Computer system and safety powering method
A computer system and security technology, applied in computer security devices, electrical digital data processing, instruments, etc., can solve problems such as stealing data, and achieve the effect of protecting privacy, protecting security, and complete use rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
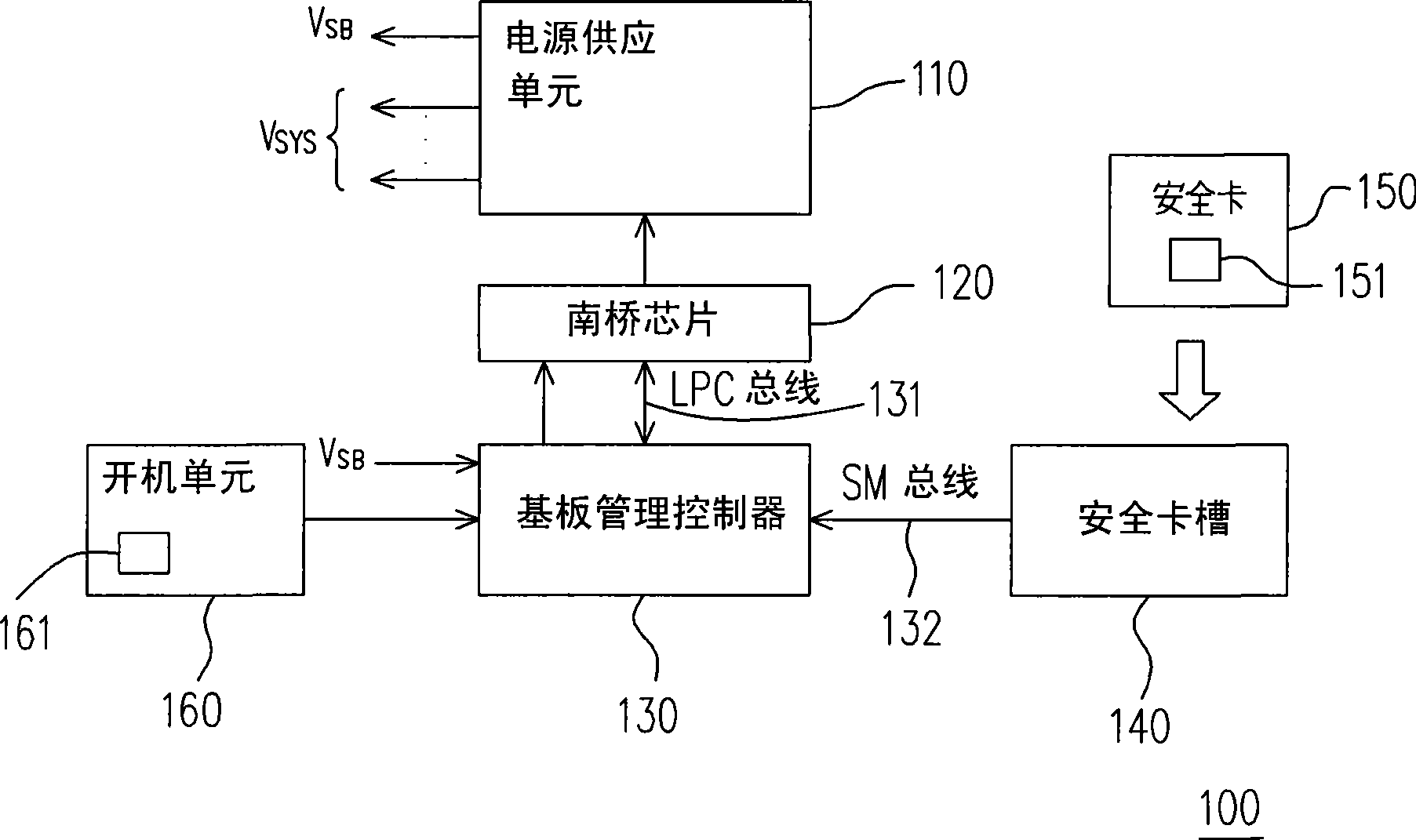
[0034] figure 1 Illustrated as a computer system 100 according to an embodiment of the present invention, including a power supply unit 110, a south bridge chip 120, a baseboard management controller (Baseboard Management Controller, BMC) 130, a security card slot 140, a security card 150 and Boot unit 160 . Wherein the power supply unit 110 supplies the standby power V SB with system supply V SYS Give the computer system 100. System Power V SYS It can supply the power required by each component inside the computer system 100 for normal operation.
[0035] In this embodiment, the power supply unit 110 is controlled by the south bridge chip 120 . When the south bridge chip 120 receives the second power-on signal sent by the baseboard management controller 130, the south bridge chip 120 will output a power-on signal to the power supply unit 110, so that the power supply unit 110 can supply the system power V SYS Give the computer system 100.
