Method and computing device for executing cryptographic processes for resisting cipher attack
A computing device, technology for masking data, applied in the field of computing systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
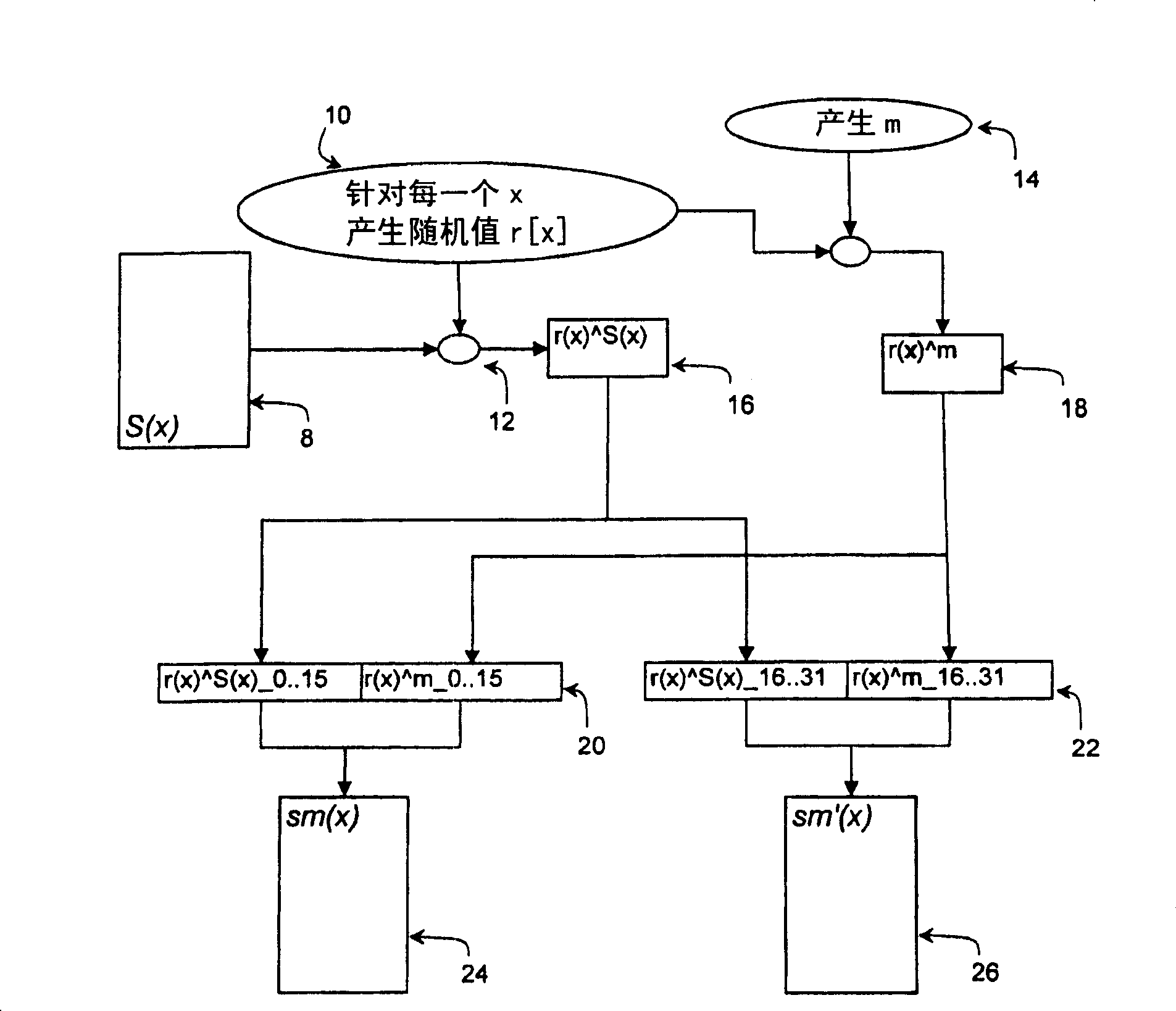
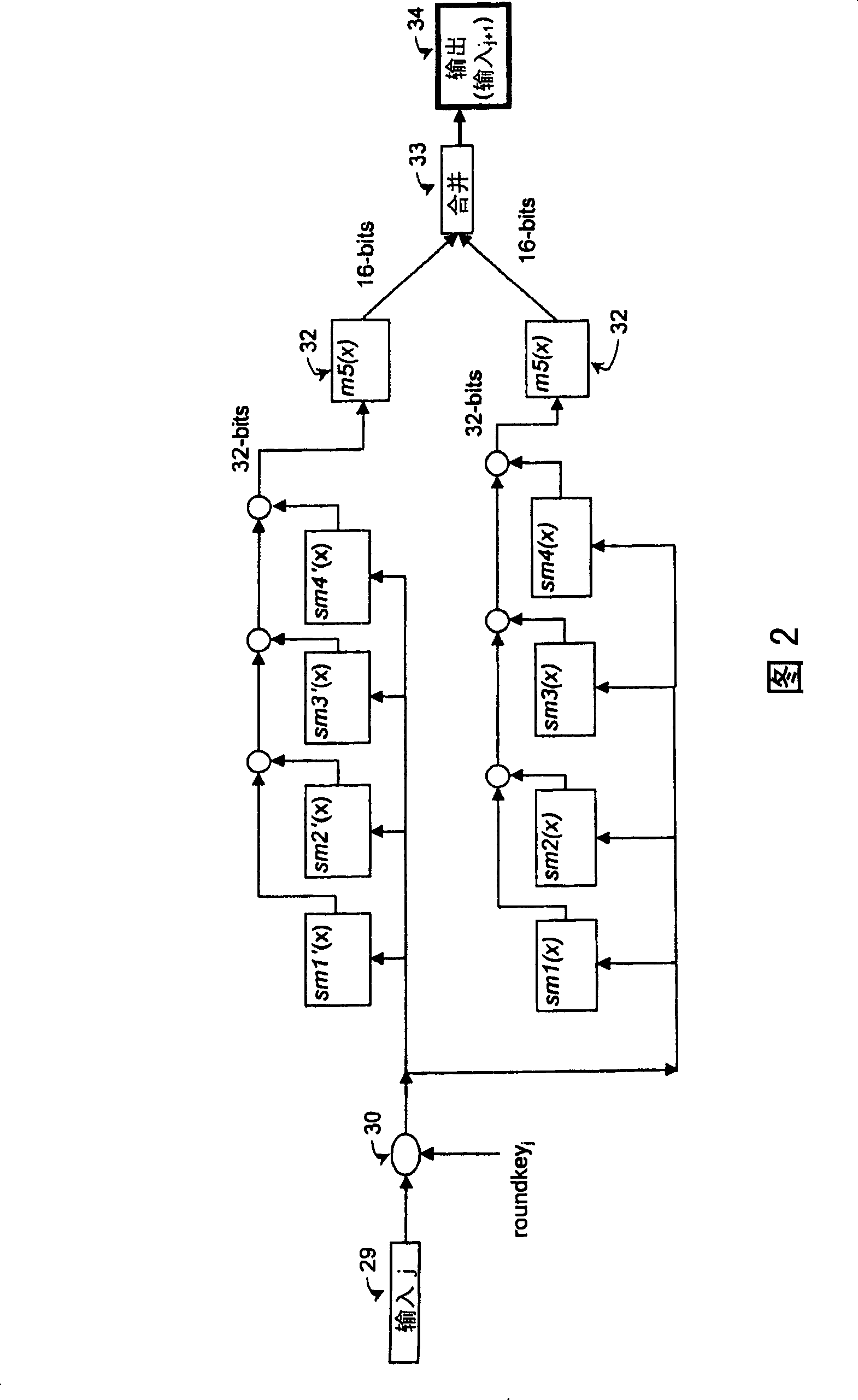
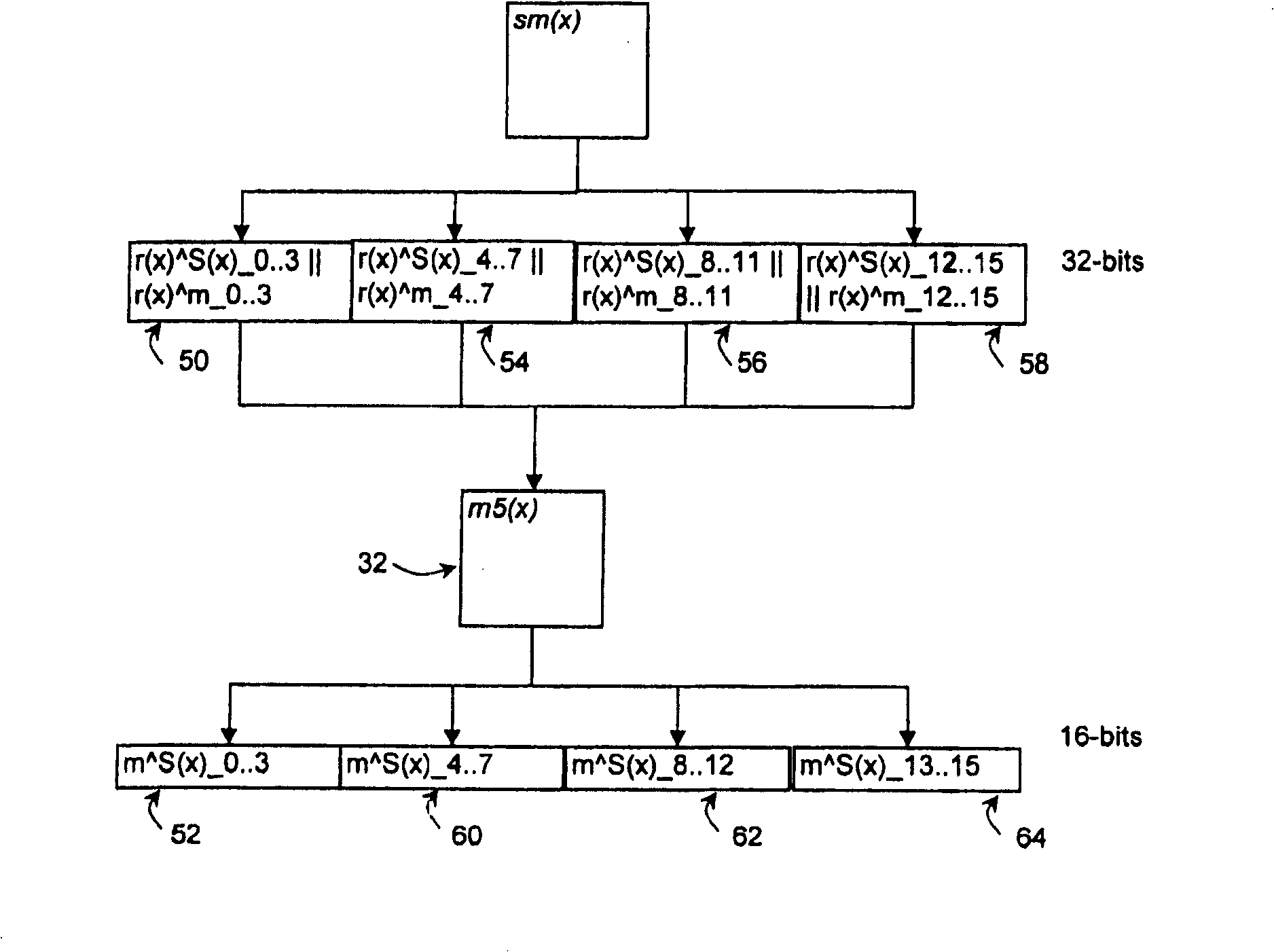
[0032] Advantages of the preferred embodiments include increased resistance to DPA attacks or other similar cryptographic attacks for devices implementing the preferred embodiments due to the parallelism of the encryption performed in accordance with the preferred embodiments. Additionally, using table splitting as described in the preferred embodiment makes higher level cryptographic attacks (eg, DPA attacks) more difficult due to the reduced number of available samples. For example, a single power sample reflecting data including random mask bits and mask table output bits may be available, but this single available sample may not be sufficient to enable higher order DPA attacks.
[0033] Advantages include the use of varying masks for the permutation table, which reduces energy, performance and program code overhead costs. This limited overhead allows such countermeasures to be used by devices such as wireless mobile devices that perform operations that require security but...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com