SDH signal encryption method realized by key bytes
A signal encryption and byte technology, applied in multiplex communication, digital transmission system, secure communication device, etc., can solve problems such as unrealizable, key byte encryption, unknown information, etc., and achieve the goal of reducing hardware processing speed Requirements, the effect of good encryption effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
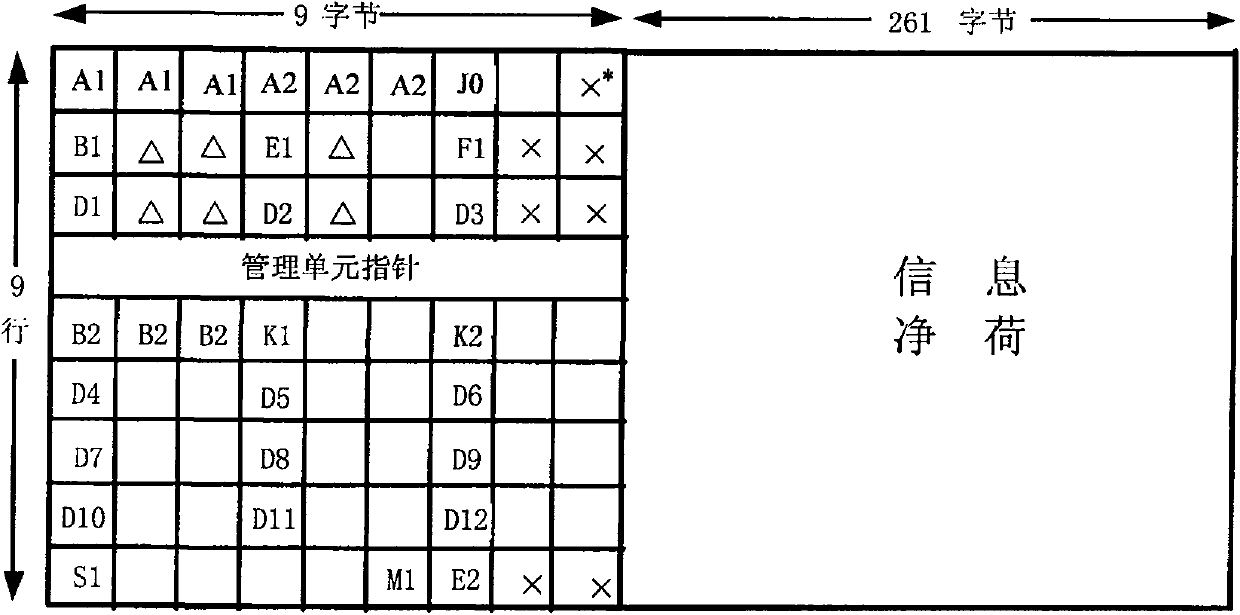
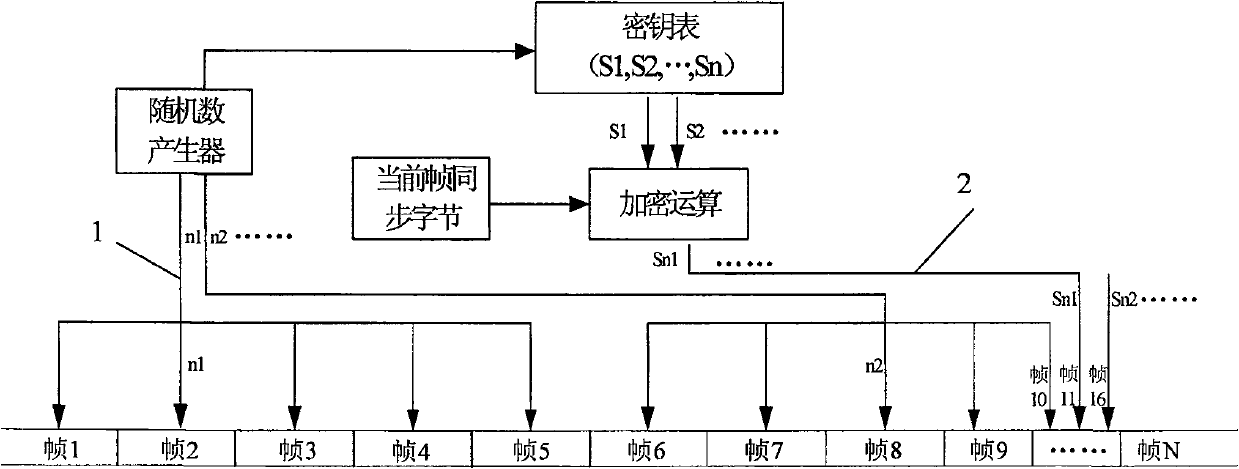
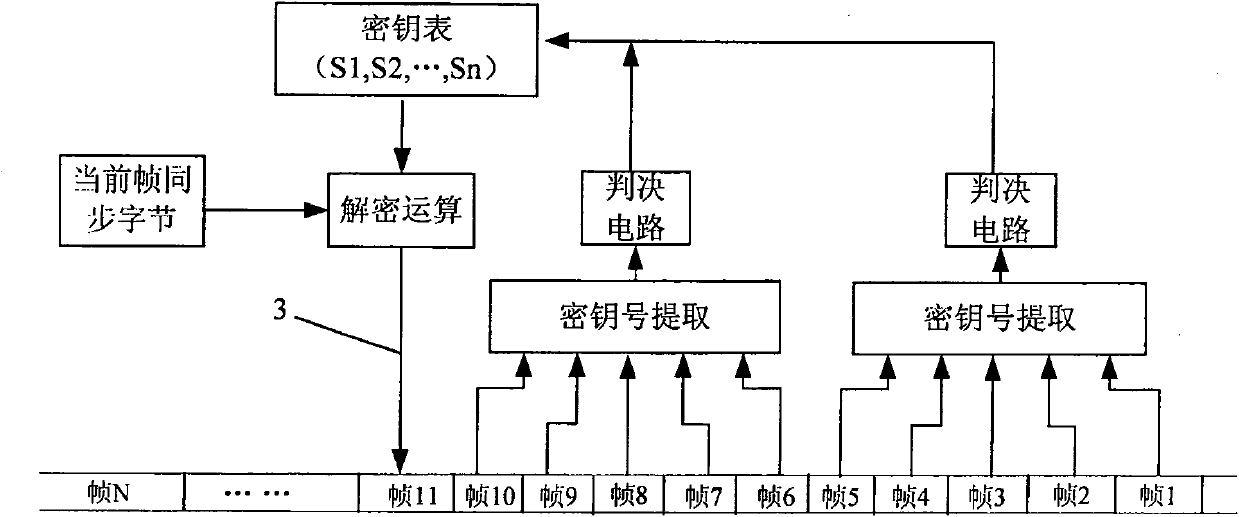
[0018] The method of encrypting SDH high-speed signal by using key bytes, the key overhead bytes provided in the SDH frame structure: frame synchronization bytes (A1, A2 bytes) and data communication channel bytes (D1-D12 bytes) encryption;
[0019] The frame sync bytes and the data communication channel bytes can also be encrypted separately, that is, only the frame sync bytes or only the data communication channel bytes are encrypted. The frame synchronization byte plays the role of frame positioning, and its protection can well realize the encryption of information; the data communication channel byte carries the network management information of the SDH transmission system, and its protection is related to the normal operation of the entire network, management and maintenance.
[0020] attached figure 1 It is the frame structure diagram of STM-1 in SDH. It consists of 9 rows x 270 columns (bytes) and is divided into three parts: segment overhead, pointer and information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com