Method, equipment and system for updating group cipher key
A technology of group key and root key, applied in the field of communication, can solve the problems of adjusting the security policy of users, increasing the threat of attackers guessing the real identity of users, etc., to achieve the effect of reducing the threat
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
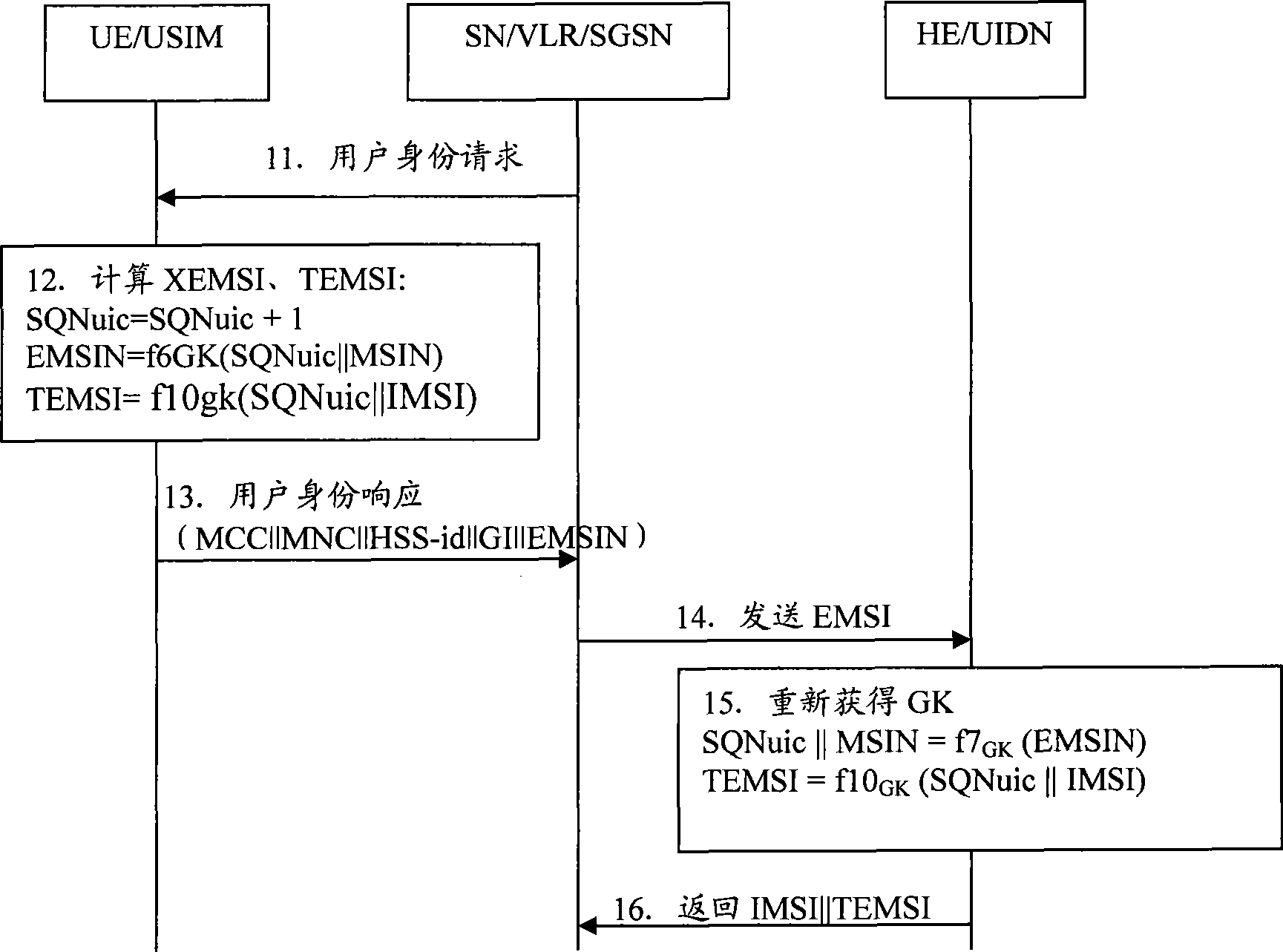
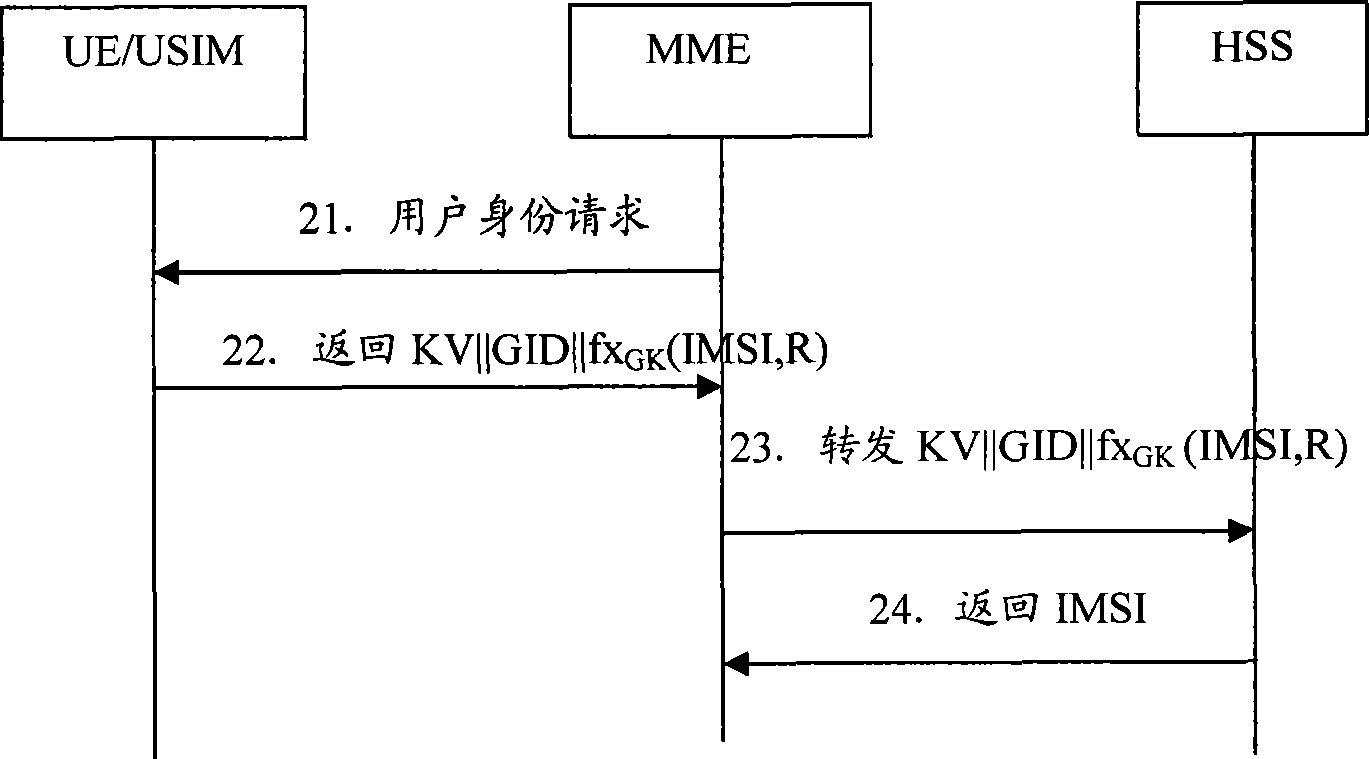