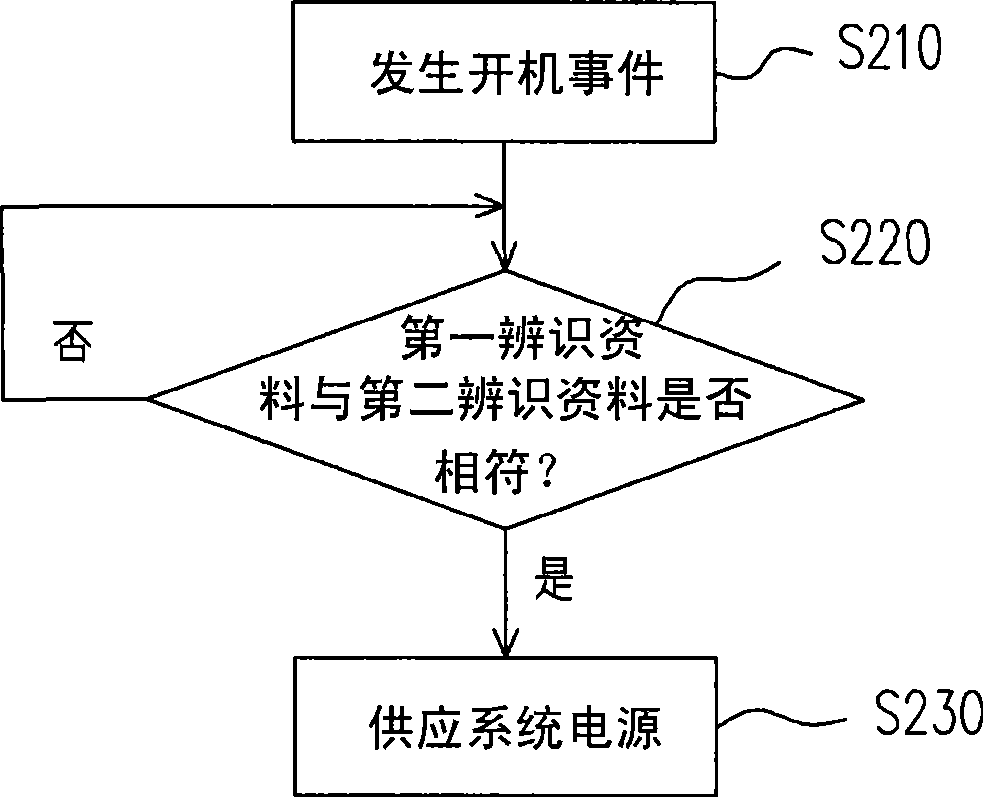
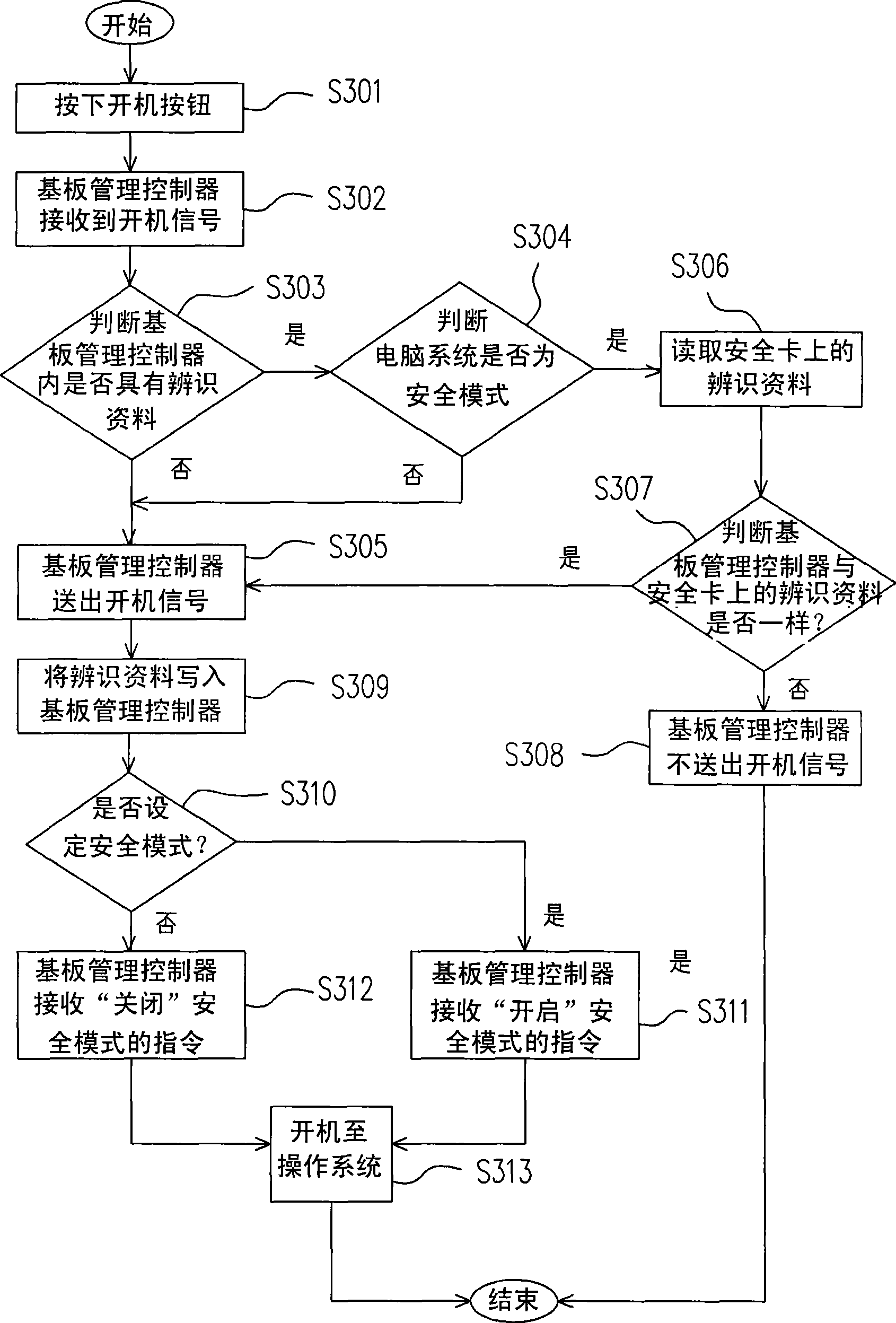
[0036] The baseboard managem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com