Software protection method
A technology of software protection and software, applied in the direction of program/content distribution protection, digital data processing components, instruments, etc., can solve the problems that the encryption lock cannot further improve the protection of software, and cannot guarantee the security of software codes, etc., to achieve improvement The effect of speed, ensuring safety, and increasing protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
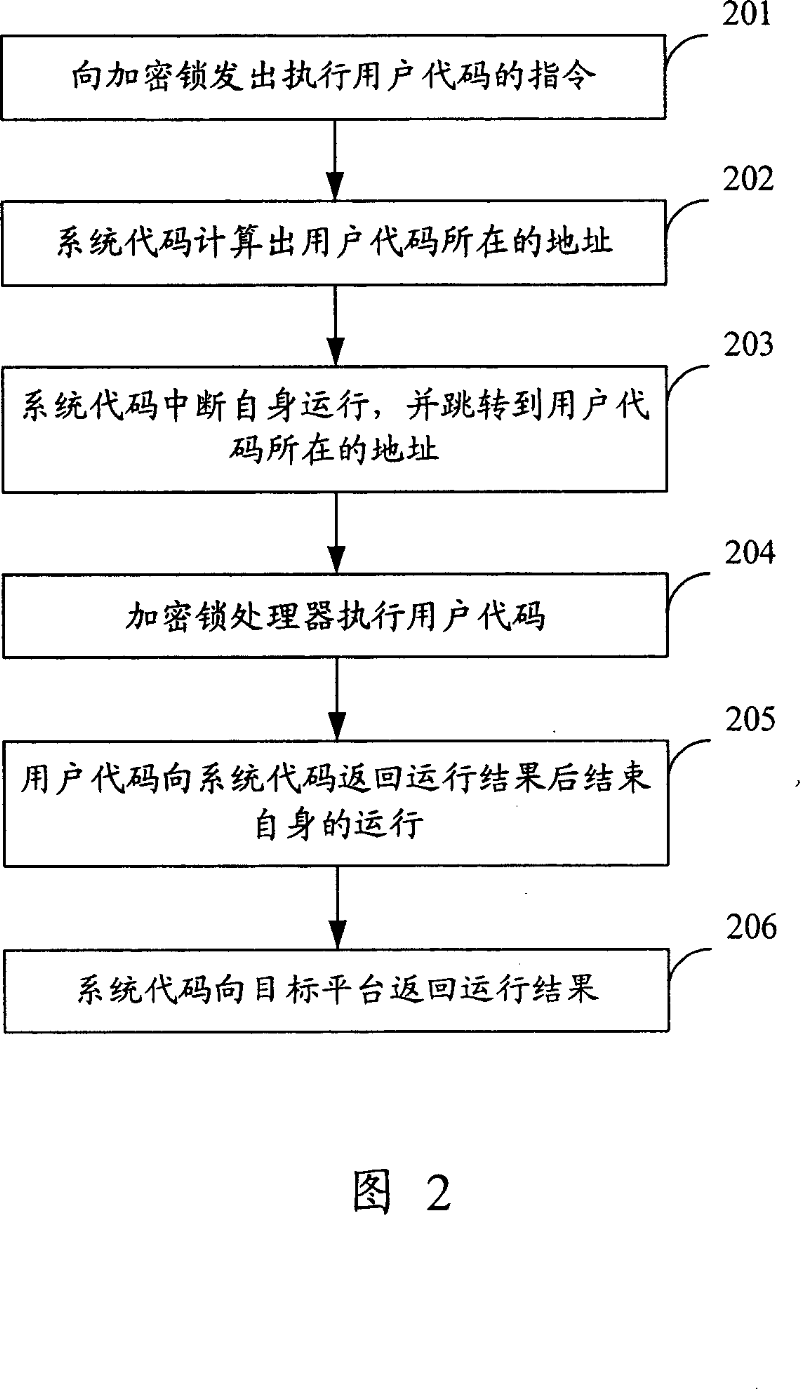
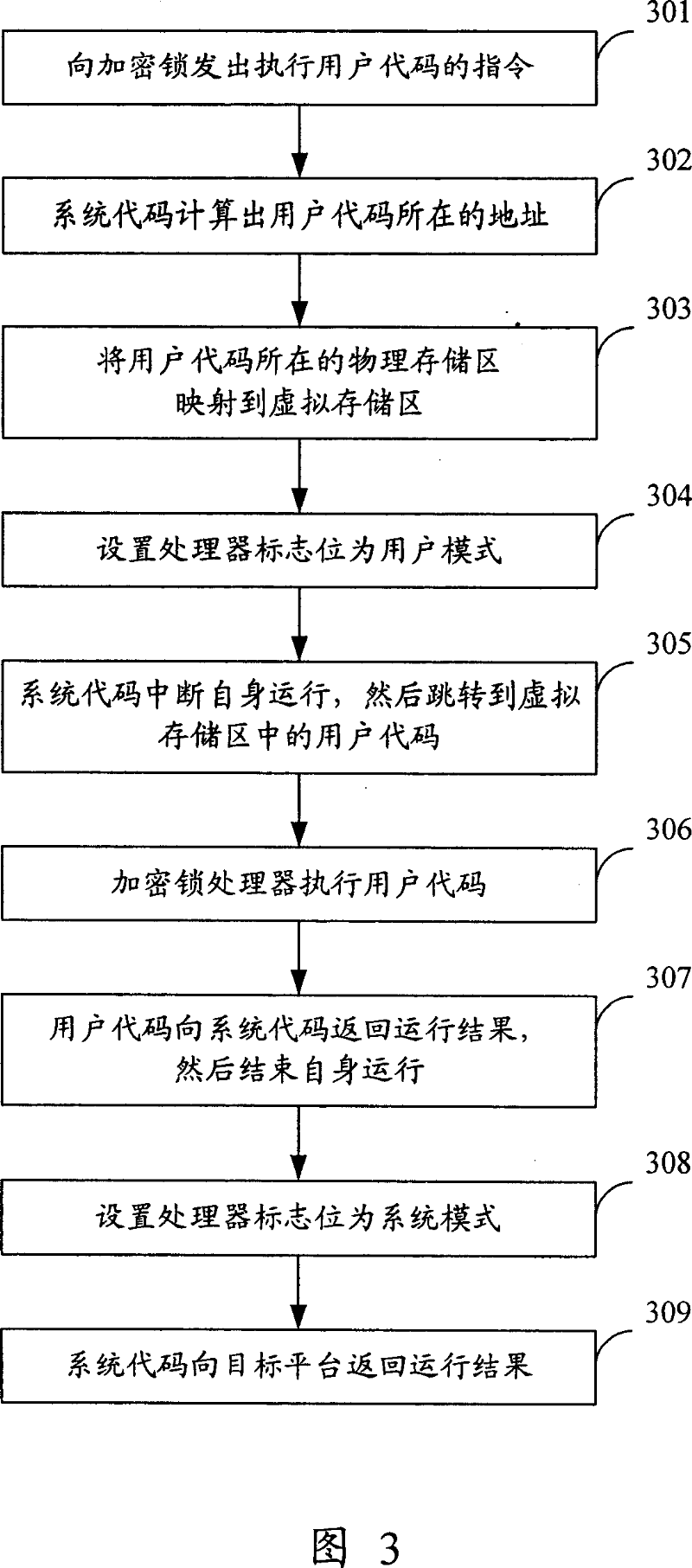
[0044] The core idea of the present invention is: the code running inside the dongle is divided into two parts, the system level and the user level, and the code