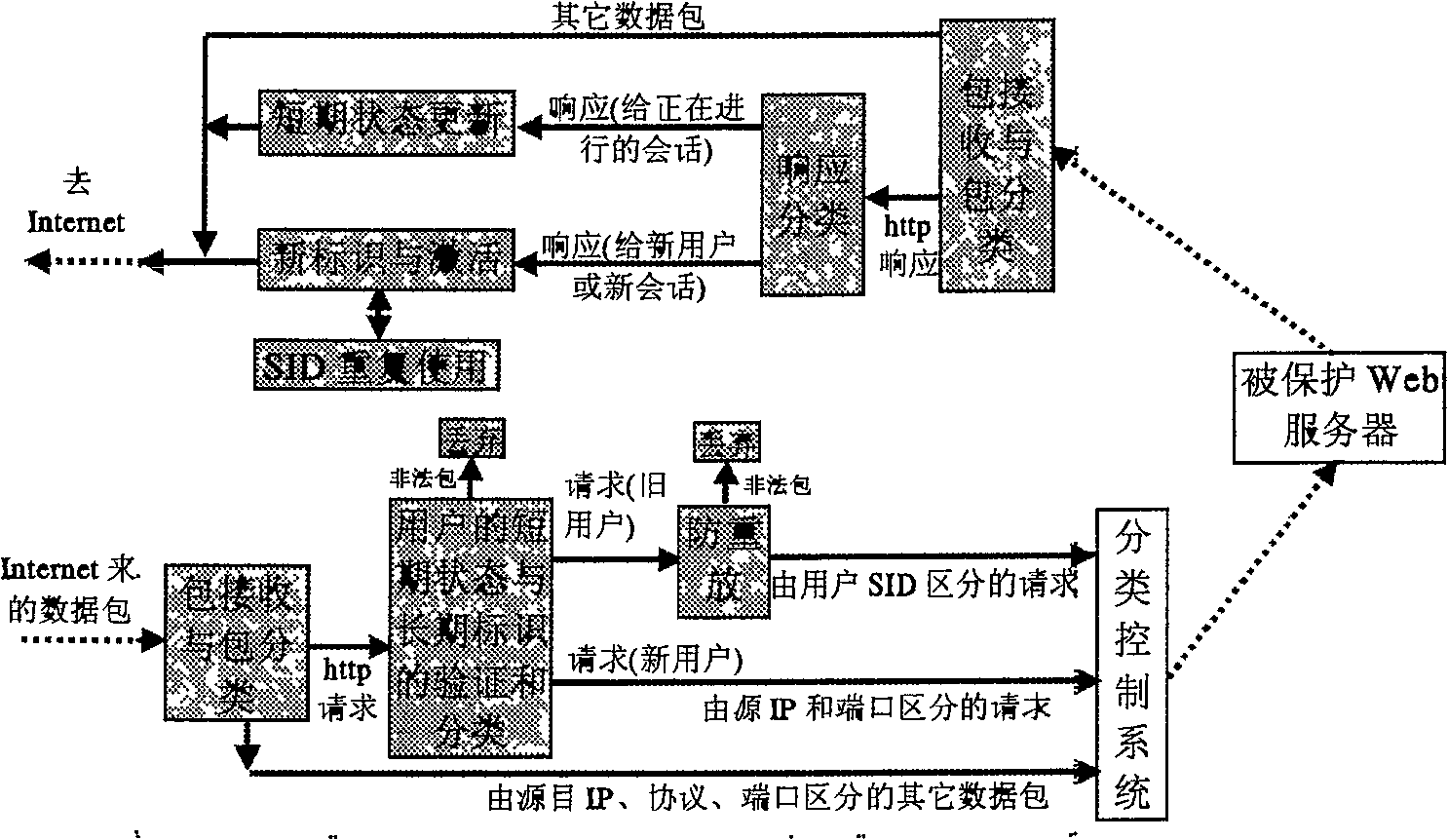
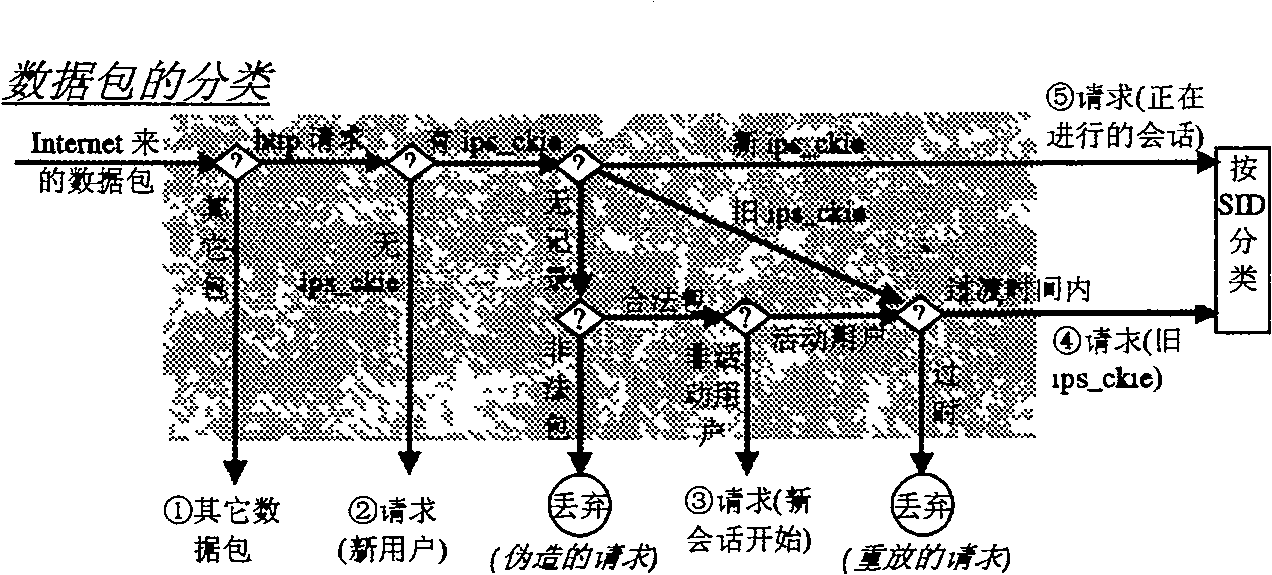
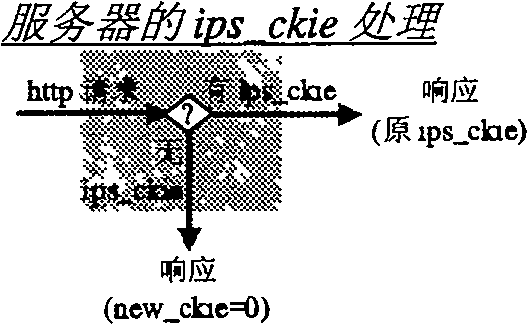
[0046] The structural diagram of the intermediate system for quickly and safely distinguishing and tracking users according to the present invention is shown in the attached figure 1 shown. The focus of this embodiment is to process the HTTP request packet, and for other data packets, mature technologies such as the access list control of the firewall and the abuse detection of the intrusion detection system can be used to realize the source and destination IP address, protocol, rate, etc. , process and key feature detection and filtering. After receiving and classifying data packets from the Internet, HTTP requests are separated. After the HTTP request is verified and classified by the user's short-term status and long-term identification, illegal or forged requests are filtered out, and new user requests and old user requests are passed. The old user's request pack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com