Protocol identification control method and equipment based on application behavior mode
A protocol identification and control method technology, applied in the field of communication, can solve the problems of unable to realize network application flow control, unable to identify efficiently and so on.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
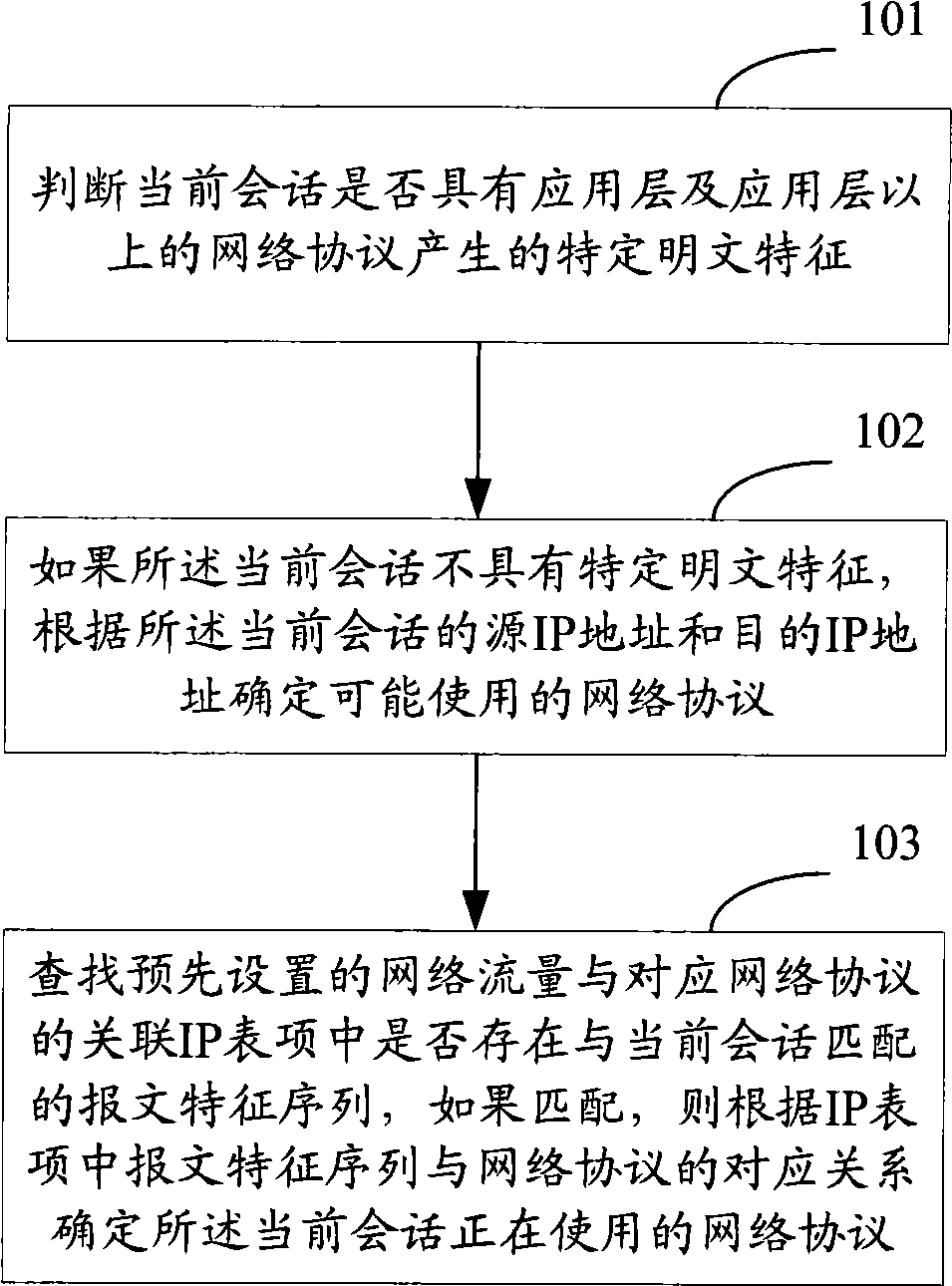
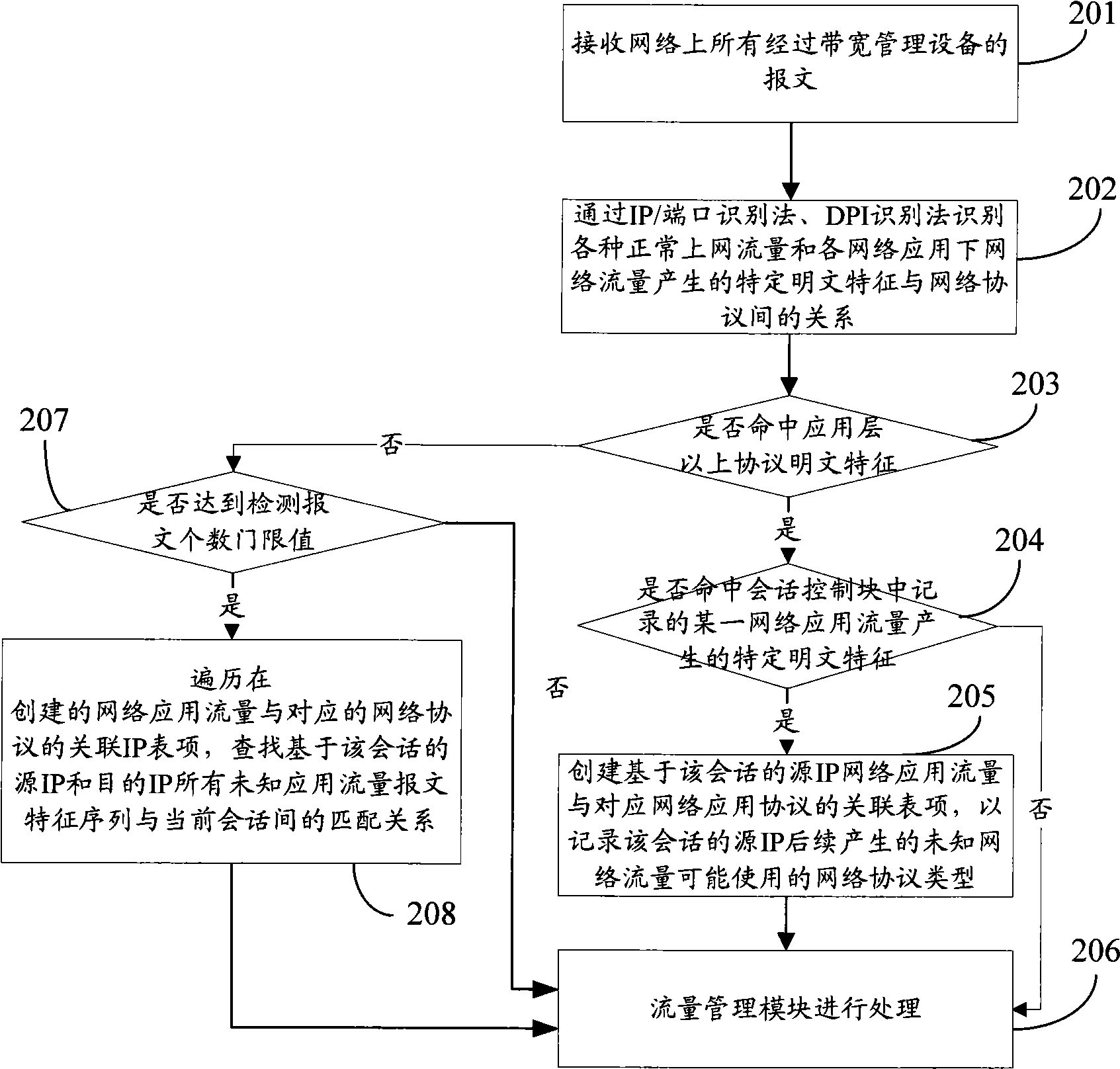
[0033] The core idea of the present invention is: for all sessions passing through the bandwidth management device, after using the IP / port identification method and the DPI identification method to detect the specified number of messages, the traffic type cannot be correctly identified, and the query based on the IP is created. The associated table entry between network traffic and the corresponding network protocol traverses the packet feature sequence corresponding to all possible network traffic used by the source IP address and destination IP address of the current session, and uses the packet feature sequence corresponding to each network traffic in the current session to perform If the current session completely matches a certain packet signature sequence, it is considered that the current session is using the network protocol corresponding to the packet signature sequence.
