Data encryption storage method
A data encryption and data storage technology, which is applied in electronic digital data processing, digital data processing components, preventing unauthorized use of memory, etc., and can solve problems such as user loss, low ease of use, and easy loss of authentication hardware. , to achieve the effect of improving uniqueness, solving easy loss, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
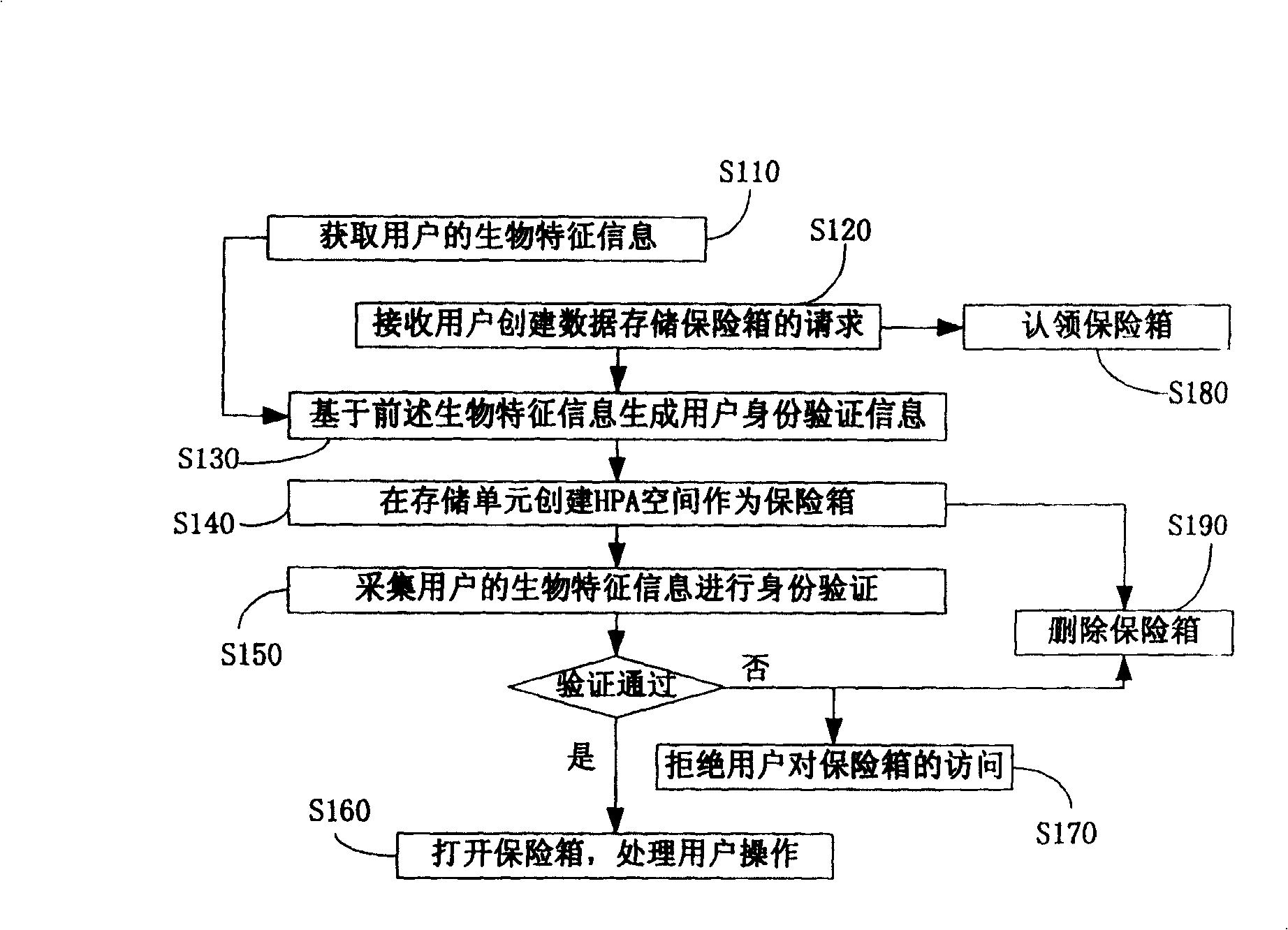
[0037] see figure 1 , is a flowchart of the data encryption storage method of the present invention.
