Negotiation method for safety algorithm
A security algorithm and network-side technology, applied in the field of security algorithm negotiation, can solve problems such as inability to support operator security algorithms, lack of scalability, and inability to satisfy operators
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
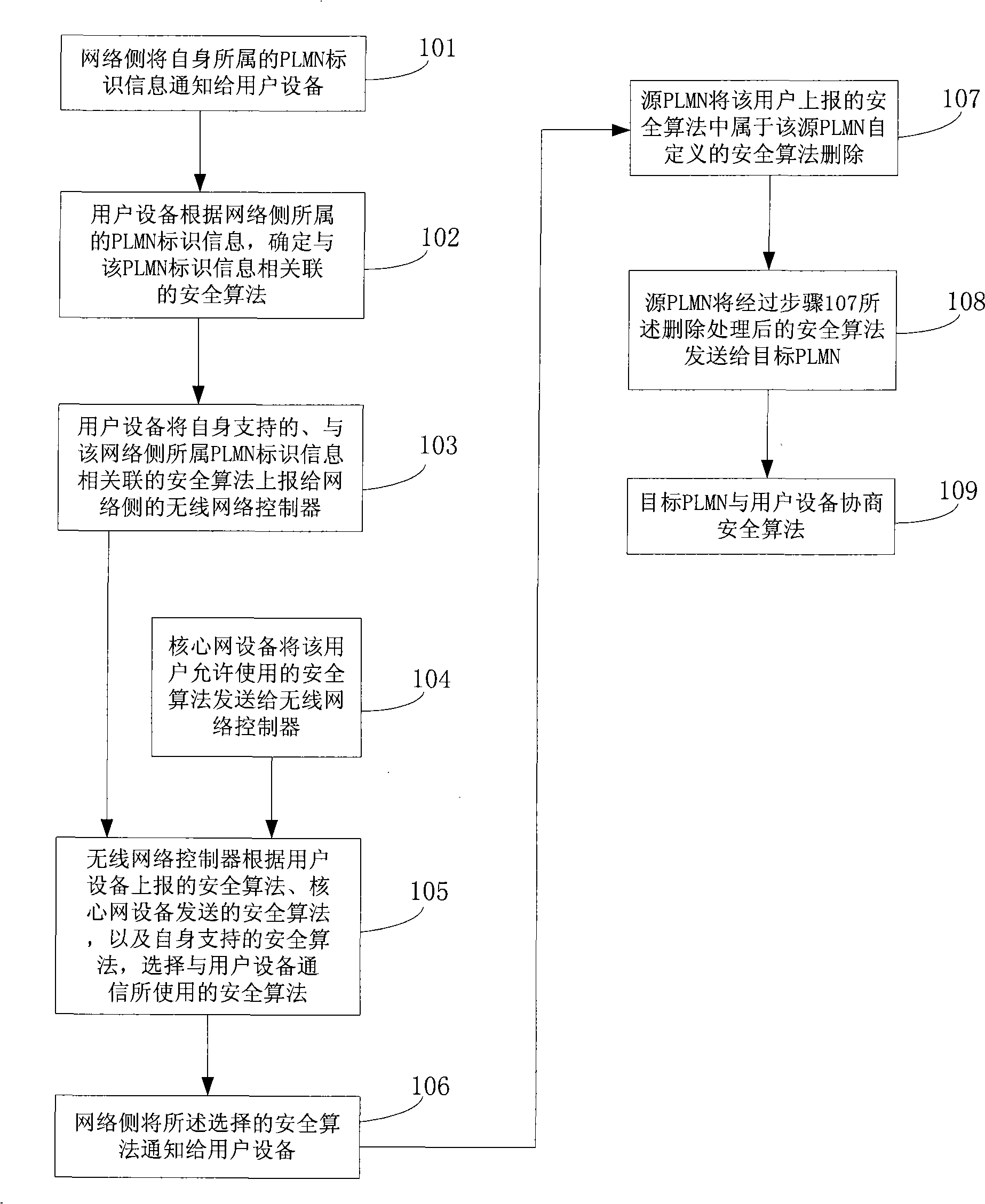
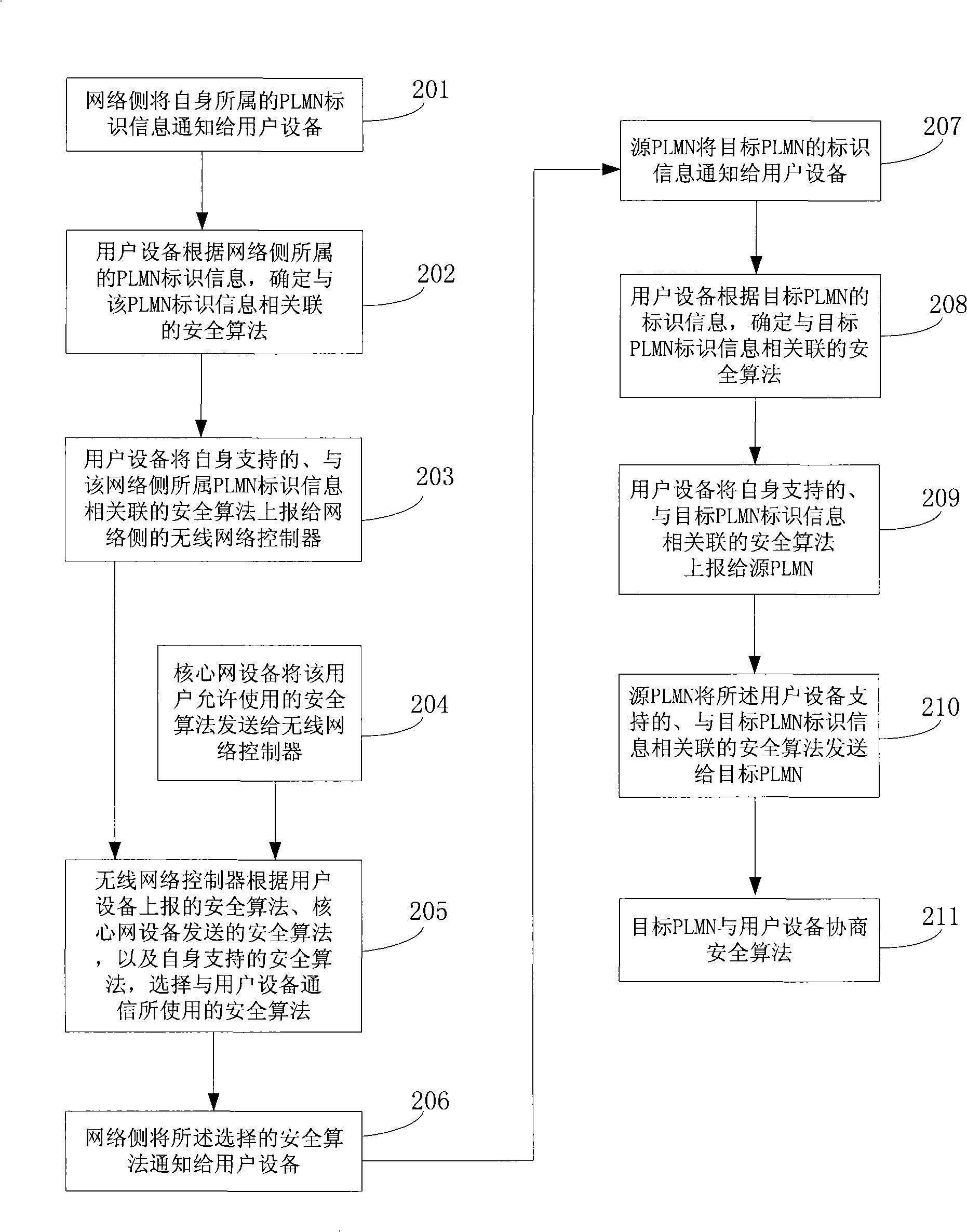
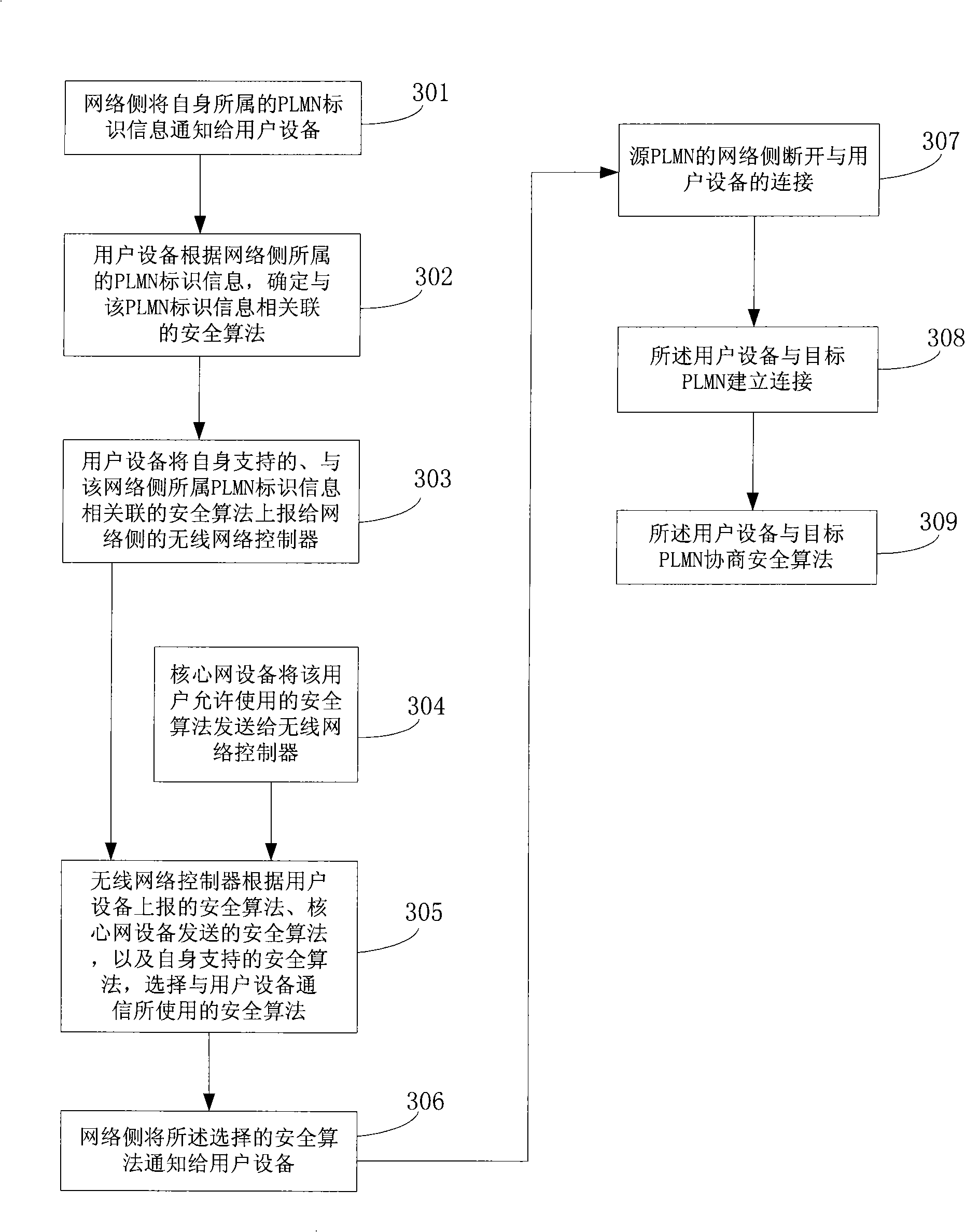
[0030] In order to realize the technical problems raised in the background art and enable operators to adopt self-defined security algorithms, the embodiments of the present invention provide a security algorithm negotiation method. The method includes:
[0031] The network side obtains a security algorithm supported by the user equipment and associated with the identification information of the PLMN to which the network side belongs;
[0032] The network side selects the security algorithm used for communicating with the user equipment according to the security algorithm supported by the user equipment and associated with the identification information of the PLMN to which the network side belongs, and the security algorithm supported by the network side itself;
[0033] The network side notifies the user equipment of the selected security algorithm.
[0034] In the above embodiments, by associating the security algorithm with the identification information of the PLMN, diff...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com