Intrude detection method and device
一种入侵检测、待检测的技术,应用在数字传输系统、电气元件、传输系统等方向,能够解决入侵检测效率低、网络攻击事件不存在、入侵检测装置单元化程度差等问题,达到提高入侵检测效率、降低维护升级费用、精确入侵检测的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
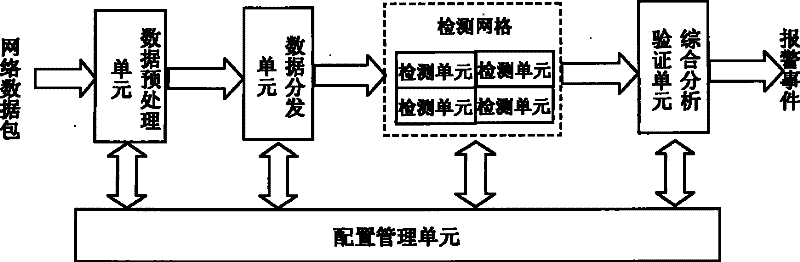
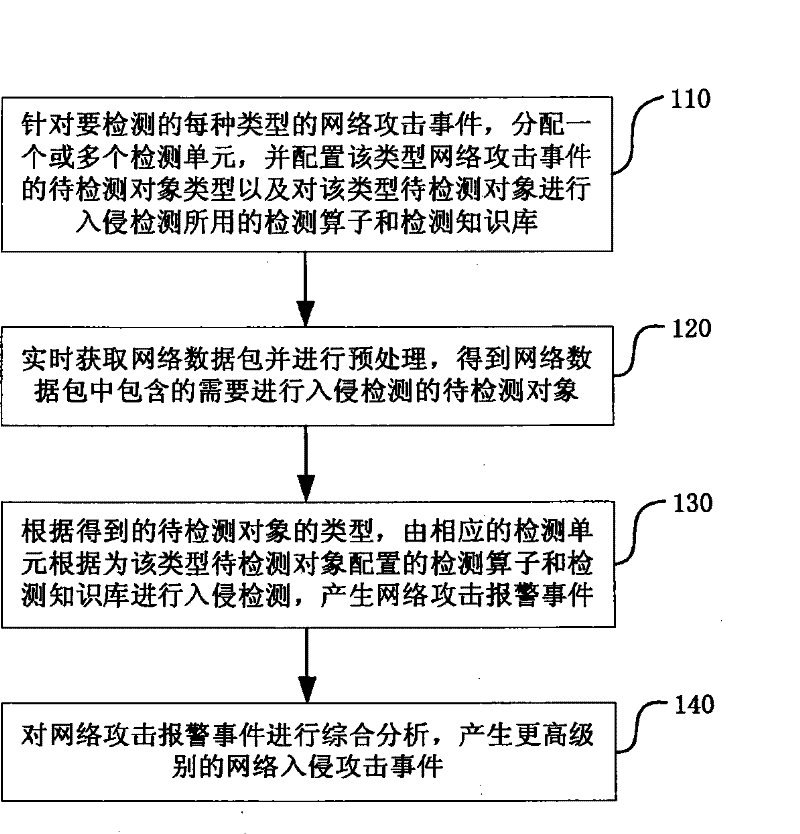
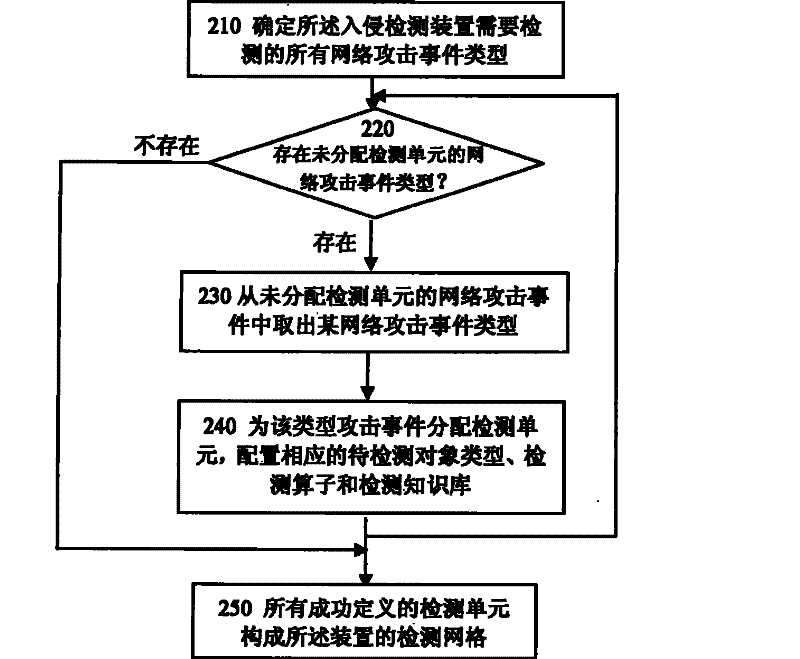
[0054] The intrusion detection method and device of the present invention no longer adopts the intrusion detection idea of using a single attack feature description format and a single attack feature matching algorithm in the traditional intrusion detection technology, but adopts a layered divide-and-conquer strategy intrusion detection idea, allowing different types of network attacks Events use different detection knowledge base description formats and select different attack detection operators to improve the detection accuracy and execution efficiency of the intrusion detection device.
[0055] Below, some nouns used in the present invention will be explained first.
[0056] The object to be detected may be an application protocol message or a file stream object, where the application layer protocol message may be an HTTP request message, and the file stream object may be an HTML document object.
[0057] The detection operator is a software program designed to detect a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com