[0038] Step S110, acquiring biometric information of the user.
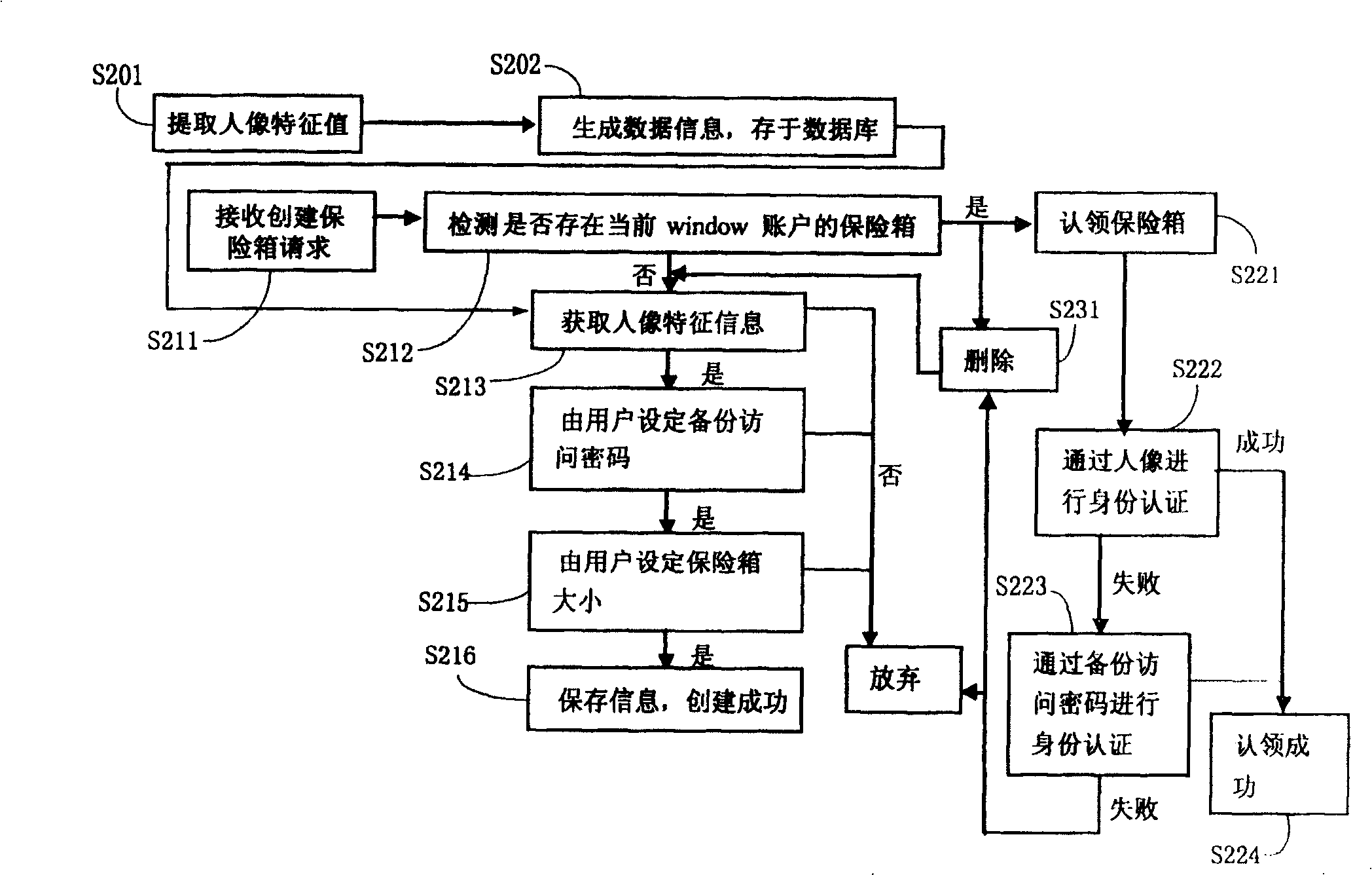
[0039] Step S120, receiving a request from a user to create a data storage safe.
[0040] Step S130, generating user identity verification information based on the aforementioned biometric information.
[0041] Step S140, creating an HPA in the storage unit as a space for creating a data safe.