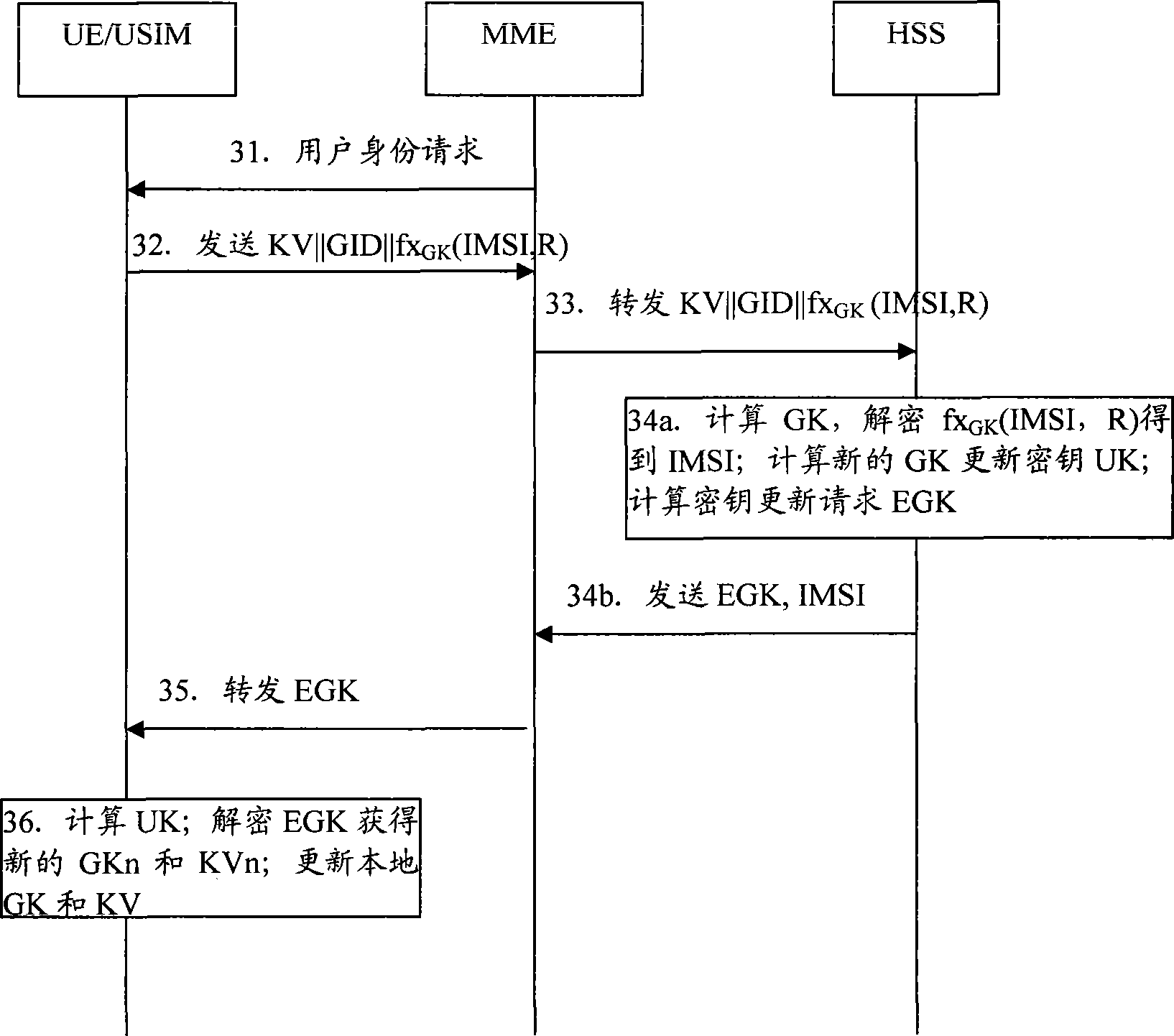
[0066] In the embodiment of the present invention, all users under the jurisdiction of the home network entity (HSS or HLR, HSS is taken as an example in this embodiment, and the processing procedure of HLR is similar to HSS) are randomly divided into different groups, and each group is represented by GID (Group ID) is uniquely identified, and the number of users in each group can be configured according to the security policy of HSS. Users in the group share a group key GK with the HSS, which is used for encryption protection of IMSI.
[0067] In the embodiment of the present invention, the parameters or functions used mainly include:
[0068] SK GID , the local root key of the HSS, used to deduce the group key GK. SK GID It is the core secret of the group, storage and GK deduction SK GID The process is carried out in HSS.
[0069] KV (64bit), t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com