A response request method and device
A technology for responding to requests and request messages, applied in the security field, can solve problems such as cost and multi-terminal system resources, and achieve the effect of improving system performance and ensuring normal calls
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
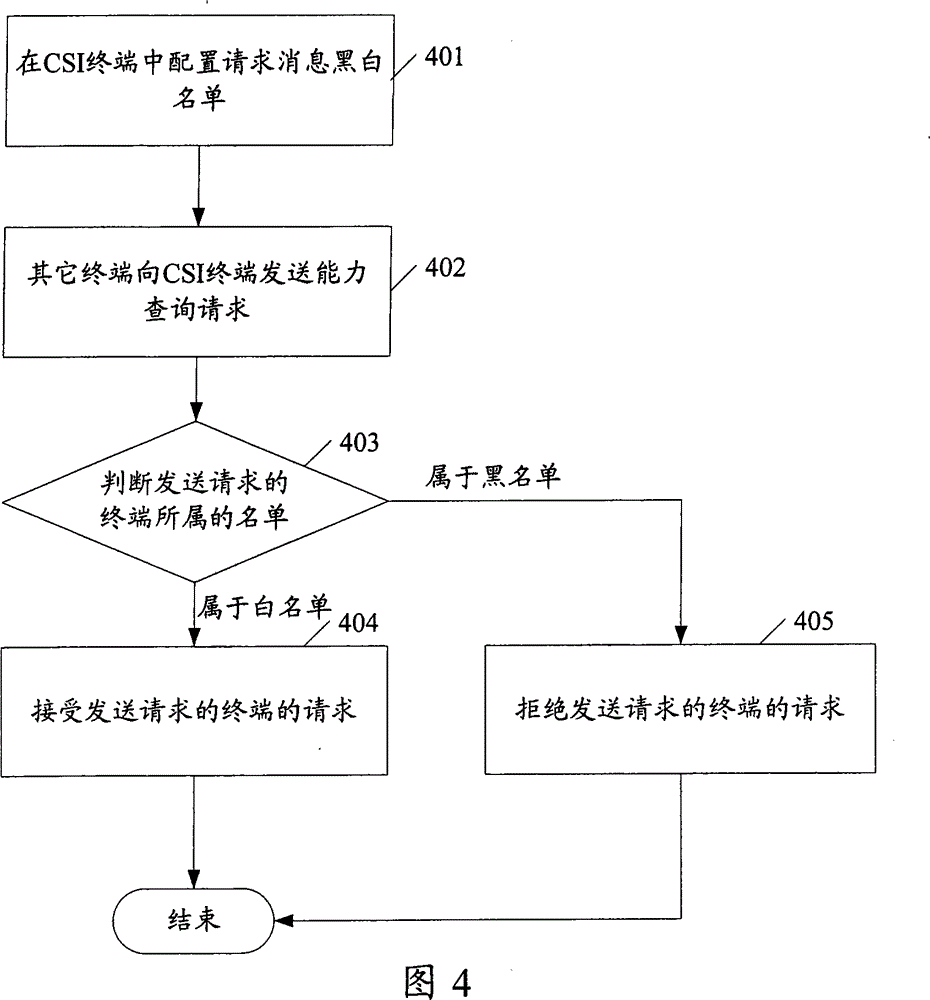
[0066] In this embodiment, a basic black and white list is used to determine whether requests from other terminals are allowed, and in the black and white list, the address of the terminal is used to represent a certain terminal.
[0067] Figure 5 That is, it is the main flowchart of the method for responding to the request in the CSI service in the first embodiment of the present invention. Such as Figure 5 As shown, the method includes:
[0068] Step 501: Configure a black and white list of request messages in a CSI terminal.
[0069] In this step, the configuration of the black and white list of request messages can be performed in a manner of active configuration by the user. In this embodiment, the address information of the terminal is used to represent a terminal, for example, the SIP address is used to represent the terminal, that is, the terminal list is actually the address list of the terminal.
[0070] After configuring the black and white list of request messages for t...
Embodiment 2
[0084] In order to increase the flexibility of the system, the terminal can set security options when configuring the list of terminals that are allowed to be inquired. For the capability request information from some terminals, authentication operations are required. In this embodiment, on the basis of the first embodiment, the method for querying terminal capabilities that is added to the authentication operation is described in detail, and the specific authentication operation is password authentication.
[0085] Figure 5 It is the main flow chart of the method for responding to the request in the CSI service in the second embodiment of the present invention. Such as Figure 5 As shown, the method includes:
[0086] Step 501: Configure a black and white list of request messages in a CSI terminal.
[0087] In this step, since the CSI call is established on the basis of the IMS call, the method of configuring the capability black and white list may be: synchronization with the IMS...
Embodiment 3
[0108] According to user needs and save unnecessary system consumption, the description types of terminal capabilities that do not need to be fed back can be specified in the black and white list. When the terminal determines that the terminal capability description can be fed back, it is only necessary to feed back the description of the terminal capability that needs to be fed back. User needs and save system consumption. In this embodiment, on the basis of the first embodiment, this embodiment is described in detail.
[0109] Picture 9 This is the main flowchart of the method for querying the capabilities of the CSI terminal in the third embodiment of the present invention. Such as Picture 9 As shown, the method includes:
[0110] Step 901: Configure a black and white list of request messages in a CSI terminal.
[0111] In this step, the way to configure the black and white list of request messages may be: the terminal automatically detects the OPTIONS attack, and after it is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com