[0042] Wherein, the HPA (Host Protected Area, hard disk host protected area) is created on the hard disk, and the HPA is an open standard.
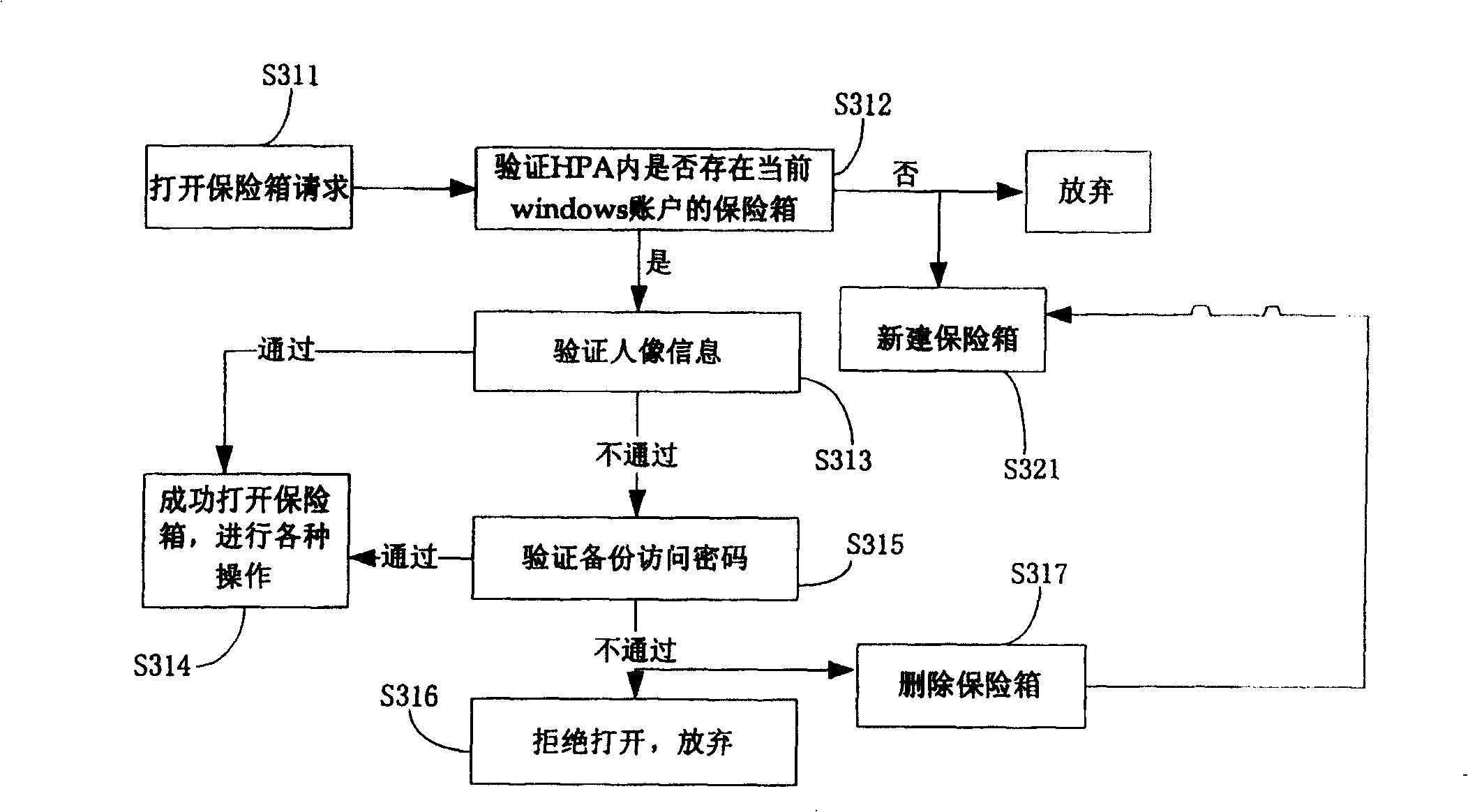
[0043] Step S150, receiving the user's request to access the safe, collecting the user's biometric information for identity verification; if the verification is passed, proceed to step S160; otherwise, proceed to step S170, denying the user's access to the safe.
[0044] Step S160, receiving the user's operation information on the safe and the data stored in the safe, and perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com