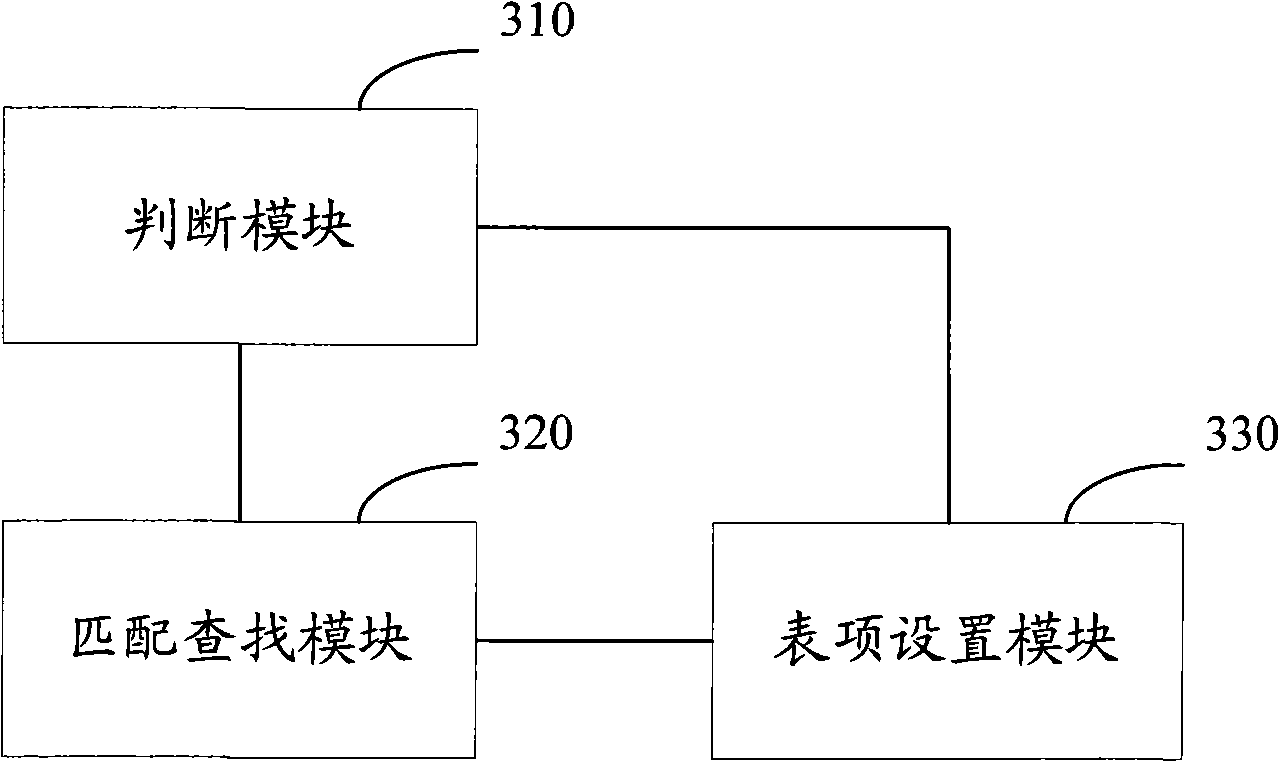
[0034] The present invention provides a protocol identification control method based on an app...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com