Method for secure data entry in an application
An application program and data technology, applied in the input/output process of data processing, digital transmission system, safety communication device, etc., can solve problems such as capture
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] In the following description, for purposes of explanation, numerous specific details are given in order to provide a thorough understanding of embodiments of the invention. It will be apparent, however, to one skilled in the art that the present invention may be practiced without these specific details.
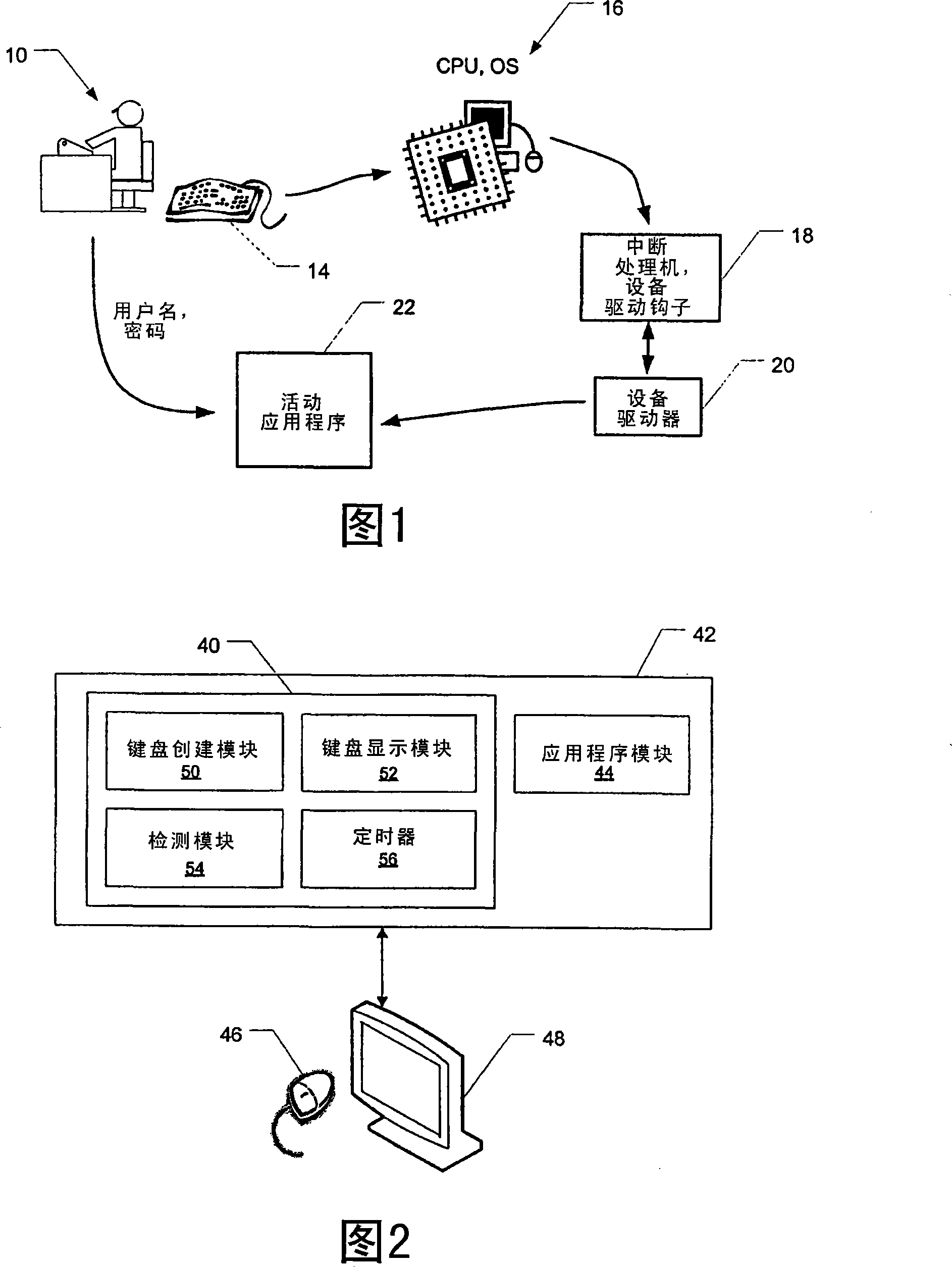
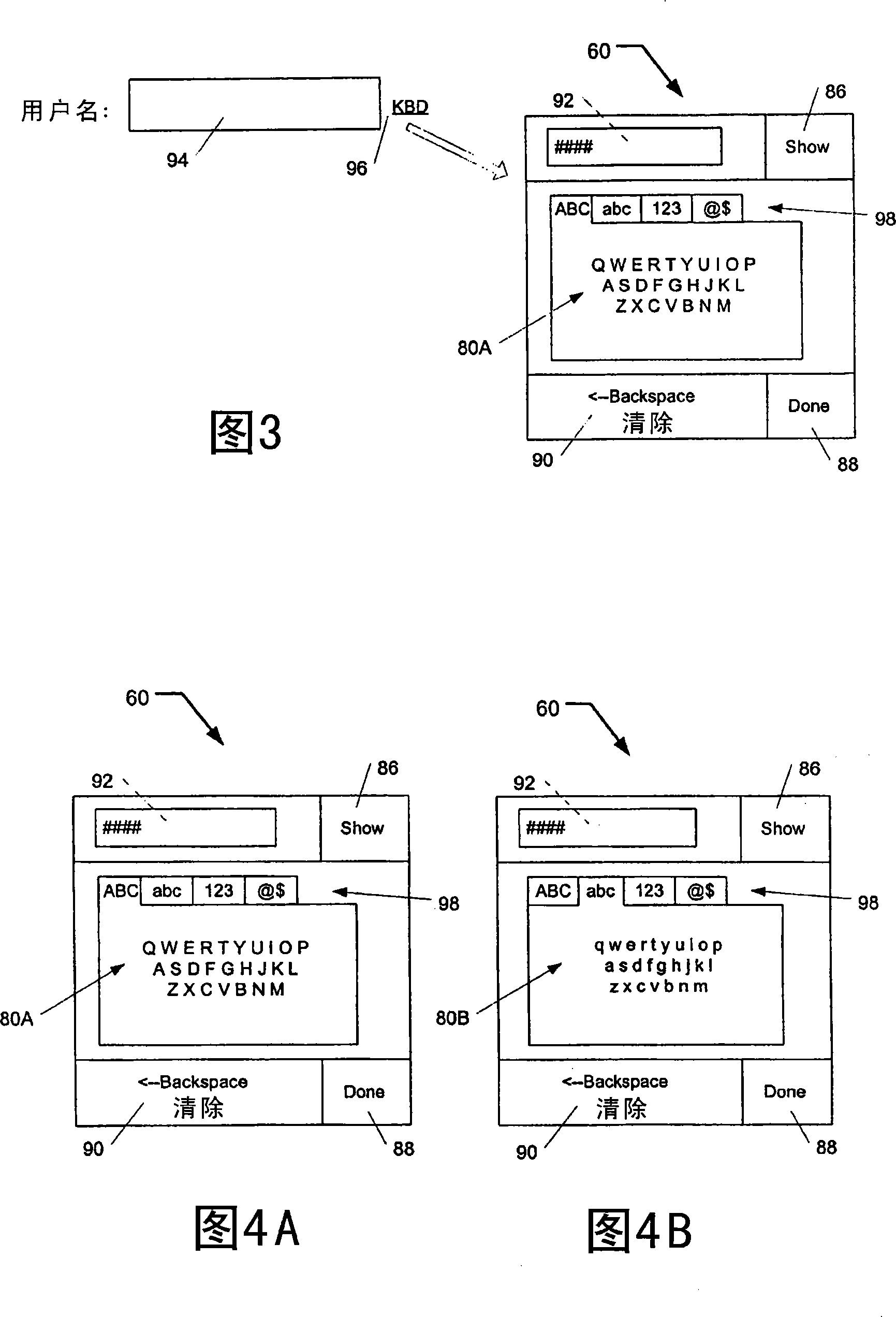
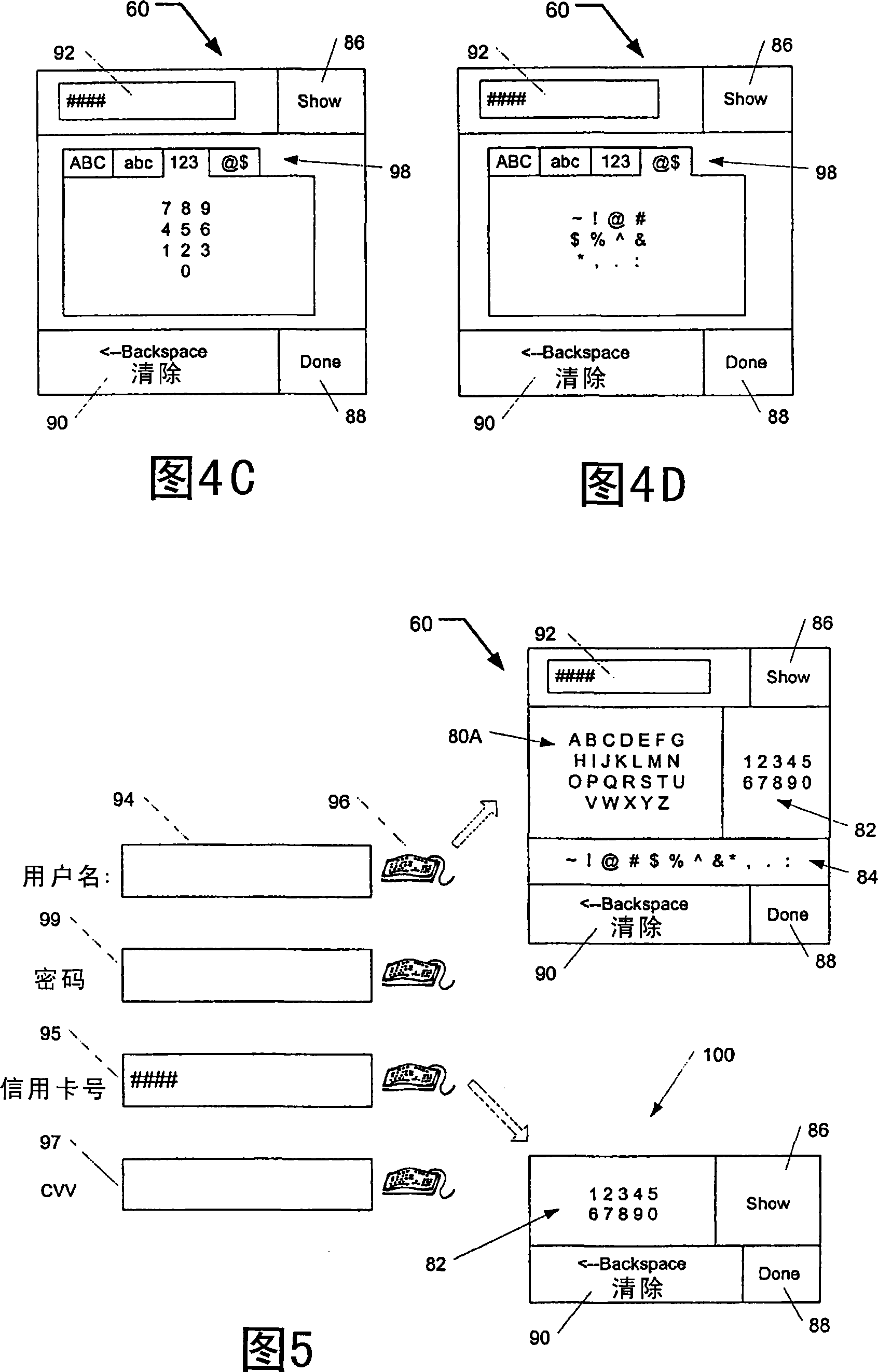
[0024] The transfer of confidential data from the user to the application is inherently insecure. Thus, in an example embodiment, user-entered confidential data bypasses traditional data flow through OS components which, in many instances, are the cause of insecurity. In an example embodiment, the motion of the pointing device is utilized, and thus OS components or similar components that may render data unsafe may be avoided. In this way, the use of a hardware keyboard is avoided, and thus no physical pressing of the keys is required. To avoid the use of a hardware keyboard, an example embodiment uses a GUI keyboard (soft keyboard) and pointer movement / position to e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com