A Defense Method for Selective Forwarding Attacks in Sensor Networks
A sensor network and selective technology, applied in the direction of data exchange network, transmission system, digital transmission system, etc., can solve the problems of limited ability to resist attacks, damage data transmission, etc., to reduce reception delay, improve security performance, and prevent tampering The effect of packets
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
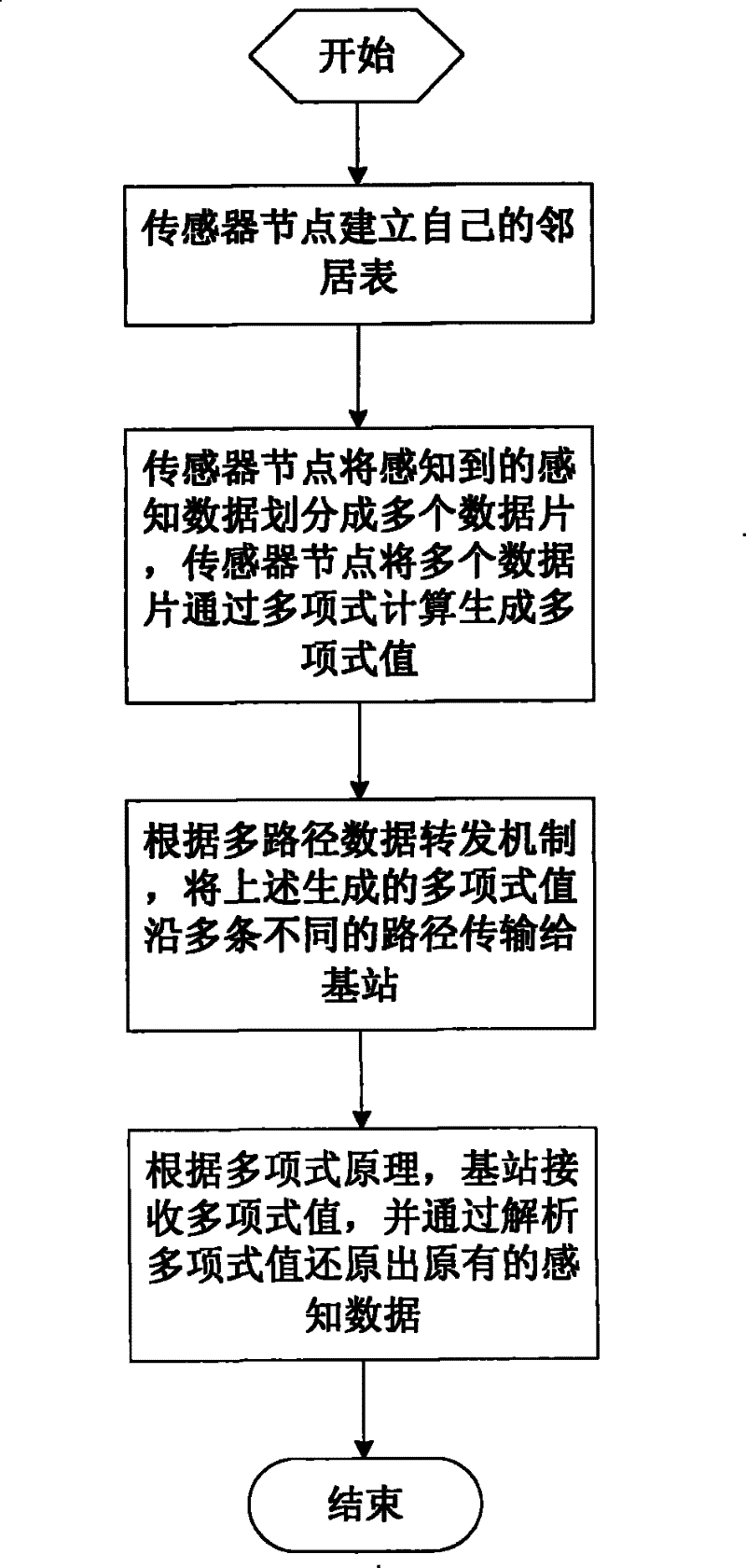
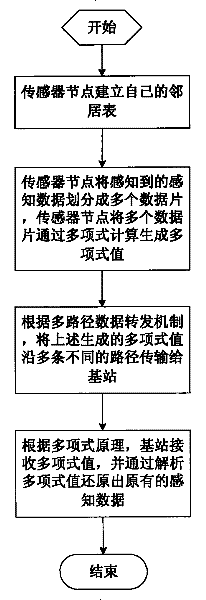
[0022] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0023] A defense method for selective forwarding attacks in a sensor network, the sensor network includes a plurality of identical sensor nodes randomly deployed in a monitoring area with high density, and once deployed, the sensor nodes will not move any more; Communication radius, the use of the same sensor nodes is beneficial for the expansion of large-scale sensor networks and facilitates the management of sensor networks. The same sensor nodes form a wireless ad hoc network in a self-organizing manner. The wireless ad hoc network is connected to a safe and trusted base station. All sensor nodes transmit the perceived data to the base station. Each sensor node has a unique and The key shared by the base station, so that when attacked by a malicious node, the sensor network will only disclose the key of the attacked sensor node without affe...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap