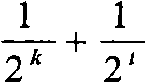IP network two-stage fault-tolerance intrusion-tolerance routing mechanism based on faith
An IP network and routing technology, applied in the field of communication, which can solve problems such as reliability
Inactive Publication Date: 2008-10-29
UNIV OF ELECTRONICS SCI & TECH OF CHINA
View PDF0 Cites 13 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
For example, the former has the advantage that each selection of the next hop is approved by the source node; the disadvantage is that the trust value evaluated by the source node for non-adjacent nodes is not as reliable as the trust value evaluated for adjacent nodes
For the latter, its advantages and disadvantages are exactly the opposite of those of the multiplicative method
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
specific Embodiment approach
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a two-stage fault tolerant and intrusion tolerant routing mechanism for an IP network based on trust. The mechanism is divided into two stages: the first stage is routing discovery, namely, a plurality of credible paths are discovered; the second stage is optimal path selection, namely, the optimal path for routing is selected from the discovered paths. In the first stage, the mechanism utilizes a trust relationship appraisal method of blending multiplication and addition and effectively improves the fault tolerant and intrusion tolerant performance of an IP network router. In the second stage, users always use the optimal router for communication by a path grading strategy, thus effectively avoiding various attacks to the paths. In addition, the invention also describes a definition, measurement, updating and an obtaining method of a trust value with fault tolerant and intrusion tolerant performance in detail.
Description
Trust-based two-stage fault-tolerant and intrusion-tolerant routing mechanism for IP networks technical field The invention relates to the technical field of communication, in particular to a trust-based two-stage fault-tolerant and intrusion-tolerant routing mechanism of an IP network. Background technique Network routing security is the top priority of network security. However, current IP network routers can only simply discover and receive routing information and cannot effectively identify routing-related malicious attacks, or can only prevent limited types of routing threats and anomalies. For example, OSPFv2 uses passwords and encrypted MD5 to improve routing security; Internet Protocol Security (IPSec) is used to ensure the confidentiality and integrity of communication; Secure-BGP is used to ensure the correctness of BGP confirmation; there are other technologies such as encryption, etc. . However, these technologies are limited in improving security performance...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L12/56H04L12/26H04L1/16H04L29/06H04L45/28
Inventor 纪俊杰阳小龙隆克平王进吴雄飚林建人
Owner UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com