Software protection
A technology for executing programs and execution environments, and is used in program/content distribution protection, instruments, electrical digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
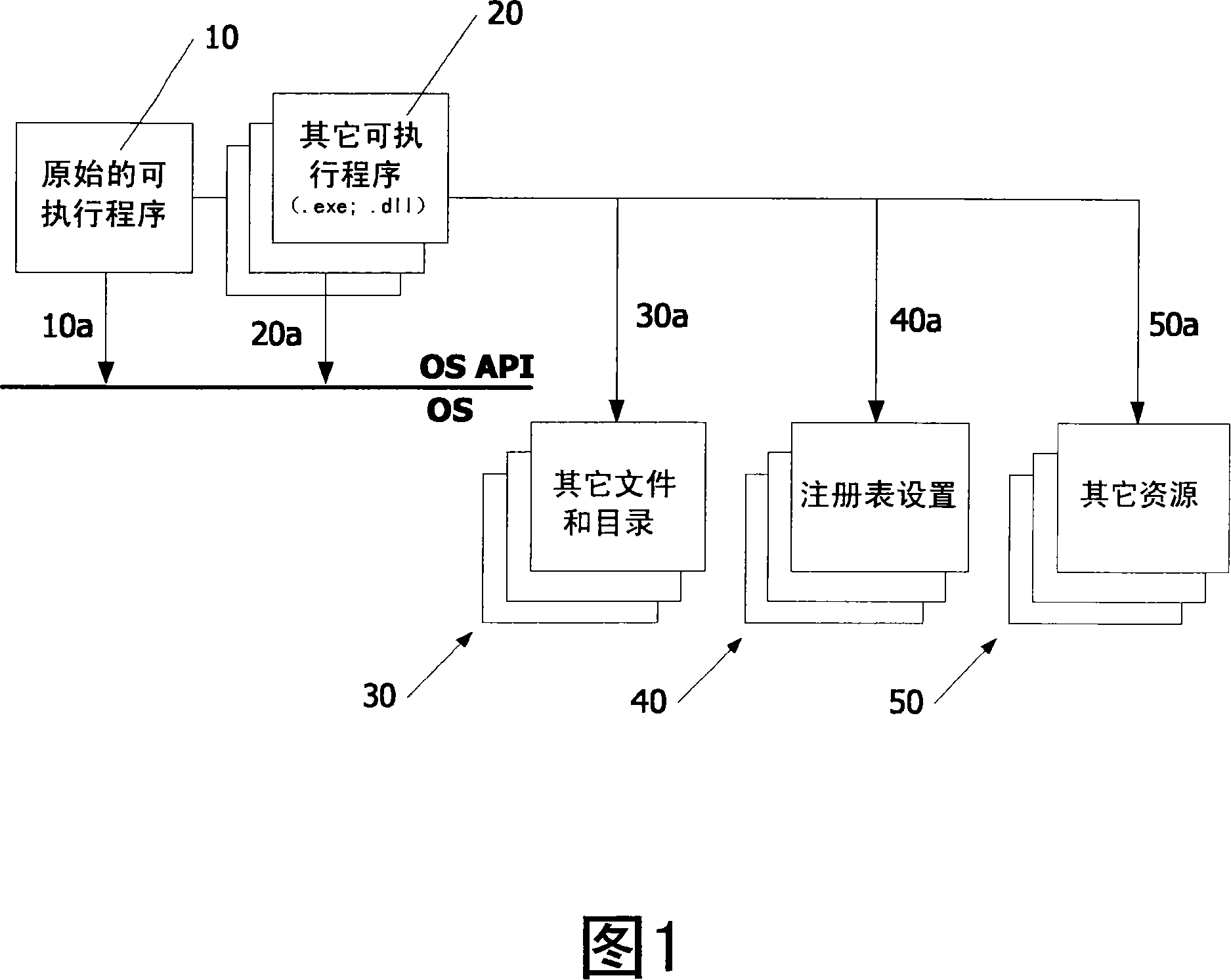
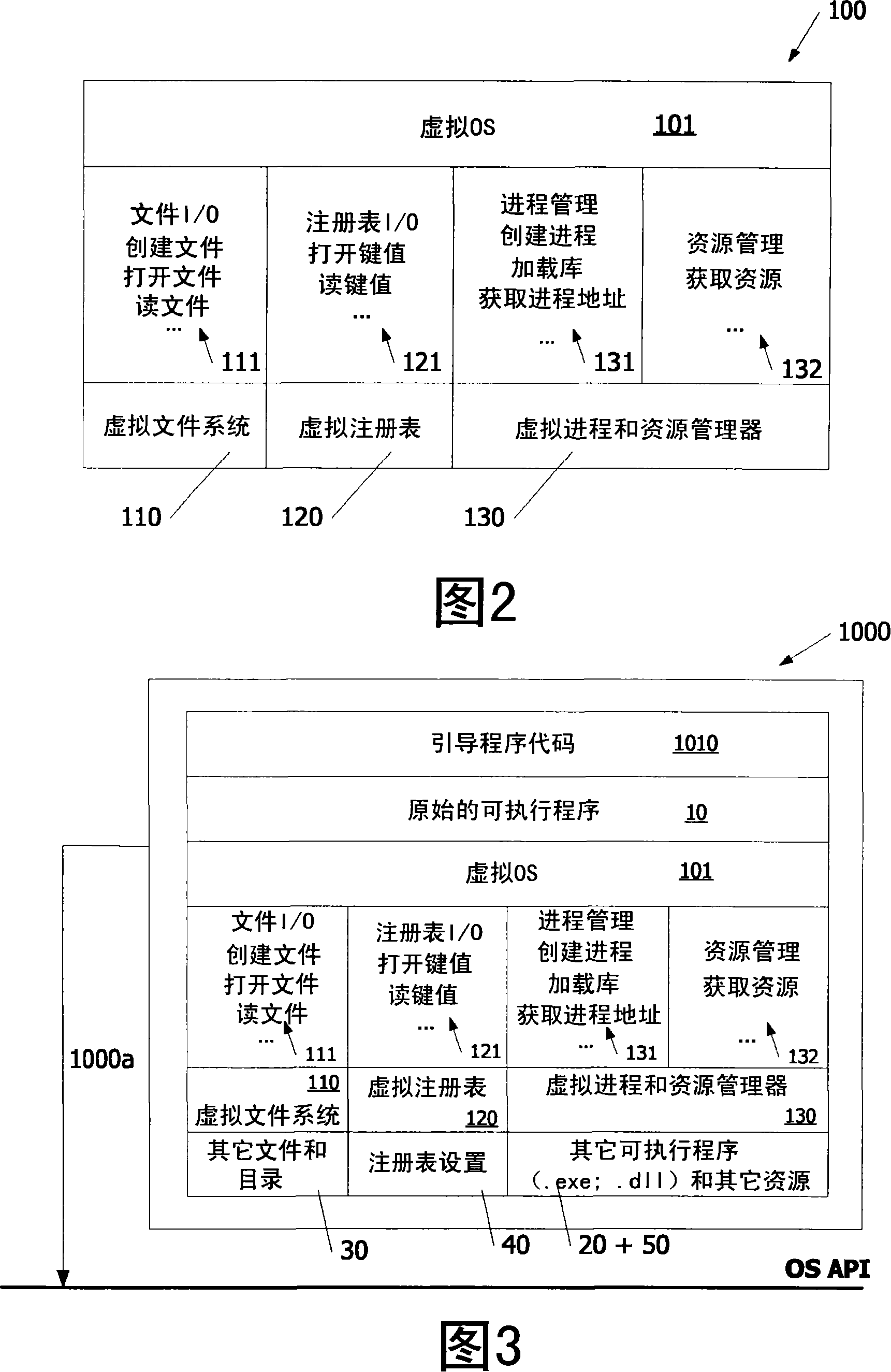
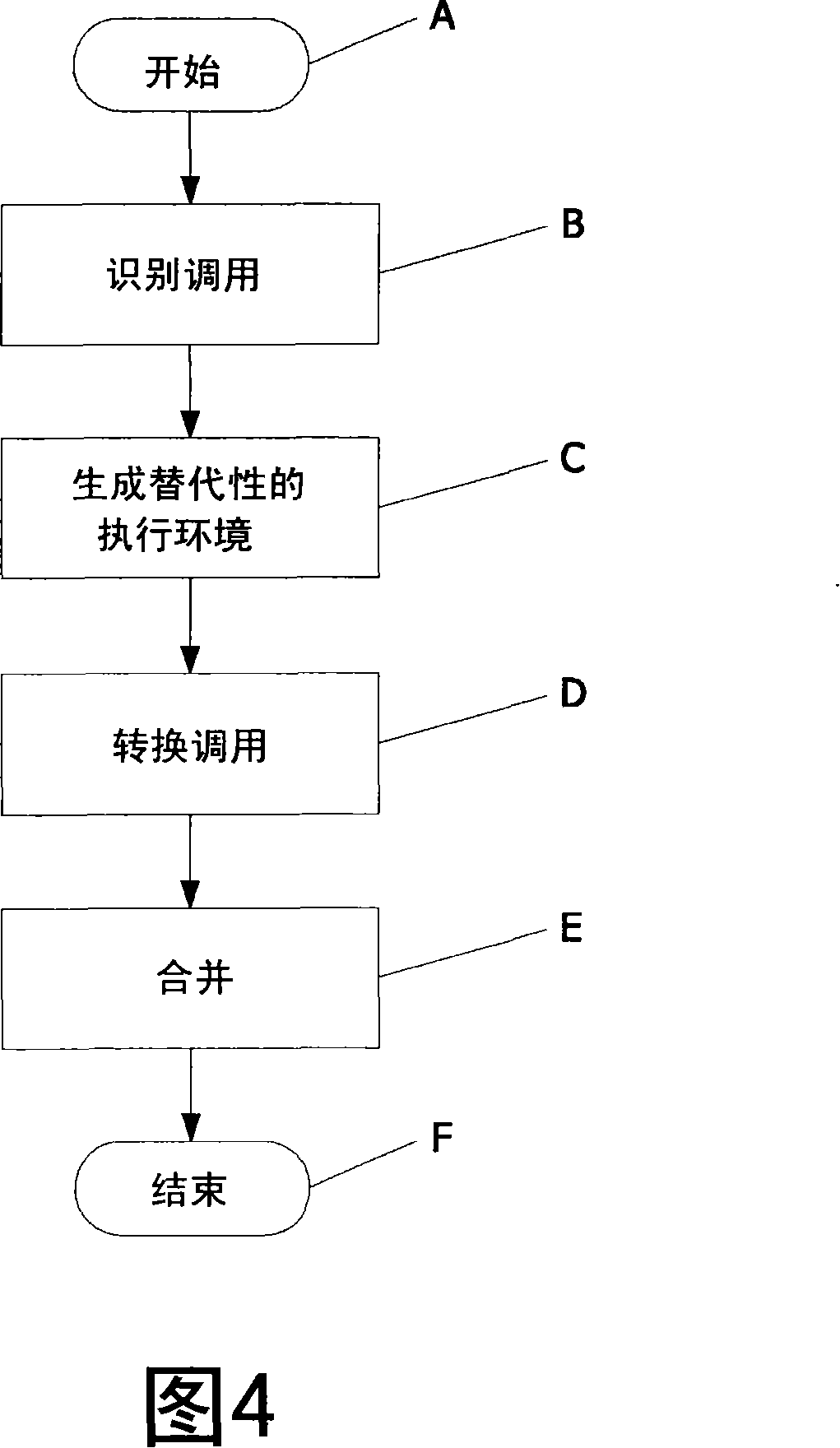
[0019] It should be understood that the components in all figures are parts of hardware, software or middleware, which may be implemented in a computer device. It should also be understood that a computer device includes an operating system (OS), eg, a program that manages all other programs in the computer device after initial loading into the computer device. Other programs are called executable programs or application programs. Executable programs or applications use the operating system in the following ways: by issuing service calls or requests through specified application program interfaces (OS APIs). The figure shows the OS API as a horizontal line and calls to the OS API as arrows pointing thereto. Direct calls to the operating system (OS) are shown in the figure as arrows pointing to elements located below the horizontal line.
[0020] It should also be understood that a computer device typically includes suitable components such as a registry, memory modules, proc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com