Method and system for confirming terminal identity in mobile terminal communication
A mobile terminal and identity confirmation technology, applied in the field of mobile communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
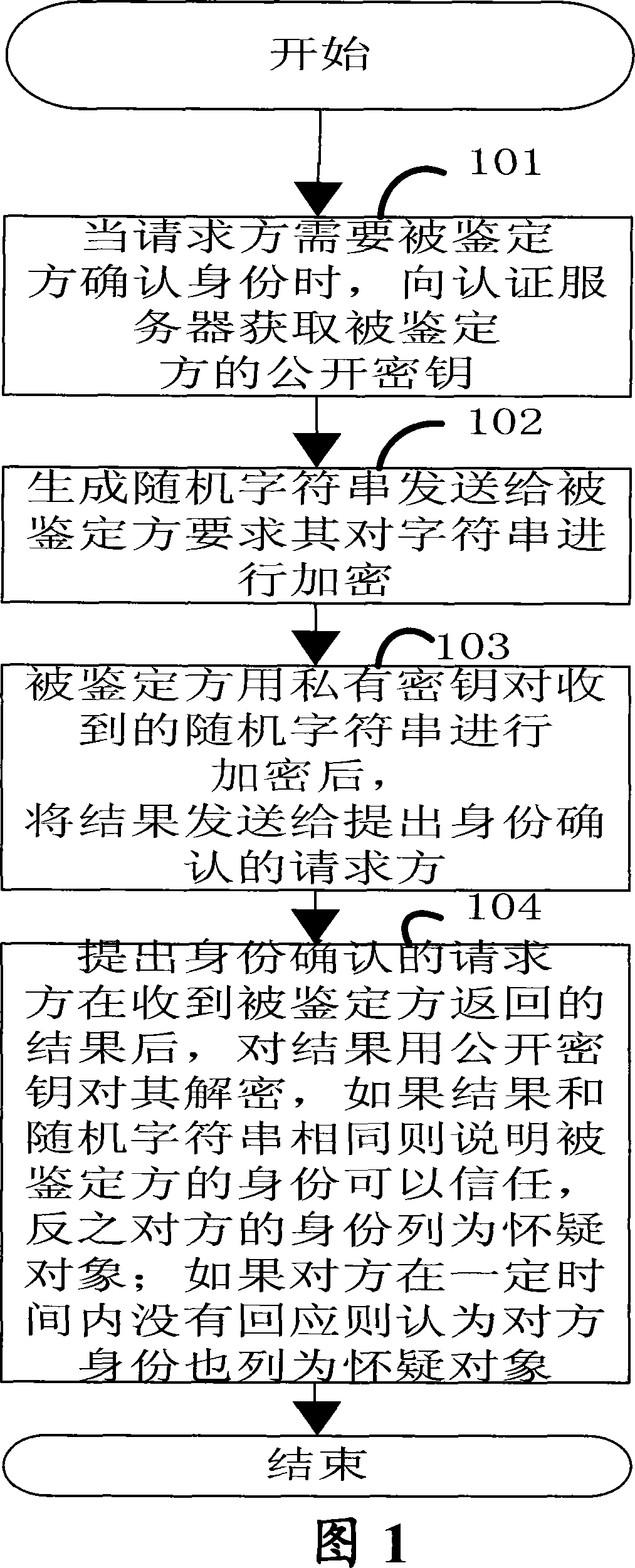
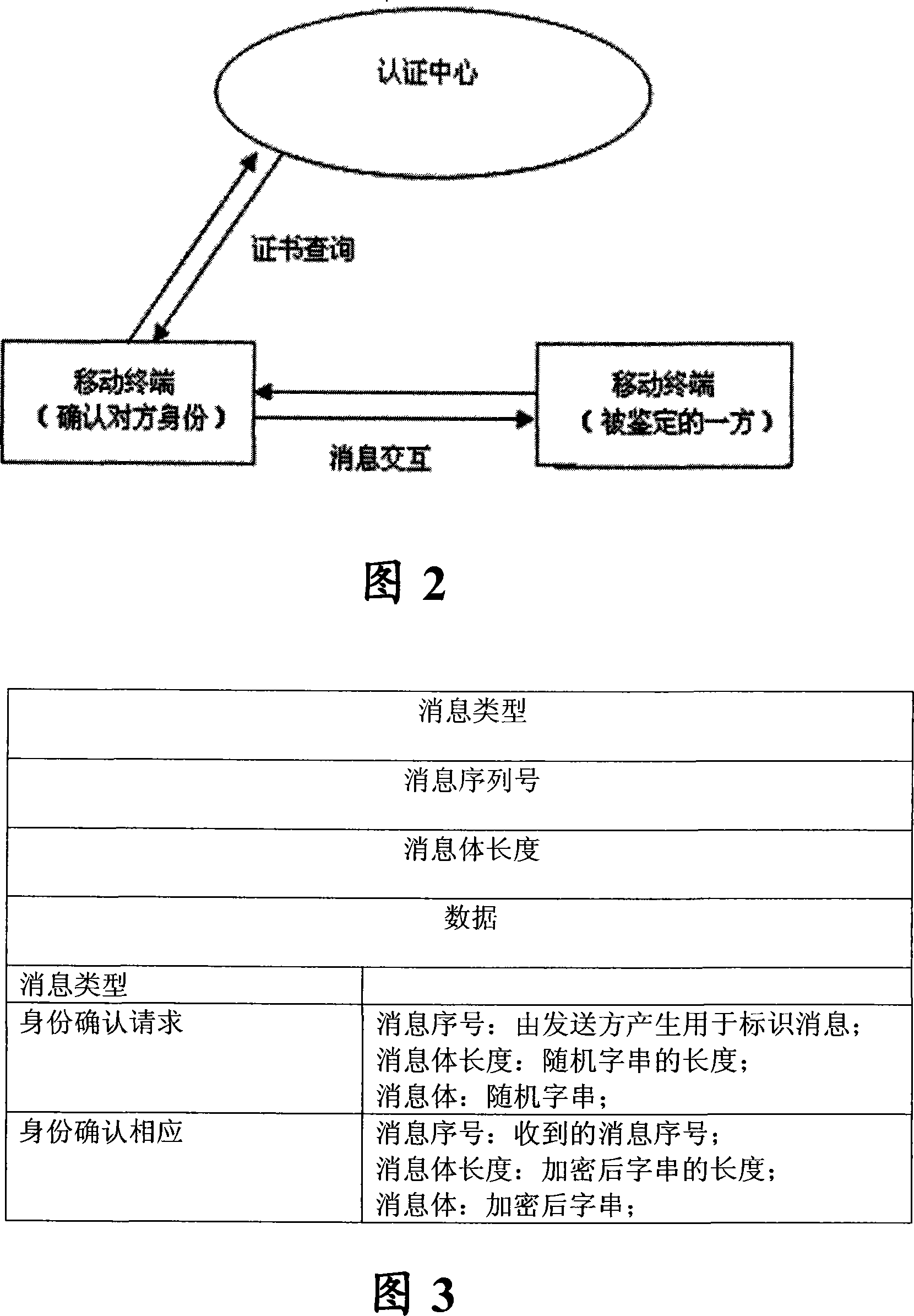
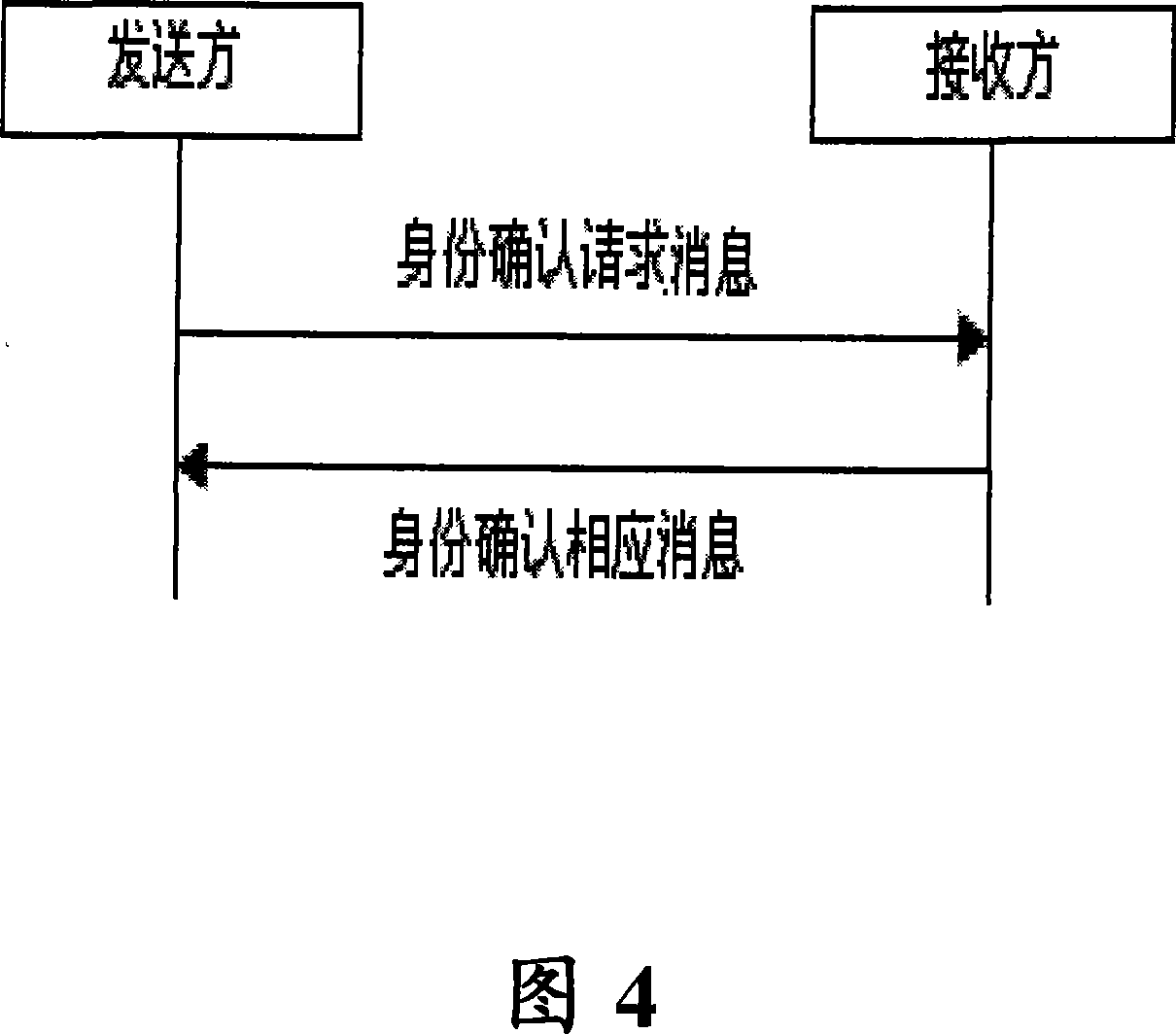
[0033] The purpose of the present invention is to introduce a method and system for confirming the identity of the opposite end in mobile terminal communication. The present invention is based on an asymmetric key algorithm to achieve the purpose of identity confirmation. Specific embodiments are described in detail below, but not as a limitation to the present invention.
[0034] In order to achieve the above purpose, and for the convenience of explanation, take a fixed station (a kind of CDMA wireless terminal) designed and developed based on Qualcomm platform as an example to illustrate how to realize the service of peer identity confirmation in a mobile terminal with peer identity confirmation .
[0035] Embodiments of the present invention adopt the following technical solutions:
[0036] The invention provides a method and system for a mobile terminal to ask the other party to confirm identity at any time during the whole process from the establishment of the communicat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com