responsible for the initialization of the dongle and the scheduling of internal resources of the dongle runs at the system level; To protect software code running at user level. Both system-level code and user-level code run directly on the dongle's processor.
[0045] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
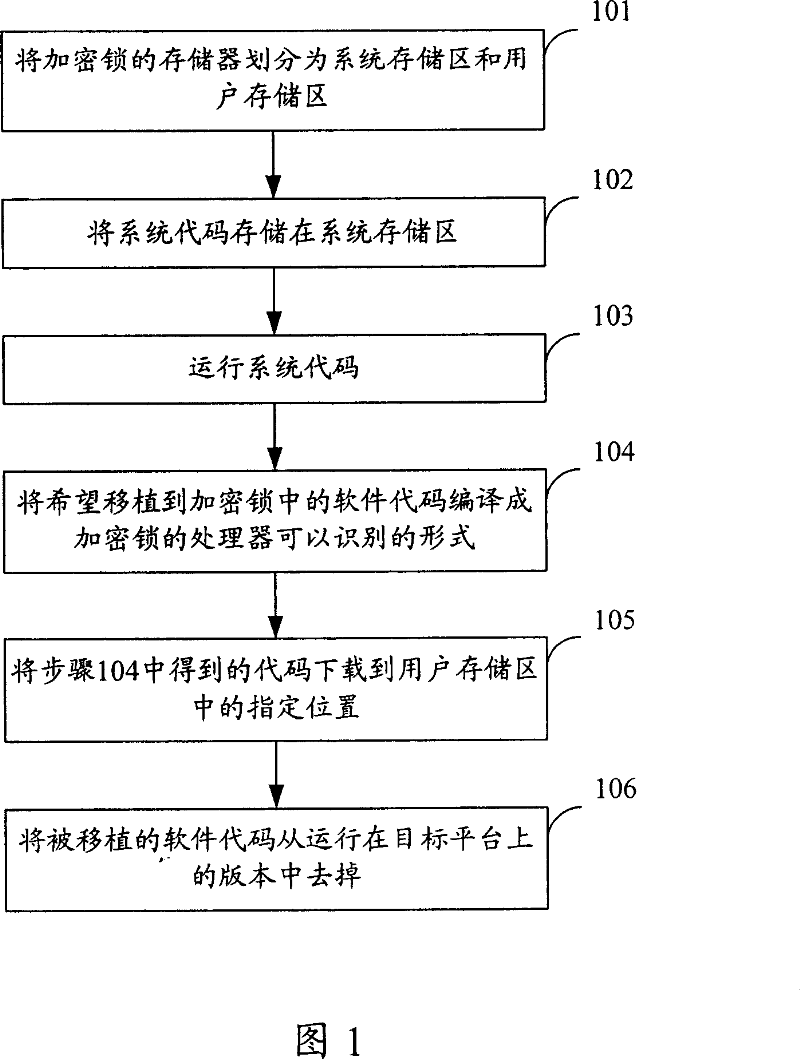
[0046] Please refer to Fig. 1, Fig. 1 is the flow chart of downloading code in the software protection method provided by the present invention, and this method comprises when downloading code:
[0047] Step 101: Divide the code storage of the dongle into a system storage area and a user storage area.
[0048] The sys...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap