Method for securing special line user access network
A user and private line technology, applied in the network field, can solve the problems of heavy configuration workload, easy IP address theft, difficult management, etc., to achieve the effect of avoiding theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Below according to accompanying drawing and embodiment the present invention will be described in further detail:
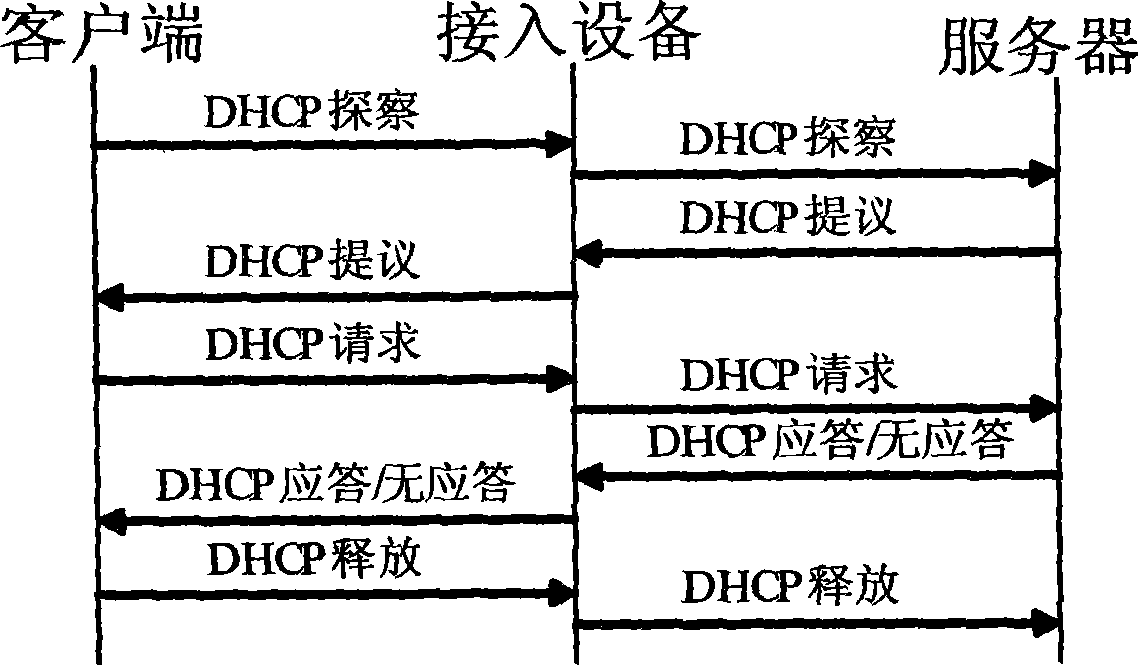
[0035] Many options are defined in the DHCP protocol, one of which is Option82, such as figure 1 As shown, two sub-options, Circuit ID Sub-option (ie CID) and Remote ID Sub-option (ie RID), are defined, where:
[0036] CID is the link identifier, which is generally used to identify the user's access location information (local information);
[0037] The RID is a remote identifier, which is generally used to identify attribute information (global information) of a device.
[0038] The general process of the DHCP protocol is as follows: figure 2 As shown, a DHCPDiscovery (discovery) message sent by the user indicates the beginning of a user dynamically obtaining an address, and a DHCPACK (response) message returned by the server indicates the end of a successful address acquisition.
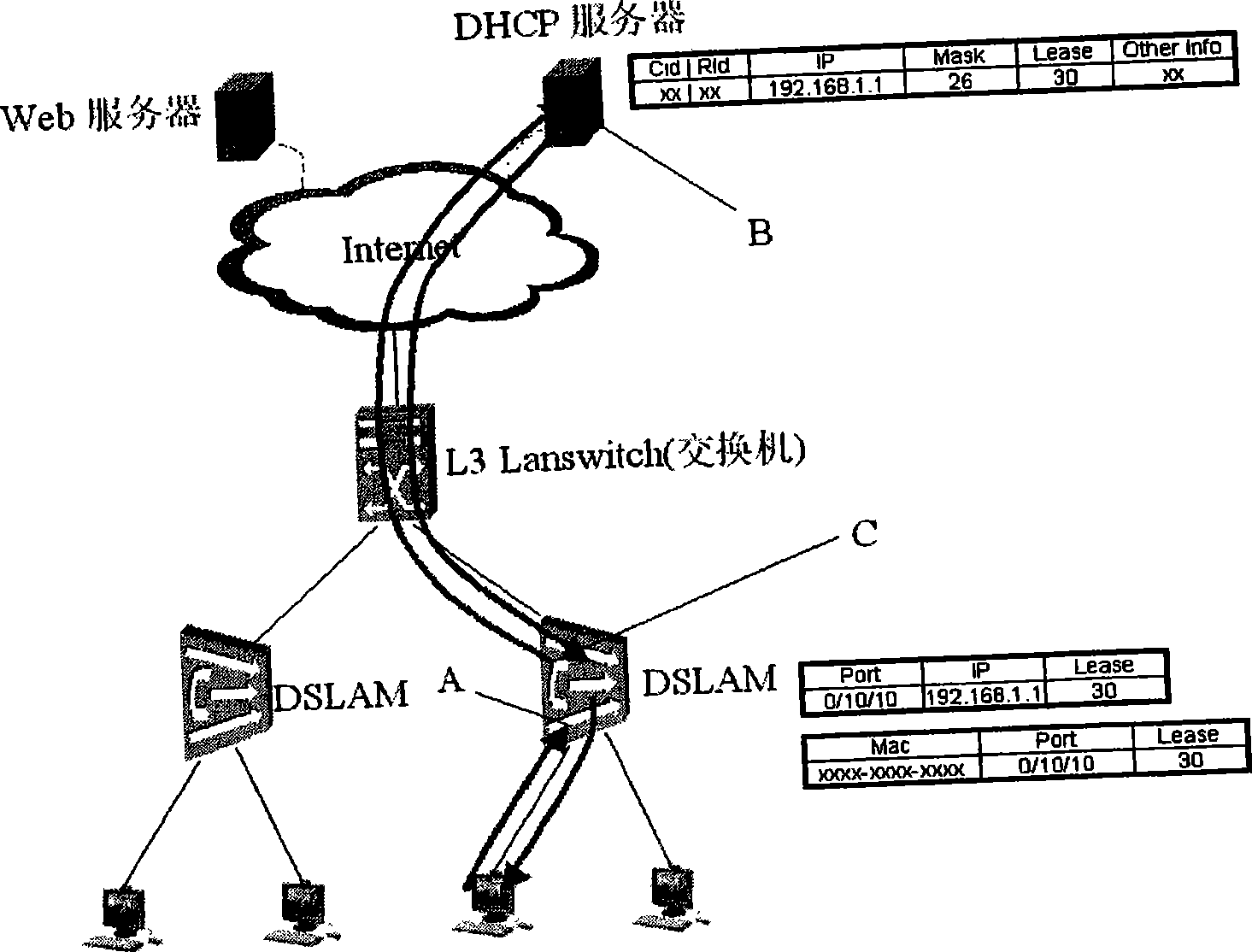
[0039] The access device (such as DSLAM) of the present invention capt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com