File management system and method, and mobile terminal
A file management system and a portable terminal technology, applied in the field of portable terminal devices, can solve problems such as inability to extract information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
[0047] (1) Structure of data management system
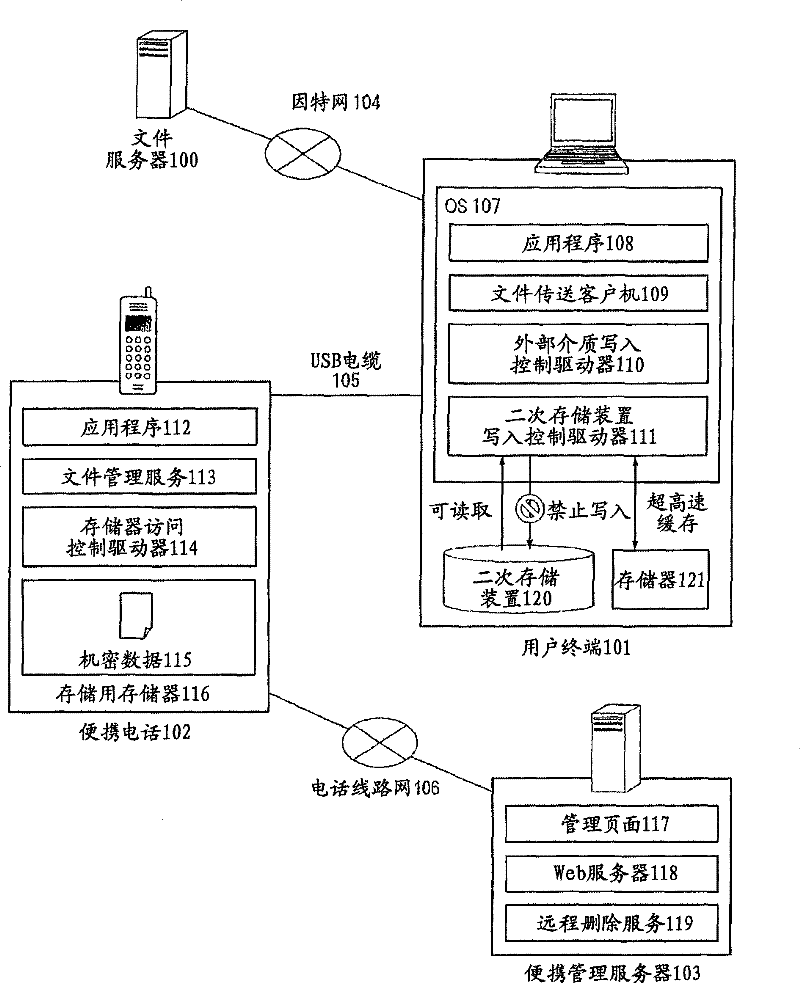
[0048] figure 1 It is a figure which shows the schematic structure of the data management system of 1st Embodiment of this invention. Such as figure 1 As shown, the data management system has a file server 100, a user terminal 101, a mobile phone (not limited to a mobile phone, but also a portable terminal such as a PDA with a communication function) 102, and a mobile management server 103. In addition, the file server 100 and the user terminal 101 can communicate via the Internet 104 , and the mobile phone 102 and the mobile management server 103 can communicate via the wireless telephone line network 106 .
[0049] In an environment where the Internet 104 is available, the user terminal 101 can manage confidential data by communicating with the file server 100, but in an environment where the Internet 104 is not available, the mobile phone 102 can manage confidential data. Since confidential data can be managed by a mobile ...
no. 2 approach
[0070] (1) Structure of data management system
[0071] Figure 6 It is a figure which shows the schematic structure of the data management system of 2nd Embodiment of this invention. The second embodiment relates to a confidential data management method using an existing PC. Therefore, although the security level is lower than that of the first embodiment, it is more convenient to use than the first embodiment. In addition, in this embodiment, trust in the user is assumed.
[0072]In the data management system of this embodiment, the difference from the first embodiment is that the user terminal 600 is an existing PC, and writing control to the secondary storage device 608 or to an external storage medium is not performed.
[0073] Such as Figure 6 As shown, the data management system has a user terminal 600 , a mobile phone (not limited to a mobile phone, but also a portable terminal such as a PDA with a communication function) 601 and a mobile management server 602 . ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com